Switch On, Update, Lose Evidence
The focus of this article relates to what can happen when switching on a mobile telephone and how data can change on a SIM Card. Essentially how a mobile telephone updates a SIM card relating to location data is down to how each make and model of mobile telephone has been programmed. When dealing with location data in SIM Cards it should not be assumed that every make/model updates location data immediately or within a prescribed period. Certain events trigger location update data and therefore it is important to determine on a case by case basis how a mobile telephone and its SIM card should be examined.
I have received several comments from different sources saying that they found location data was not updated when the mobile telephone was held within a shielded device or bag. This is fine, but it has been found that data can change in such environments and it is not the case that it was only a few times, but the fact that it happened at all can mean unilaterally ignoring that such an event (loss of data) might occur may mean losing vital evidence.
A best practise methodology has been outlined in the article for those that wish to follow it and the justification for using such a stated methodology.
http://www.filebucket.net/files/1579_ov3rx/Switch%20On%20Update%20Lose%20Evidence%20.pdf
Investigations, Practices and Procedures: Seizure-Forensic Examination-Evidence. Cellular and Satellite Telephones, Call Records-Billing Data, Cell Site Analysis. Telecomms. Computer and Network Analysis. GPS devices & Jammers, Cyber, IoT forensics.
Wednesday, November 29, 2006
Switch On, Update, Lose Evidence
Switch On, Update, Lose Evidence
The focus of this article relates to what can happen when switching on a mobile telephone and how data can change on a SIM Card. Essentially how a mobile telephone updates a SIM card relating to location data is down to how each make and model of mobile telephone has been programmed. When dealing with location data in SIM Cards it should not be assumed that every make/model updates location data immediately or within a prescribed period. Certain events trigger location update data and therefore it is important to determine on a case by case basis how a mobile telephone and its SIM card should be examined.
I have received several comments from different sources saying that they found location data was not updated when the mobile telephone was held within a shielded device or bag. This is fine, but it has been found that data can change in such environments and it is not the case that it was only a few times, but the fact that it happened at all can mean unilaterally ignoring that such an event (loss of data) might occur may mean losing vital evidence.
A best practise methodology has been outlined in the article for those that wish to follow it and the justification for using such a stated methodology.
http://www.filebucket.net/files/1579_ov3rx/Switch%20On%20Update%20Lose%20Evidence%20.pdf
The focus of this article relates to what can happen when switching on a mobile telephone and how data can change on a SIM Card. Essentially how a mobile telephone updates a SIM card relating to location data is down to how each make and model of mobile telephone has been programmed. When dealing with location data in SIM Cards it should not be assumed that every make/model updates location data immediately or within a prescribed period. Certain events trigger location update data and therefore it is important to determine on a case by case basis how a mobile telephone and its SIM card should be examined.
I have received several comments from different sources saying that they found location data was not updated when the mobile telephone was held within a shielded device or bag. This is fine, but it has been found that data can change in such environments and it is not the case that it was only a few times, but the fact that it happened at all can mean unilaterally ignoring that such an event (loss of data) might occur may mean losing vital evidence.
A best practise methodology has been outlined in the article for those that wish to follow it and the justification for using such a stated methodology.
http://www.filebucket.net/files/1579_ov3rx/Switch%20On%20Update%20Lose%20Evidence%20.pdf
Deleted Data Mobiles
This article generally looked at how data that are deleted and that might be subsequently recovered and used as evidence may be viewed following the case of R .v. Porter.
http://system7428.files-upload.com/393504/DeleteddataMobiles.rar.html
http://system7428.files-upload.com/393504/DeleteddataMobiles.rar.html
Tuesday, November 28, 2006
Cell Site Analysis Part 1
Cell Site Analysis Part 1
Part 1 Introduction to Cell Site Analysis
http://www.filebucket.net/files/1557_srkzn/Cell%20Site%20Analysis%20Pt1.pdf
Part 1 Introduction to Cell Site Analysis
http://www.filebucket.net/files/1557_srkzn/Cell%20Site%20Analysis%20Pt1.pdf
Samsung Toolbox
Samsung Toolbox

Tests over 17 different models of Samsung Mobile Phones - models: A800, A1xx, T108, N628, N625, N620, N611, N600, N500, N400, N300, N2xx, N1xx, R225, R210, R208, R200,
Features: WinTracer, E2P Manager, Downloader, H/W Tester, Remote Key, Camera Tester, Flash Dump, Environment Tester.
http://system7428.files-upload.com/380870/ToolBox5NewMMI.zip.html

Tests over 17 different models of Samsung Mobile Phones - models: A800, A1xx, T108, N628, N625, N620, N611, N600, N500, N400, N300, N2xx, N1xx, R225, R210, R208, R200,
Features: WinTracer, E2P Manager, Downloader, H/W Tester, Remote Key, Camera Tester, Flash Dump, Environment Tester.
http://system7428.files-upload.com/380870/ToolBox5NewMMI.zip.html
Monday, November 27, 2006
SonyEricsson Explorer
SonyEricsson Explorer

Found this nice little SonyEricsson handset software.
Handset/SIM Contacts:
-Name
-Home
-Mobile
-Email
- Calls: see all or separately dialled, answered, missed
- Orangiser: calendar and alarms
- SMS Messages: inbox, drafts, sent items, saved items, archive
-Files (obex)
-Others: profiles, monitor (battery etc), memory status (handset & SIM)
http://filebucket.org/files/7017_xsd3x/k600i%20MyPhoneExplorer_Setup_1.5.2.exe

Found this nice little SonyEricsson handset software.
Handset/SIM Contacts:
-Name
-Home
-Mobile
- Calls: see all or separately dialled, answered, missed
- Orangiser: calendar and alarms
- SMS Messages: inbox, drafts, sent items, saved items, archive
-Files (obex)
-Others: profiles, monitor (battery etc), memory status (handset & SIM)
http://filebucket.org/files/7017_xsd3x/k600i%20MyPhoneExplorer_Setup_1.5.2.exe
Sunday, November 26, 2006
Phone Tap Data as evidence
Interesting article in The Independent Online newspaper, headed "Reid wary of phone tap data as evidence."
http://news.independent.co.uk/uk/politics/article2010026.ece
http://news.independent.co.uk/uk/politics/article2010026.ece
Thursday, November 23, 2006
Build your own mobile phone
Build your own mobile phone
Don't you just love it. Building your own mobile phone is now becoming a popular hobbyist event. In fact, it isn't as difficult as may be imagined. Why is it good for forensic... a unique fingerprint of activity, of course.

Credit to the Tuxphone guys putting this together. Couldn't see the point though of buying surplus components when you can pick up second-hand handsets dirt cheap...and rip them apart.
Don't you just love it. Building your own mobile phone is now becoming a popular hobbyist event. In fact, it isn't as difficult as may be imagined. Why is it good for forensic... a unique fingerprint of activity, of course.

Credit to the Tuxphone guys putting this together. Couldn't see the point though of buying surplus components when you can pick up second-hand handsets dirt cheap...and rip them apart.
Mobile Phone Vouchers
Interesting November 2005 newsfeed. Not sure whether this is a compliment to mobile phones grip in the maketplace or an insult indicating that mobile phones are a desperate, last resort.
Azahari's group 'selling phone cards' to survive
A terrorist group once led by master bombmaker Azahari Husin is struggling for funds and now depends on selling mobile phone vouchers to get by, Indonesia's police chief said on Monday.
http://www.abc.net.au/news/newsitems/200511/s1513116.htm
Azahari's group 'selling phone cards' to survive
A terrorist group once led by master bombmaker Azahari Husin is struggling for funds and now depends on selling mobile phone vouchers to get by, Indonesia's police chief said on Monday.
http://www.abc.net.au/news/newsitems/200511/s1513116.htm
Disappearing SMS Text Messages
Disappearing SMS Text Messages
SMS (short message service) text messages are convienent way to communicate and the amount of texts sent each year runs into billions, proving that this service in the wireless world of mobile telephones is highly popular.
There are a number of classes of SMS messages, but the class of message relevant to this discussion is "Class 0 (flash message)", which can add difficulties to an examiner's investigation and evidence. Text messages that are stored and then deleted can be recovered, provided they have not been overwritten.
Flash messages though are a different beast altogether, because when sent the recipient sees the message on the handset screen without the message having been lodged at first instance in the handset inbox or SIM (ef) 7F106F42.
A simple constructed message and assignment can be:
[Flash] [Recipient Number] [Message]
The flash message once received can be deleted from the screen or made to disappear from the screen and it is possible to generate messages in such away that any content of importance may not be recoverable.
SMS (short message service) text messages are convienent way to communicate and the amount of texts sent each year runs into billions, proving that this service in the wireless world of mobile telephones is highly popular.
There are a number of classes of SMS messages, but the class of message relevant to this discussion is "Class 0 (flash message)", which can add difficulties to an examiner's investigation and evidence. Text messages that are stored and then deleted can be recovered, provided they have not been overwritten.
Flash messages though are a different beast altogether, because when sent the recipient sees the message on the handset screen without the message having been lodged at first instance in the handset inbox or SIM (ef) 7F106F42.
A simple constructed message and assignment can be:
[Flash] [Recipient Number] [Message]
The flash message once received can be deleted from the screen or made to disappear from the screen and it is possible to generate messages in such away that any content of importance may not be recoverable.
Disappearing SMS Text Messages
Disappearing SMS Text Messages
SMS (short message service) text messages are convienent way to communicate and the amount of texts sent each year runs into billions, proving that this service in the wireless world of mobile telephones is highly popular.
There are a number of classes of SMS messages, but the class of message relevant to this discussion is "Class 0 (flash message)", which can add difficulties to an examiner's investigation and evidence. Text messages that are stored and then deleted can be recovered, provided they have not been overwritten.
Flash messages though are a different beast altogether, because when sent the recipient sees the message on the handset screen without the message having been lodged at first instance in the handset inbox or SIM (ef) 7F106F42.
A simple constructed message and assignment can be:
[Flash] [Recipient Number] [Message]
The flash message once received can be deleted from the screen or made to disappear from the screen and it is possible to generate messages in such away that any content of importance may not be recoverable.
SMS (short message service) text messages are convienent way to communicate and the amount of texts sent each year runs into billions, proving that this service in the wireless world of mobile telephones is highly popular.
There are a number of classes of SMS messages, but the class of message relevant to this discussion is "Class 0 (flash message)", which can add difficulties to an examiner's investigation and evidence. Text messages that are stored and then deleted can be recovered, provided they have not been overwritten.
Flash messages though are a different beast altogether, because when sent the recipient sees the message on the handset screen without the message having been lodged at first instance in the handset inbox or SIM (ef) 7F106F42.
A simple constructed message and assignment can be:
[Flash] [Recipient Number] [Message]
The flash message once received can be deleted from the screen or made to disappear from the screen and it is possible to generate messages in such away that any content of importance may not be recoverable.
Tuesday, November 21, 2006
Seizure Procedure s19 PACE 1984
Seizure Procedure s19 PACE 1984
By the end of this month I aim to have completed the updated Mobile Telephone Seizure Procedure in accordance with Section 19 of the Police and Criminal Evidence 1984. The document was originally put together for the TrewMTE mobile telephone evidence training courses six years ago and has largely been used as a reference source to consider when examining Seizure Procedure to comprehend, from a practitioner's viewpoint, elements involved regarding best endeavours to secure mobile 'phone exhibits for later examination.
The work involved is undertaken and sponsored by TrewMTE does not receive any public funding.
By the end of this month I aim to have completed the updated Mobile Telephone Seizure Procedure in accordance with Section 19 of the Police and Criminal Evidence 1984. The document was originally put together for the TrewMTE mobile telephone evidence training courses six years ago and has largely been used as a reference source to consider when examining Seizure Procedure to comprehend, from a practitioner's viewpoint, elements involved regarding best endeavours to secure mobile 'phone exhibits for later examination.
The work involved is undertaken and sponsored by TrewMTE does not receive any public funding.
Monday, November 20, 2006
Mobile Telephone Forensics
Mobile Telephone Forensics
Mobile telephones are small devices and commonly, due to misunderstanding and lack of appreciation of the brilliant work that goes into making a mobile telephone and SIM Card operate, are relegated to a lower standard of investigation. Yet, with mobile telephones primary radio capability, with solid-state electronics to back it up, enables them to punch, pound for pound, way above their weight when measured in terms of multifunctional computers or laptops.
This makes mobile telephone forensics an exciting branch of forensic science, but it does mean taking time and a dedication to comprehend. Consider the wireless and connectivity of a mobile telephone and it may surprise many what is incorporated into these mobile devices.
We commonly think of mobiles defined by their wireless service they use, such as GSM GPRS 3G etc, which are of course very important to mobile 'phone forensics. However, behind that sits a myriad of connectivity from which data can be generated and provide equally importance evidence. A footprint, if you will, that needs to be considered. For instance, what impact it has in relation to how data got to be there, what affect and effect it has regarding evidence and whether the proposition of what the evidence means can be correlated to the connectivity in question.
If SMS text messages were the only evidence to be considered then it would be understandable that connectivity would be rather a moot point. But given the fact mobile telephones have come on leaps and bounds with the introduction of Symbian based systems and java technology etc isolating SMS text messages is no longer an option. EMS and MMS play an important part in evidence, as do emails, videos etc. Indeed, transporting data wirelessly between devices through close-range communications equally means that connectivity cannot be ignored within the forensic investigation. The possible paths how data are populated in mobile device requires identification, in order to be able to comprehend the overall picture how the devices have or can be used.
- WAP 1.0, 2.0
- Bluetooth v.1.0, v.2.0
- GPRS class 10 EGPRS (Class B, Multislot class 11)
- E-mail protocols: SMTP, POP3, IMAP4 - attachments
- MMS
- Synchronization via Bluetooth or a cable SyncML
- SMIL
- USB 1.0, 2.0 via Pop-Port
- PoC or PTT
- Instant Messaging
- VideoCall
- WiFi (WLAN)
Above are just some of the connectivity technologies in use today in mobile telephones. Look, comprehend and consider is the name of the game with mobile 'phone forensics. For each heading shown above, each has its own subset standards and guidelines. It is not difficult to see why mobile telephones are very smart phones indeed.
Mobile telephones are small devices and commonly, due to misunderstanding and lack of appreciation of the brilliant work that goes into making a mobile telephone and SIM Card operate, are relegated to a lower standard of investigation. Yet, with mobile telephones primary radio capability, with solid-state electronics to back it up, enables them to punch, pound for pound, way above their weight when measured in terms of multifunctional computers or laptops.
This makes mobile telephone forensics an exciting branch of forensic science, but it does mean taking time and a dedication to comprehend. Consider the wireless and connectivity of a mobile telephone and it may surprise many what is incorporated into these mobile devices.
We commonly think of mobiles defined by their wireless service they use, such as GSM GPRS 3G etc, which are of course very important to mobile 'phone forensics. However, behind that sits a myriad of connectivity from which data can be generated and provide equally importance evidence. A footprint, if you will, that needs to be considered. For instance, what impact it has in relation to how data got to be there, what affect and effect it has regarding evidence and whether the proposition of what the evidence means can be correlated to the connectivity in question.
If SMS text messages were the only evidence to be considered then it would be understandable that connectivity would be rather a moot point. But given the fact mobile telephones have come on leaps and bounds with the introduction of Symbian based systems and java technology etc isolating SMS text messages is no longer an option. EMS and MMS play an important part in evidence, as do emails, videos etc. Indeed, transporting data wirelessly between devices through close-range communications equally means that connectivity cannot be ignored within the forensic investigation. The possible paths how data are populated in mobile device requires identification, in order to be able to comprehend the overall picture how the devices have or can be used.
- WAP 1.0, 2.0
- Bluetooth v.1.0, v.2.0
- GPRS class 10 EGPRS (Class B, Multislot class 11)
- E-mail protocols: SMTP, POP3, IMAP4 - attachments
- MMS
- Synchronization via Bluetooth or a cable SyncML
- SMIL
- USB 1.0, 2.0 via Pop-Port
- PoC or PTT
- Instant Messaging
- VideoCall
- WiFi (WLAN)
Above are just some of the connectivity technologies in use today in mobile telephones. Look, comprehend and consider is the name of the game with mobile 'phone forensics. For each heading shown above, each has its own subset standards and guidelines. It is not difficult to see why mobile telephones are very smart phones indeed.
Saturday, November 18, 2006
Motorla A1000
Motorola A1000
A problem that has been noted with the A1000 is that the handset itself can bounce into auto reset and lose data: images, SMS, contacts, videos etc are wiped from the handset memory. One cause for to this problem - where the handset has been re-charged and leaving the charger switched ON and booting up the handset can cause this to happen. It is an intermittent fault apparently.
Another is, attempting to back-up data by transferring data to a computer it has been noted an error message can occur stating:
"Backup Error: Failed to analyse differences between the handset and the PC (0x8000ffff)"
loss of data on some handsets has been noted.
Re-flashing the handsets may solve these problems (but the previously stored data following both instances above might be lost). This doesn't assist the examiner though if these events occur whilst examining an exhibit.
Remember to note it down, that where a device under test (DUT) is known to have problems to refer to the known problems in examination notes.
A problem that has been noted with the A1000 is that the handset itself can bounce into auto reset and lose data: images, SMS, contacts, videos etc are wiped from the handset memory. One cause for to this problem - where the handset has been re-charged and leaving the charger switched ON and booting up the handset can cause this to happen. It is an intermittent fault apparently.
Another is, attempting to back-up data by transferring data to a computer it has been noted an error message can occur stating:
"Backup Error: Failed to analyse differences between the handset and the PC (0x8000ffff)"
loss of data on some handsets has been noted.
Re-flashing the handsets may solve these problems (but the previously stored data following both instances above might be lost). This doesn't assist the examiner though if these events occur whilst examining an exhibit.
Remember to note it down, that where a device under test (DUT) is known to have problems to refer to the known problems in examination notes.
Friday, November 17, 2006
Nokia 6280 Black Out
Nokia 6280 Black Out
There appears to be a problem that can occur with some Nokia 6280. I am not the first to notice this. When SMS or MMS memories are full or scrolling the Menu the handset suddenly blacks out. For an examiner this can imply the examination has somehow gone wrong, causing blood pressure to rise and an increase pulse and heart rate. It appears to be a fault with some (I hasten to add, not all) 6280 handsets and therefore it is suggested you note it down in your contemporaneous examination notes for mobile telephone evidence.
Do remember for evidential purposes, in fairness not only to the Judge and Court, prosecution and defence, do remember to identify the offending device for the purposes of "originality and genuineness":
A) Man-Machine Interface Code *#06# (compliant with GSM02:30 Presentation of IMEI)
B) Handset Software Code *#0000# (manufacturer specific code)
C) Warranty Code *#92702689# (manufacturer specific code)
Send an email to me TrewMTE@gmail.com (do not send the IMEI - handset serial number) and I will happily publish the list here of handsets found to have this problem.
There appears to be a problem that can occur with some Nokia 6280. I am not the first to notice this. When SMS or MMS memories are full or scrolling the Menu the handset suddenly blacks out. For an examiner this can imply the examination has somehow gone wrong, causing blood pressure to rise and an increase pulse and heart rate. It appears to be a fault with some (I hasten to add, not all) 6280 handsets and therefore it is suggested you note it down in your contemporaneous examination notes for mobile telephone evidence.
Do remember for evidential purposes, in fairness not only to the Judge and Court, prosecution and defence, do remember to identify the offending device for the purposes of "originality and genuineness":
A) Man-Machine Interface Code *#06# (compliant with GSM02:30 Presentation of IMEI)
B) Handset Software Code *#0000# (manufacturer specific code)
C) Warranty Code *#92702689# (manufacturer specific code)
Send an email to me TrewMTE@gmail.com (do not send the IMEI - handset serial number) and I will happily publish the list here of handsets found to have this problem.
Mobile Telephone Evidence - TIPS
Mobile Telephone Evidence - TIPS
Vinny Parmar sent in a couple of handset examination tips for my webblog readers. Thanks Vinny..
1. Nokia 6280 Series 40
- Handset can be powered on without the need for a SIM card. Access granted to menu's & data areas. Call log is not available. Contact list only viewable if Contact settings memory allocation changed to Phone Memory only. All other data areas accessible
2. Samsung D600:
- Memory card can be password protected via GUI. However once card removed from handset card is no longer protected - Requires further testing to confirm on all firmware versions and other models.
Vinny Parmar sent in a couple of handset examination tips for my webblog readers. Thanks Vinny..
1. Nokia 6280 Series 40
- Handset can be powered on without the need for a SIM card. Access granted to menu's & data areas. Call log is not available. Contact list only viewable if Contact settings memory allocation changed to Phone Memory only. All other data areas accessible
2. Samsung D600:
- Memory card can be password protected via GUI. However once card removed from handset card is no longer protected - Requires further testing to confirm on all firmware versions and other models.
Mobile Telephone Evidence - TIPS
Mobile Telephone Evidence - TIPS
Vinny Parmar sent in a couple of handset examination tips for my webblog readers. Thanks Vinny..
1. Nokia 6280 Series 40
- Handset can be powered on without the need for a SIM card. Access granted to menu's & data areas. Call log is not available. Contact list only viewable if Contact settings memory allocation changed to Phone Memory only. All other data areas accessible
2. Samsung D600:
- Memory card can be password protected via GUI. However once card removed from handset card is no longer protected - Requires further testing to confirm on all firmware versions and other models.
Vinny Parmar sent in a couple of handset examination tips for my webblog readers. Thanks Vinny..
1. Nokia 6280 Series 40
- Handset can be powered on without the need for a SIM card. Access granted to menu's & data areas. Call log is not available. Contact list only viewable if Contact settings memory allocation changed to Phone Memory only. All other data areas accessible
2. Samsung D600:
- Memory card can be password protected via GUI. However once card removed from handset card is no longer protected - Requires further testing to confirm on all firmware versions and other models.
Celliax Developers LiveCD 0.0.32
Celliax Developers LiveCD 0.0.32

GSM CDMA cellular driver, Skype cellphone calls support, via chan_celliax and hardware adapter. Works with Linux & WinXP
NOTICE: Before installing check any downloads for virus etc. Also read the instructions and supporting technical help links.
Here are some links:
http://www.celliax.org/downloads
http://www.celliax.org/LiveCD_0_0_32
http://knoppix.net/wiki/Knoppix_Remastering_Howto
http://www.celliax.org/LiveCD_0_0_32
http://knoppix.net/wiki/Knoppix_Remastering_Howto
Britain's Most Wanted
Britain's Most Wanted
Whilst crime is the topic of the last post, I thought it might be useful to let everyone know to look at Crimestopper's website for Britain's most wanted:
http://www.crimestoppers-uk.org/ceop/
Whilst crime is the topic of the last post, I thought it might be useful to let everyone know to look at Crimestopper's website for Britain's most wanted:
http://www.crimestoppers-uk.org/ceop/
Robbers use Camera Cell Phones
Robbers use Camera Cell Phones
According to inq7.net newsfeed following a story printed in the Philippine Daily Inquirer "ROBBERS have also gone high-tech, using cell phones equipped with cameras to spot potential victims."
Apparently, a "syndicate" that operates on the Philippine railway system take photographs of their "would-be victims" using the camera on the cell phone. The photo then gets forwarded to "accomplices" who then "stage a holdup" by positioning themselves near the "ticket booth" waiting for people to take out their wallets to pay for tickets.
"The spotter would then follow the intended victim inside the train and then call or text or send a photo of the victim to their members on the ground. When the target gets off the train, one of the robbers would drape his arm around the victim’s shoulder while another would get the contents of the victim’s bag."
According to inq7.net newsfeed following a story printed in the Philippine Daily Inquirer "ROBBERS have also gone high-tech, using cell phones equipped with cameras to spot potential victims."
Apparently, a "syndicate" that operates on the Philippine railway system take photographs of their "would-be victims" using the camera on the cell phone. The photo then gets forwarded to "accomplices" who then "stage a holdup" by positioning themselves near the "ticket booth" waiting for people to take out their wallets to pay for tickets.
"The spotter would then follow the intended victim inside the train and then call or text or send a photo of the victim to their members on the ground. When the target gets off the train, one of the robbers would drape his arm around the victim’s shoulder while another would get the contents of the victim’s bag."
Thursday, November 16, 2006
Confidential Mobile Phone Calls
Confidential Mobile Phone Calls
 No matter where you are, on the train, in a meeting or with your family at home, you can now make mobile calls with complete assurance that no one can over hear you.
No matter where you are, on the train, in a meeting or with your family at home, you can now make mobile calls with complete assurance that no one can over hear you.
This revolutionary new gadget brings charm and sophiscation, and can be worn with confidence, providing an escape from the otherwise technobland world of being heard whilst using a mobile 'phone without protection. The girls will love it !
Which reminds me, "Something for the weekend, Sir!?"
 No matter where you are, on the train, in a meeting or with your family at home, you can now make mobile calls with complete assurance that no one can over hear you.
No matter where you are, on the train, in a meeting or with your family at home, you can now make mobile calls with complete assurance that no one can over hear you.This revolutionary new gadget brings charm and sophiscation, and can be worn with confidence, providing an escape from the otherwise technobland world of being heard whilst using a mobile 'phone without protection. The girls will love it !
Which reminds me, "Something for the weekend, Sir!?"
Wednesday, November 15, 2006
Globalstar GSP-1700 Satellite Phone
Globalstar GSP-1700 Satellite Phone

Seems our common mobile 'phones will now compete with satellite 'phone for fashion and style. The new GSP-1700 from Globalstar Inc has been quite drastically reduced in size from the old-brick, clumsy satellite handset design previously available. The battery allows for 4-hours talktime and 36hours standby.
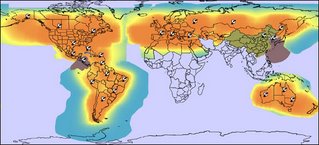
Features include: data calls (EV-DO), six operating languages and a range of faceplates. a new five-mode colur display and bluetooth capability. What, no mention of Phonebook, testing and calls registers? tch!!!!! ohhhhhhhh. Well it might do, but the spec that I saw didn't mention them. The world map identifies service to Europe, and UK is in this list for provision of service. However, the coloured coverage areas, as far as I can make out from Globalstar's site, denotes coverage for Direct Dial-Up data calls only. (saw newsfeed at Popgadget.net)

Seems our common mobile 'phones will now compete with satellite 'phone for fashion and style. The new GSP-1700 from Globalstar Inc has been quite drastically reduced in size from the old-brick, clumsy satellite handset design previously available. The battery allows for 4-hours talktime and 36hours standby.

Features include: data calls (EV-DO), six operating languages and a range of faceplates. a new five-mode colur display and bluetooth capability. What, no mention of Phonebook, testing and calls registers? tch!!!!! ohhhhhhhh. Well it might do, but the spec that I saw didn't mention them. The world map identifies service to Europe, and UK is in this list for provision of service. However, the coloured coverage areas, as far as I can make out from Globalstar's site, denotes coverage for Direct Dial-Up data calls only. (saw newsfeed at Popgadget.net)
Smith's LND Dilemma
Smith's LND Dilemma
In real cases of mobile 'phone and SIM Card examination, as opposed to theoretical discussion about them, entries found in elementary file Last Number Dialled (EFLND) on a SIM Card can be quite complex to determine and today do not have a clearly defined pattern as to the origin of data, as one might think is suggested by the GSM Standard 11.11. This is largely due to misunderstandings as to the interpretation to be given to relevant clauses within the Standard and what they actually mean. There is some commentary in the Standard which provides for minimal comprehension of possible origin of data in LND, but not nearly enough for my work.
Back in the early 1990s there was an considerable amount to be learnt about GSM SIM cards and I needed a way that I could at least comprehend how data was being shared and recorded in elementary files (EF) in the SIM. As data was being recorded in the elementary files Last Number Dialled (EFLND) which appeared to be from origins other than from within the SIM by 2002, this meant a re-think of a simple 'problem' algorithm I had written back in 1995, which was titled "Smith's LND Dilemma", so titled for copyright reasons.
As mentioned above, the early algorithm was written relating to data generated in EFLND internally to the SIM and the 2003 update I did included possible arguments for external sources for generation of the data. I updated Smith's LND Dilemma to consider where less restrictive assumptions are considered regarding determining LND entries, the investigation uncovers a more complex series of potential events and appears as a non-complete combinational problem, due to some undefined sources. The undefined sources are used for investigation having first investigated common sources where data is known to originate. The undefined sources were, in essence, a precaution by me to cover myself where sources occurred from uncommon or a new implementations in SIM, or simlar from external sources, such as mobile telephones. Also, I needed to consider the issue of programs that can generate data on SIM Cards. I didn't wish to be confined by identifying particular program/s.
I have reproduced the main part of Smith's LND Dilemma and cut out coding remarks and other bits etc, which make for uncomfortable reading and comprehension. Well I hope this helps examiners, or newbies to our branch of forensic science, regarding investigating mobile telephone evidence. This is just the tip of the iceberg .
Smith's LND Dilemma
#
# Makefile for Smith's LND Dilemma (c) by Gregory N Smith
#
.
.
.
Where (
Entries = 3F00+2FE2+7F10+6F44+6F4A
)
if (
and 7F20+6F38+7F10+6F3D = allocated+activated+string
)
Where origin needs to be known (
If 7F10+6F3D+6F44+6F3A+6F40+6F4A
)
and/ (
If 7F10+6F3D+6F44+6F4A+6F42
)
/or (
If 7F10+6F3D+6F44+6F3B(6F3A+6F40+6F42+6F4A)+6F4B
)
/or (
If 7F10+6F3D+6F44+6F49+6F4C
)
/or (
If 7F10+6F3D+6F44+6F4D(6F44+6F3A+6F40+6F42+6F49+6F4A+6F4B+6F4C)+6F4E
)= Entries
However, where (
Entries = 3F00+2FE2+7F10+6F44+6F4A
)
If (
and 7F20+6F38+7F10+6F3D = allocated+activated+string
)
Where origin needs to be known (
If +CGMI+CGMM +CGSN
)
If (
and/ +CLCC+7F10+6F3D+6F44+6F4A
)
If (
/or +CPBS(+CPBR)+7F10+6F3D+6F44+6F4A
)
If (
/or +CMGL(+CPMR)+7F10+6F3D+6F44+6F4A
)= Entries
Alternatively, where (
Entries = 3F00+2FE2+7F10+6F44+6F4A
)
if (
and 7F20+6F38+7F10+6F3D = allocated+activated+string
)
Where origin needs to be known (
and/ undefinedsource+7F10+6F3D+6F44+6F4A
)= Entries
(c) Gregory N Smith 1995-2006
In real cases of mobile 'phone and SIM Card examination, as opposed to theoretical discussion about them, entries found in elementary file Last Number Dialled (EFLND) on a SIM Card can be quite complex to determine and today do not have a clearly defined pattern as to the origin of data, as one might think is suggested by the GSM Standard 11.11. This is largely due to misunderstandings as to the interpretation to be given to relevant clauses within the Standard and what they actually mean. There is some commentary in the Standard which provides for minimal comprehension of possible origin of data in LND, but not nearly enough for my work.
Back in the early 1990s there was an considerable amount to be learnt about GSM SIM cards and I needed a way that I could at least comprehend how data was being shared and recorded in elementary files (EF) in the SIM. As data was being recorded in the elementary files Last Number Dialled (EFLND) which appeared to be from origins other than from within the SIM by 2002, this meant a re-think of a simple 'problem' algorithm I had written back in 1995, which was titled "Smith's LND Dilemma", so titled for copyright reasons.
As mentioned above, the early algorithm was written relating to data generated in EFLND internally to the SIM and the 2003 update I did included possible arguments for external sources for generation of the data. I updated Smith's LND Dilemma to consider where less restrictive assumptions are considered regarding determining LND entries, the investigation uncovers a more complex series of potential events and appears as a non-complete combinational problem, due to some undefined sources. The undefined sources are used for investigation having first investigated common sources where data is known to originate. The undefined sources were, in essence, a precaution by me to cover myself where sources occurred from uncommon or a new implementations in SIM, or simlar from external sources, such as mobile telephones. Also, I needed to consider the issue of programs that can generate data on SIM Cards. I didn't wish to be confined by identifying particular program/s.
I have reproduced the main part of Smith's LND Dilemma and cut out coding remarks and other bits etc, which make for uncomfortable reading and comprehension. Well I hope this helps examiners, or newbies to our branch of forensic science, regarding investigating mobile telephone evidence. This is just the tip of the iceberg .
Smith's LND Dilemma
#
# Makefile for Smith's LND Dilemma (c) by Gregory N Smith
#
.
.
.
Where (
Entries = 3F00+2FE2+7F10+6F44+6F4A
)
if (
and 7F20+6F38+7F10+6F3D = allocated+activated+string
)
Where origin needs to be known (
If 7F10+6F3D+6F44+6F3A+6F40+6F4A
)
and/ (
If 7F10+6F3D+6F44+6F4A+6F42
)
/or (
If 7F10+6F3D+6F44+6F3B(6F3A+6F40+6F42+6F4A)+6F4B
)
/or (
If 7F10+6F3D+6F44+6F49+6F4C
)
/or (
If 7F10+6F3D+6F44+6F4D(6F44+6F3A+6F40+6F42+6F49+6F4A+6F4B+6F4C)+6F4E
)= Entries
However, where (
Entries = 3F00+2FE2+7F10+6F44+6F4A
)
If (
and 7F20+6F38+7F10+6F3D = allocated+activated+string
)
Where origin needs to be known (
If +CGMI+CGMM +CGSN
)
If (
and/ +CLCC+7F10+6F3D+6F44+6F4A
)
If (
/or +CPBS(+CPBR)+7F10+6F3D+6F44+6F4A
)
If (
/or +CMGL(+CPMR)+7F10+6F3D+6F44+6F4A
)= Entries
Alternatively, where (
Entries = 3F00+2FE2+7F10+6F44+6F4A
)
if (
and 7F20+6F38+7F10+6F3D = allocated+activated+string
)
Where origin needs to be known (
and/ undefinedsource+7F10+6F3D+6F44+6F4A
)= Entries
(c) Gregory N Smith 1995-2006
Tuesday, November 14, 2006
Data eliminated - FileShredPPC 2.3
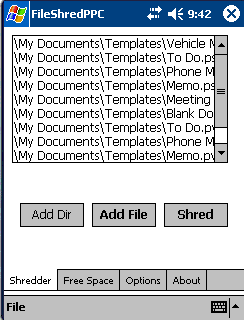 Data eliminated - FileShredPPC 2.3
Data eliminated - FileShredPPC 2.3 I thought this would be of interest for those who extract and harvest data from PDAs and CF/SD cards. When deleting a file, the file is still there, only the pointers to the file are what are removed. The physical data from the file still remains and can be recovered. FileShredPPC opens the file to be deleted and overwrites the content with a series of nulls, ones, or random data. This process is semi-randomized, and depends on how many overwrites are choosen, which can be anywhere from 1 to 10. It then truncates the file to a zero byte file, and deletes it.
This data eliminator wipe free space too. Click on the "Free Space" Tab, choose the volume you want to wipe the free space, and click on "Wipe Free Space". Depending on the size of the volume, it can take some time as it wipes free space on a storage card (e.g. 18 Mb) with the default 3 passes, and the file access ran at about 10KB/sec.
Interetingly, as Volume names can be standard this app ignores standard names like "\windows" and just removes non-standard directory names. It also has the ability to automatically load the ENTIRE contents of a directory for shredding by use of the Add Dir button. Click on this button, select directory, hit select, and all files in the directory will be added to the Shred list! Prerequisites: .NET Compact Framework
Sunday, November 12, 2006
Mobile phone forensics and evidence
Mobile phone forensics and evidence
The UK appears to be leading the world when in comes to mobile telephone forensics and evidence. Law enforcement globally, though, relies heavily upon mobile telephone evidence. The concerns over terrorism and the use by terrorists to use technology promoted an enquiry by the UK House of Commons Home Affairs Select Committee into the use of evidence from mobile telephone devices, prompting leading mobile telephone forensic specialists to identify forensic techniques available in this area:
http://www.publications.parliament.uk/pa/cm200506/cmselect/cmhaff/910/910we17.htm
The UK appears to be leading the world when in comes to mobile telephone forensics and evidence. Law enforcement globally, though, relies heavily upon mobile telephone evidence. The concerns over terrorism and the use by terrorists to use technology promoted an enquiry by the UK House of Commons Home Affairs Select Committee into the use of evidence from mobile telephone devices, prompting leading mobile telephone forensic specialists to identify forensic techniques available in this area:
http://www.publications.parliament.uk/pa/cm200506/cmselect/cmhaff/910/910we17.htm
Saturday, November 11, 2006
GSM radio coverage bounces backward
GSM radio coverage bounces backward
A characteristic of radio signals is that they reflect off surfaces. Not startling or new news in itself, unless one considers its impact on radio coverage propagated North, but due to reflection, can be detected for instance in the South East or South West, behind the Sector of the Mast. In yet another case, I am told that at the Central Criminal Court evidence in a case confirmed that coverage in the opposite direction from its angle of propagation was detected and useable. It is useful to know this in cases for instance where the location of a mobile 'phone and a Cell ID's radio coverage at a location are not compatible with the investigation evidence. Importantly, the case does not set a universal principle, as this phenomenon does not happen in every case due to flat earth, no clutter etc. Tests will still need to be conducted on a case by case basis. It does though cast doubt over simply conducting spot-tests at one location.
A characteristic of radio signals is that they reflect off surfaces. Not startling or new news in itself, unless one considers its impact on radio coverage propagated North, but due to reflection, can be detected for instance in the South East or South West, behind the Sector of the Mast. In yet another case, I am told that at the Central Criminal Court evidence in a case confirmed that coverage in the opposite direction from its angle of propagation was detected and useable. It is useful to know this in cases for instance where the location of a mobile 'phone and a Cell ID's radio coverage at a location are not compatible with the investigation evidence. Importantly, the case does not set a universal principle, as this phenomenon does not happen in every case due to flat earth, no clutter etc. Tests will still need to be conducted on a case by case basis. It does though cast doubt over simply conducting spot-tests at one location.
Reports and Newsletters Available
Reports and Newsletters Available
Mobile Telephone Evidence (MTE) Newsletter
Mobile Telephone Surveillance (MTS) Newsletter
Mobile Telephone Seizure Procedure
Mobile Telephone Handset Cloning Report
Mobile Telephobne SIM Card Cloning Report
Mobile Telephone Cell Site Analysis
Please sent a request to: TrewMTE@gmail.com
You will need to provide identifiable organisation details and valid email and phone numbers.
Mobile Telephone Evidence (MTE) Newsletter
Mobile Telephone Surveillance (MTS) Newsletter
Mobile Telephone Seizure Procedure
Mobile Telephone Handset Cloning Report
Mobile Telephobne SIM Card Cloning Report
Mobile Telephone Cell Site Analysis
Please sent a request to: TrewMTE@gmail.com
You will need to provide identifiable organisation details and valid email and phone numbers.
Friday, November 10, 2006
WHAT'S THIS?
WHAT'S THIS?

The x-ray from one of four prisoners in an El Salvador prison who smuggled in cellphones, a phone charger and spare chips in their bowels so they could coordinate crimes from their cells, according to prison officials at the maximum security Zacatecoluca. Urrrgghhhhh!!! Think I would have to phone my insurance company and ask whether my desk was covered to have one of those items put on it.
http://today.reuters.com/news/articlenews.aspx?type=oddlyEnoughNews&storyID=2006-09-08T015309Z_01_N06184750_RTRUKOC_0_US-SALVADOR-PRISONERS.xml&WTmodLoc=Home-C5-oddlyEnoughNews-2

The x-ray from one of four prisoners in an El Salvador prison who smuggled in cellphones, a phone charger and spare chips in their bowels so they could coordinate crimes from their cells, according to prison officials at the maximum security Zacatecoluca. Urrrgghhhhh!!! Think I would have to phone my insurance company and ask whether my desk was covered to have one of those items put on it.
http://today.reuters.com/news/articlenews.aspx?type=oddlyEnoughNews&storyID=2006-09-08T015309Z_01_N06184750_RTRUKOC_0_US-SALVADOR-PRISONERS.xml&WTmodLoc=Home-C5-oddlyEnoughNews-2
Thursday, November 09, 2006
Cell Site Analysis
Cell Site Analysis
"Radio, she is a beauty but a mistress to none. Just when you think you have her coralled up she'll jump and kick you right in the backside when you least expect it. She is indeed a worthy challenge."
I said that in 1994, and I haven't changed my mind todate.
The above will be brought home to you only too quickly when you deal with digital radio and the art of cell site analysis. If you want a starting point with GSM, then start with the GSM standards. Having spent many years dealing with GSM and the evidence that can be produced from it, I am still in awe today as I was back in 1993 when I first started to work with GSM. For those not yet having an insight into the GSM, I can only say we really do stand on the shoulders of geniuses. I cannot think of any other technology where the authors produced such an amazing system and went on to fully document what they have done, only asking you respect what they have done by reading the standards and comprehending, and then go on to use it.
For example, when considering GSM, it is worth knowing at least four principles to be understood:
- There are mandatory requirements with mandatory outcomes
- There are mandatory requirements with optional outcomes
- There are optional requirements with mandatory outcomes
- There are optional requirements with optional outcomes
This appears to apply right across the GSM system.
There are some very good radio detection systems around, such as TEMS, Sagem etc, useful for part of the job of cell site analysis radio data acquisition. Each provides different ways to assess the radio system. An expert or examiner cannot get by though relying on devices alone. You need knowledge, skill and experience in order to comprehend the radio assessment and then how to apply it.
If you do come to our branch of forensic science, do make sure you understand the GSM system and not simply knowing how the device works. It does make for better quality of evidence and assist in a higher degree of certainty about the opinion that may be expressed regarding mobile telephone evidence.
Also, if you intend to enter 3G forensic investigation, you will find it much easier having a GSM background understanding and how it impacts; and of course having read the 3G standards.
The caveat in all of this, of course, is both systems (GSM & 3G) are constantly evolving. Even with all the years I have been working with GSM, what I have found is the more I know, the more I need to know. I find exactly the same with 3G.
"Radio, she is a beauty but a mistress to none. Just when you think you have her coralled up she'll jump and kick you right in the backside when you least expect it. She is indeed a worthy challenge."
I said that in 1994, and I haven't changed my mind todate.
The above will be brought home to you only too quickly when you deal with digital radio and the art of cell site analysis. If you want a starting point with GSM, then start with the GSM standards. Having spent many years dealing with GSM and the evidence that can be produced from it, I am still in awe today as I was back in 1993 when I first started to work with GSM. For those not yet having an insight into the GSM, I can only say we really do stand on the shoulders of geniuses. I cannot think of any other technology where the authors produced such an amazing system and went on to fully document what they have done, only asking you respect what they have done by reading the standards and comprehending, and then go on to use it.
For example, when considering GSM, it is worth knowing at least four principles to be understood:
- There are mandatory requirements with mandatory outcomes
- There are mandatory requirements with optional outcomes
- There are optional requirements with mandatory outcomes
- There are optional requirements with optional outcomes
This appears to apply right across the GSM system.
There are some very good radio detection systems around, such as TEMS, Sagem etc, useful for part of the job of cell site analysis radio data acquisition. Each provides different ways to assess the radio system. An expert or examiner cannot get by though relying on devices alone. You need knowledge, skill and experience in order to comprehend the radio assessment and then how to apply it.
If you do come to our branch of forensic science, do make sure you understand the GSM system and not simply knowing how the device works. It does make for better quality of evidence and assist in a higher degree of certainty about the opinion that may be expressed regarding mobile telephone evidence.
Also, if you intend to enter 3G forensic investigation, you will find it much easier having a GSM background understanding and how it impacts; and of course having read the 3G standards.
The caveat in all of this, of course, is both systems (GSM & 3G) are constantly evolving. Even with all the years I have been working with GSM, what I have found is the more I know, the more I need to know. I find exactly the same with 3G.
Mobile number analyser
Mobile number analyser
This is a useful resources for mobile telephone evidence analysis... although I would suspect some people in the field know about it. There are quite a number of these free online services on the Internet. The only observation I would make is that online services like these usually provide identification only of the mobile/country code (MCC etc) and mobile/network code (MNC etc) and so on. I would certainly not enter my complete IMSI (International Mobile Subscriber Identity) or the SSN (SIM Serial Number) from your the SIM card, IMEI etc, simply from a privacy pointof view, apart from anything else.
Phone Dialling Number Analaysis
https://www.numberingplans.com//?page=analysis&sub=phonenr
International Mobile Subscriber Identity (IMSI) Analysis
https://www.numberingplans.com//?page=analysis&sub=imsinr
International Mobile Equipment Identity (IMEI) Analysis
https://www.numberingplans.com//?page=analysis&sub=imeinr
SIM Serial Number (SIM Card number) Analysis
https://www.numberingplans.com//?page=analysis&sub=simnr
This is a useful resources for mobile telephone evidence analysis... although I would suspect some people in the field know about it. There are quite a number of these free online services on the Internet. The only observation I would make is that online services like these usually provide identification only of the mobile/country code (MCC etc) and mobile/network code (MNC etc) and so on. I would certainly not enter my complete IMSI (International Mobile Subscriber Identity) or the SSN (SIM Serial Number) from your the SIM card, IMEI etc, simply from a privacy pointof view, apart from anything else.
Phone Dialling Number Analaysis
https://www.numberingplans.com//?page=analysis&sub=phonenr
International Mobile Subscriber Identity (IMSI) Analysis
https://www.numberingplans.com//?page=analysis&sub=imsinr
International Mobile Equipment Identity (IMEI) Analysis
https://www.numberingplans.com//?page=analysis&sub=imeinr
SIM Serial Number (SIM Card number) Analysis
https://www.numberingplans.com//?page=analysis&sub=simnr
Improvised Mobile Device
Improvised Mobile Device
Interesrting photos of mobile phone and wireless device released on the Internet from US military source, apparently having been altered to act as a detonator.

Apart from the electronics wrapped on the outside of the Nokia mobile 'phone, apparently the disturbing photo also shows the handset LCD displaying "01 Call Missed".

This photo was apparently issued courtesy of the US Department of Defense.
Conclusion: I trust your seizure procedures and handling procedures are up-to-date.
Interesrting photos of mobile phone and wireless device released on the Internet from US military source, apparently having been altered to act as a detonator.

Apart from the electronics wrapped on the outside of the Nokia mobile 'phone, apparently the disturbing photo also shows the handset LCD displaying "01 Call Missed".

This photo was apparently issued courtesy of the US Department of Defense.
Conclusion: I trust your seizure procedures and handling procedures are up-to-date.
Wednesday, November 08, 2006
Not always the right moment
Not always the right moment
A moment in the life of a forensic engineer
Being involved in forensics has its moments and compensations, but that benefit does not extend to immunity from discussing matters with numbskulls that one may encounter from time to time along the way .
One forensic forum I belong to has been running short of topical discussion laterly, so out of the goodness of my heart I posted some information about a Postal and other scams that are currently in vogue at the moment. The intention of this was to highlight various elements of the scams involved. That being postal fraud, social engineering and call charging fraud etc etc. I had hoped at least these elements would be of sufficient interest to stimulate debate... but owwwwwwwwww noooooooooo!!! Do you think we even got that far?
Stone me, if one of the forum members doesn't start to get all arsy about it.
"The prices you quoted for the call fraud are wrong blah blah blah", he wrote.
"Errr no", I said, "this information is from a known scam and being mentioned just for the discussion about the postal and other scams. You know, just trying to analyse the elements of the crimes and all that..."
Would you believe it, this cheeky blighter only writes back "And you need to go an do some research"
Well I thought, you can push off 'n' all.
Geeze, you try to join in, help out and do your bit, and then get lumbered with a right artist like that.
Not exactly CSI Miami is it?
Mind you, a friend of mine who works in this business goes around wearing Sunglasses and keeps mentioning the name Horatio. I asked him whether he was hinting at HMS Victory on its summer holiday?
I'm dreading the time he turns up wearing a Sombrero...
A moment in the life of a forensic engineer
Being involved in forensics has its moments and compensations, but that benefit does not extend to immunity from discussing matters with numbskulls that one may encounter from time to time along the way .
One forensic forum I belong to has been running short of topical discussion laterly, so out of the goodness of my heart I posted some information about a Postal and other scams that are currently in vogue at the moment. The intention of this was to highlight various elements of the scams involved. That being postal fraud, social engineering and call charging fraud etc etc. I had hoped at least these elements would be of sufficient interest to stimulate debate... but owwwwwwwwww noooooooooo!!! Do you think we even got that far?
Stone me, if one of the forum members doesn't start to get all arsy about it.
"The prices you quoted for the call fraud are wrong blah blah blah", he wrote.
"Errr no", I said, "this information is from a known scam and being mentioned just for the discussion about the postal and other scams. You know, just trying to analyse the elements of the crimes and all that..."
Would you believe it, this cheeky blighter only writes back "And you need to go an do some research"
Well I thought, you can push off 'n' all.
Geeze, you try to join in, help out and do your bit, and then get lumbered with a right artist like that.
Not exactly CSI Miami is it?
Mind you, a friend of mine who works in this business goes around wearing Sunglasses and keeps mentioning the name Horatio. I asked him whether he was hinting at HMS Victory on its summer holiday?
I'm dreading the time he turns up wearing a Sombrero...
Tuesday, November 07, 2006
JOKE
Incredible this idea of 'blogging'. Think of something, you can simply write it down and share it with the world.
I heard a joke recently that made me laugh.
A man in hospital after a serious operation. Lying in his recovery bed, post op, the nurse walks in with a bowl and flannel.
The patient has a ventilator mask on and says to the nurse:
"Are my testicles black?"
The nurse looks embarrassed and says:
"I don't know Sir! I am here to bathe your face and feet."
The patient says, "but are my testicles black?"
The nurse says, "Well, let me look".
She pulls back the bed covers and examines the man's testicles - lifts, rummagaes around, looks, places them back and puts the bed covers back - and replies
"No, they look alright to me Sir!"
The patient removes the ventilator mask and says:
"Thank you nurse, that was very nice, but I asked: Are My Test Results Back?"
I heard a joke recently that made me laugh.
A man in hospital after a serious operation. Lying in his recovery bed, post op, the nurse walks in with a bowl and flannel.
The patient has a ventilator mask on and says to the nurse:
"Are my testicles black?"
The nurse looks embarrassed and says:
"I don't know Sir! I am here to bathe your face and feet."
The patient says, "but are my testicles black?"
The nurse says, "Well, let me look".
She pulls back the bed covers and examines the man's testicles - lifts, rummagaes around, looks, places them back and puts the bed covers back - and replies
"No, they look alright to me Sir!"
The patient removes the ventilator mask and says:
"Thank you nurse, that was very nice, but I asked: Are My Test Results Back?"
Vodafone move to standardise handset software
The Daily Mail City&Finance Page 68 (Tuesday, November 7, 2006) ran a short piece on Vodafone unveiling "plans to become the first mobile operator to standardise the software of its handsets". It is to "slash the number of operating systems it would develop applications for in the next five years". This will reduce to three, that of Microsoft Windows Mobile, Symbian/S60 and Linux.
The three choices Vodafone have made are not bad, but there is always the worry from end-users point of view that they end up with largely a fait accompli, that of limited choices dished up by an operator.
It will be interesting to see whether the handset manufacturers follow suit and downsize their operating systems to comply with Vodafone's plans
Alternatively, the likes of Nokia, Motorola, SonyEricsson, Samsung etc could create mobile 'phones with the appropriate GSM/GPRS/WCDMA/WiFi wireless operating systems on them and allow the general public to profile their handsets with the application features (download) they not only like, but actually want.
The three choices Vodafone have made are not bad, but there is always the worry from end-users point of view that they end up with largely a fait accompli, that of limited choices dished up by an operator.
It will be interesting to see whether the handset manufacturers follow suit and downsize their operating systems to comply with Vodafone's plans
Alternatively, the likes of Nokia, Motorola, SonyEricsson, Samsung etc could create mobile 'phones with the appropriate GSM/GPRS/WCDMA/WiFi wireless operating systems on them and allow the general public to profile their handsets with the application features (download) they not only like, but actually want.
Super Ghost SIM
Interesting product but which 3F002FE27F206F07 would be relevant? ... happy mobile telephone evidence hunting...

Super Ghost SIM
- NEW FEATURE! Switch between SIMs via the phone's menu!
- NEW FEATURE! Option to auto switch between SIMs every 1-99 minutes
- use the manual sim selection option if you don't want to auto switch
- allows you to use two SIM cards in one phone
- no need to cut your SIM card like with similar products
- more convenient than removing your back cover/battery every time you want to swap SIM cards
- combine business/personal lines and address books on one handset
- switch between networks easily - no more coverage problems!
- take advantages of cheaper rates from different phone companies
- saves your previous calls, received calls, time and date settings etc.
- new ultra slim design - sits inbetween your battery and back cover
- no need to replace your phone's back cover - the ghost SIMs sit inbetween your battery and standard back cover
- works with all SIMs (including 3)
- can be used to add another 200 contacts to your phone book via the second sim card (sim dependent)
- works with virtually all makes and models
- also known as dual SIMs/twin SIMs
http://www.formymobile.co.uk/proddetail.php?prod=supersim

Super Ghost SIM
- NEW FEATURE! Switch between SIMs via the phone's menu!
- NEW FEATURE! Option to auto switch between SIMs every 1-99 minutes
- use the manual sim selection option if you don't want to auto switch
- allows you to use two SIM cards in one phone
- no need to cut your SIM card like with similar products
- more convenient than removing your back cover/battery every time you want to swap SIM cards
- combine business/personal lines and address books on one handset
- switch between networks easily - no more coverage problems!
- take advantages of cheaper rates from different phone companies
- saves your previous calls, received calls, time and date settings etc.
- new ultra slim design - sits inbetween your battery and back cover
- no need to replace your phone's back cover - the ghost SIMs sit inbetween your battery and standard back cover
- works with all SIMs (including 3)
- can be used to add another 200 contacts to your phone book via the second sim card (sim dependent)
- works with virtually all makes and models
- also known as dual SIMs/twin SIMs
http://www.formymobile.co.uk/proddetail.php?prod=supersim
Super Ghost SIM
Interesting product but which 3F002FE27F206F07 would be relevant? ... happy mobile telephone evidence hunting...

Super Ghost SIM
- NEW FEATURE! Switch between SIMs via the phone's menu!
- NEW FEATURE! Option to auto switch between SIMs every 1-99 minutes
- use the manual sim selection option if you don't want to auto switch
- allows you to use two SIM cards in one phone
- no need to cut your SIM card like with similar products
- more convenient than removing your back cover/battery every time you want to swap SIM cards
- combine business/personal lines and address books on one handset
- switch between networks easily - no more coverage problems!
- take advantages of cheaper rates from different phone companies
- saves your previous calls, received calls, time and date settings etc.
- new ultra slim design - sits inbetween your battery and back cover
- no need to replace your phone's back cover - the ghost SIMs sit inbetween your battery and standard back cover
- works with all SIMs (including 3)
- can be used to add another 200 contacts to your phone book via the second sim card (sim dependent)
- works with virtually all makes and models
- also known as dual SIMs/twin SIMs
http://www.formymobile.co.uk/proddetail.php?prod=supersim

Super Ghost SIM
- NEW FEATURE! Switch between SIMs via the phone's menu!
- NEW FEATURE! Option to auto switch between SIMs every 1-99 minutes
- use the manual sim selection option if you don't want to auto switch
- allows you to use two SIM cards in one phone
- no need to cut your SIM card like with similar products
- more convenient than removing your back cover/battery every time you want to swap SIM cards
- combine business/personal lines and address books on one handset
- switch between networks easily - no more coverage problems!
- take advantages of cheaper rates from different phone companies
- saves your previous calls, received calls, time and date settings etc.
- new ultra slim design - sits inbetween your battery and back cover
- no need to replace your phone's back cover - the ghost SIMs sit inbetween your battery and standard back cover
- works with all SIMs (including 3)
- can be used to add another 200 contacts to your phone book via the second sim card (sim dependent)
- works with virtually all makes and models
- also known as dual SIMs/twin SIMs
http://www.formymobile.co.uk/proddetail.php?prod=supersim
U8120 secret Java Menu
U8120 secret Java Menu
- Access the menu, go to Applications
- Then select Setting No.3
- Type in the 3698*#*, which reveals a secret java menu
- Then select Setting No.1 (which should be disable)
Having connected the handset to LG Phone Manager reveals a Java folder, not previously seen, that is now visible. Whilst the new folder can be used for uploading games, it isn't difficult to work out that other data may be hiding on the handset, particularly where the above processes is reversed and the java folder is then hidden again, the handset *may* not recognise, thus not display, any uploaded data under this folder.
As with any matters like this, there are a number of cautionary warnings:
1. This is only for discuss and is not an instruction, advice or anything else to go out and start implementing this info...no guarantees are provided, either express or implied.
2. As with any issues not anticipated by a handset manufacturer, when it becomes general knowledge (this matter was known in 2005), a particular handset manufacturer may alter any later versions of the same model to prevent access..
3. If you do not know what you are doing when playing with your own handset or someone else's, then DONT do it.
- Access the menu, go to Applications
- Then select Setting No.3
- Type in the 3698*#*, which reveals a secret java menu
- Then select Setting No.1 (which should be disable)
Having connected the handset to LG Phone Manager reveals a Java folder, not previously seen, that is now visible. Whilst the new folder can be used for uploading games, it isn't difficult to work out that other data may be hiding on the handset, particularly where the above processes is reversed and the java folder is then hidden again, the handset *may* not recognise, thus not display, any uploaded data under this folder.
As with any matters like this, there are a number of cautionary warnings:
1. This is only for discuss and is not an instruction, advice or anything else to go out and start implementing this info...no guarantees are provided, either express or implied.
2. As with any issues not anticipated by a handset manufacturer, when it becomes general knowledge (this matter was known in 2005), a particular handset manufacturer may alter any later versions of the same model to prevent access..
3. If you do not know what you are doing when playing with your own handset or someone else's, then DONT do it.
Electricity generator in your backpack
Electricity generator in your backpack
 Here is an interesting big gadget. As any professional examiner of mobile telephones will know being called to deal with onsite examination where no electricity is available can be a nightmare. Lugging back power supplies can be a pain, particularly if having to move between locations. This device may bring some relief although it may not look attractive.
Here is an interesting big gadget. As any professional examiner of mobile telephones will know being called to deal with onsite examination where no electricity is available can be a nightmare. Lugging back power supplies can be a pain, particularly if having to move between locations. This device may bring some relief although it may not look attractive.
Developed following hurricane Katrina (2005), the backpack has been designed to "assist first responders and disaster relief workers to generate their own electricity for communications devices, night vision goggles, water purifiers or other crucial, portable electronics", according to http://msnbc.msn.com/id/9245155/.
I can see it having application under certain conditions, however, expect some frowns if any mobile 'phone examiners turn up at court wearing one..
 Here is an interesting big gadget. As any professional examiner of mobile telephones will know being called to deal with onsite examination where no electricity is available can be a nightmare. Lugging back power supplies can be a pain, particularly if having to move between locations. This device may bring some relief although it may not look attractive.
Here is an interesting big gadget. As any professional examiner of mobile telephones will know being called to deal with onsite examination where no electricity is available can be a nightmare. Lugging back power supplies can be a pain, particularly if having to move between locations. This device may bring some relief although it may not look attractive.Developed following hurricane Katrina (2005), the backpack has been designed to "assist first responders and disaster relief workers to generate their own electricity for communications devices, night vision goggles, water purifiers or other crucial, portable electronics", according to http://msnbc.msn.com/id/9245155/.
I can see it having application under certain conditions, however, expect some frowns if any mobile 'phone examiners turn up at court wearing one..
Sunday, November 05, 2006
Judge bans paedophile from using Internet and mobile phones
Judge bans paedophile from using Internet and mobile phones
A British judge on 15 January 2004 made a ground-breaking ruling by banning a paedophile from using the Internet or mobile telephones after he was found to have had sex with a 14-year-old girl who he lured through an on-line chatroom. Judge Huw Daniel at a court in central Wales ruled that Gary Thomas, 37, should be jailed for 18 months and restrained from using the Internet or mobile telephones for the next five years. Daniel said the British law must be changed to allow the judiciary to give tougher sentences to paedophiles who target girls of 14 and over. Currently Britain's maximum sentence for such offenders is two years. The ban is believed to be the first of its kind in Britain. Reported by Chinaview
A British judge on 15 January 2004 made a ground-breaking ruling by banning a paedophile from using the Internet or mobile telephones after he was found to have had sex with a 14-year-old girl who he lured through an on-line chatroom. Judge Huw Daniel at a court in central Wales ruled that Gary Thomas, 37, should be jailed for 18 months and restrained from using the Internet or mobile telephones for the next five years. Daniel said the British law must be changed to allow the judiciary to give tougher sentences to paedophiles who target girls of 14 and over. Currently Britain's maximum sentence for such offenders is two years. The ban is believed to be the first of its kind in Britain. Reported by Chinaview
EUROPEAN POLICE COLLEGE (CEPOL)
EUROPEAN POLICE COLLEGE (CEPOL)
An event that has largely gone unnoticed, but confirmed from the Brussels common accord of the 13th December 2003, is the establishment of CEPOL. The good news is that the Heads of each Member State agreed that it should be located in London. Whilst the notion of Homeland Security has been played out as applying to the UK, the creation, establishment and location of these newer agencies appears more aligned with strategic placement, similar to the way US which deploys its agencies in various states.
An event that has largely gone unnoticed, but confirmed from the Brussels common accord of the 13th December 2003, is the establishment of CEPOL. The good news is that the Heads of each Member State agreed that it should be located in London. Whilst the notion of Homeland Security has been played out as applying to the UK, the creation, establishment and location of these newer agencies appears more aligned with strategic placement, similar to the way US which deploys its agencies in various states.
Global Initiative to Crackdown on Stolen Mobile Telephones
Global Initiative to Crackdown on Stolen Mobile Telephones
The escalation in mobile phone thefts in 2000 and 2001 brought a major crackdown in the UK. The thefts from the most vulnerable in our society, generated massive media publicity and lead to several UK initiatives. Firstly, legislation was enacted under the Mobile Telephon (Reprogramming) Act 2002, this was stop the stolen handset serial number (IMEI) being altered so as to avoid detection as stolen mobile telephone when connected to any of the UK mobile phone networks. Secondly, mobile telephones registered as stolen were blocked from using the network. The impact of the crackdown lead to detection of reportedly 30,000 mobile telephones having the same serial number and over half-million mobile phones being blocked. This success has been achieved by the lawful requirement for UK mobile network operators to share their databases of mobile telephones using each other networks, improving network operators network surveillance and squeezing out black listed mobile telephones.
There is still more to do though as it is believed there are some 130 million mobile telephone handsets in circulation in the UK, arising from ten years of success of the GSM (Global System for Mobile) communication. It is thought that there are still tens of thousands of mobiles that have not been reported by their owners as lost or stolen. On the face of the UK successful reducing theft and cloning it looks like the UK initiative appears to be having global appeal.
Cloning of mobile telephone serial numbers (IMEI) is not unlawful in many other countries and the practice of cloning continues unabated. Many of those mobile phones find there way back into the UK, through natural routes suggest as users roaming in the UK through to the more nefarious grey market trade and used by organised crime. Other countries unaffected by UK legislation have no requirement to share their databases. Attempting to block roaming cloned mobiles in the UK may be largely ineffective.
Now, however several of the world’s largest wireless operators have launched an global initiative aimed at cracking down on mobile phone theft by organised criminal gangs. The new plan will render a handset stolen in one country useless in another, thus stemming the flow of stolen handsets into Africa, Asia and Europe. The GSM Association is leading the initiative, which is proposing the use of an international register of IMEI (serial) numbers that will be accessible by all GSM operators. To further strengthen the validity of an IMEI being genuine and unique to a particular device, Nokia, NEC and SonyEricsson and other manufacturers are working towards the early introduction of new technology that will make it almost impossible for the unauthorised reprogramming of wireless phones. This scheme should further underpin the initiative by the GSM Association.
In reality, of course, until this international register is fully operational and detecting registered stolen or lost phones it is foreseen cloned mobile phones will be in circulation for some years yet. That forecast is based upon the huge and undeniable success of GSM globally and the hundreds of millions of GSM mobiles in circulation worldwide.
The escalation in mobile phone thefts in 2000 and 2001 brought a major crackdown in the UK. The thefts from the most vulnerable in our society, generated massive media publicity and lead to several UK initiatives. Firstly, legislation was enacted under the Mobile Telephon (Reprogramming) Act 2002, this was stop the stolen handset serial number (IMEI) being altered so as to avoid detection as stolen mobile telephone when connected to any of the UK mobile phone networks. Secondly, mobile telephones registered as stolen were blocked from using the network. The impact of the crackdown lead to detection of reportedly 30,000 mobile telephones having the same serial number and over half-million mobile phones being blocked. This success has been achieved by the lawful requirement for UK mobile network operators to share their databases of mobile telephones using each other networks, improving network operators network surveillance and squeezing out black listed mobile telephones.
There is still more to do though as it is believed there are some 130 million mobile telephone handsets in circulation in the UK, arising from ten years of success of the GSM (Global System for Mobile) communication. It is thought that there are still tens of thousands of mobiles that have not been reported by their owners as lost or stolen. On the face of the UK successful reducing theft and cloning it looks like the UK initiative appears to be having global appeal.
Cloning of mobile telephone serial numbers (IMEI) is not unlawful in many other countries and the practice of cloning continues unabated. Many of those mobile phones find there way back into the UK, through natural routes suggest as users roaming in the UK through to the more nefarious grey market trade and used by organised crime. Other countries unaffected by UK legislation have no requirement to share their databases. Attempting to block roaming cloned mobiles in the UK may be largely ineffective.
Now, however several of the world’s largest wireless operators have launched an global initiative aimed at cracking down on mobile phone theft by organised criminal gangs. The new plan will render a handset stolen in one country useless in another, thus stemming the flow of stolen handsets into Africa, Asia and Europe. The GSM Association is leading the initiative, which is proposing the use of an international register of IMEI (serial) numbers that will be accessible by all GSM operators. To further strengthen the validity of an IMEI being genuine and unique to a particular device, Nokia, NEC and SonyEricsson and other manufacturers are working towards the early introduction of new technology that will make it almost impossible for the unauthorised reprogramming of wireless phones. This scheme should further underpin the initiative by the GSM Association.
In reality, of course, until this international register is fully operational and detecting registered stolen or lost phones it is foreseen cloned mobile phones will be in circulation for some years yet. That forecast is based upon the huge and undeniable success of GSM globally and the hundreds of millions of GSM mobiles in circulation worldwide.
ABOUT THE AUTHOR
ABOUT THE AUTHOR
I have been involved with forensics and technology evidence for 22 years (1986-2007), of which 20 years with wireless evidence, and of which 14 years dealing with Global System for Mobile (GSM) communications evidence. The extent to which I have dealt with cellular/wireless evidence relates originally to the analogue mobile telephone system in the UK called TACS (Total Access Communications System) trial runs 1983 and launched 1985. This wireless system was phased out of use in the 1990s, although the last TACS wireless licence expired in 2005.
The predominant evidence for TACS related to investigating stolen and cloning mobile telephones. It required examination of the handset and transmitted identity to the network; the examination of the printed circuit boards for modification components or circuitry used to hijack the use of a genuine user's identity; to reprogram stolen identity into a stolen mobile and jettison original identity. To examine usage of stolen TACS mobile'phones in relation to Phonebook and mobile calls. To conduct cell site analysis based on the use of Masts by the stolen mobile 'phones and Masts radio coverage area. The last bulk of TACS mobile 'phone cases ended between 1997/98. This was largely due to the introduction of GSM in 1992 and the four fully operational GSM networks by 1994.
My work with GSM assisted in the introduction into evidence of the early GSM radio maps, called digital cell footprint maps but categorised as Best Server Plots/Density Maps and Single Cell Prediction Plots/Density Maps. This work with GSM began in 1993 with mobile telephone and SIM card examination, and GSM cell site analysis. In 1999 I created the first GSM accredited mobile telephone courses in the UK delivered in 2001 and in 2003 set about creating the first 3G USIM courses in the UK, which began in November 2005. My main skillsets are conducting research and development, data acquisition and harvesting, examining evidence but also presenting evidence in criminal courts of law, thus combining specialist R&D & evidential experience skillsets necessary when dealing with criminal proceedings.
Recently gave evidence to the House of Commons Home Affairs Select Committee - Terrorism Detention Powers relevant to mobile telephone evidence.
Appeared on Panorama to discuss Cell Site Analysis with respect to the Omagh Bombing 1988.
Gave evidence to the Omagh Inquiry held by the Intelligence Services Commissioner.
More info on Trew MTE courses: trewmte@googlemail.com
Currently Publications I produce:
Mobile Telephone Evidence (MTE) Newsletter
Mobile Telephone Surveillance (MTS) Newsletter
MTE Reports
Forensic Expert News (FEN)
Professional Communications Security Management (PCSM)
Past Publications
Professional Telephone Engineer and Installer
Telephone Times
Telephone News
Author
Admissibility of Computer Evidence in Criminal Proceedings
Understanding the European Community Phase II Directive
Implications of a regulatory framework for telecoms terminal equipment
European Telecommunications Approvals Process
The EMC Implications for type approval for telecommunications terminal equipment
Basic Overview of the Mobile Phone Network
Cloning SIM Cards
Cloning Mobile Phones
Access Control of Networks
PSTN Interface Requirements for Terminal Equipment
Telephone Installation: Keep it simply and legal
Profiting from Private Payphone
Meeting NETs Needs
Computer Evidence in Criminal Proceedings
Security Management - the evolution of standards
The path to Data Encryption and Cryptography
Network Management - Virus and other potential threats to the integrity of the network
Putting Britain First - A blueprint for the future control of public switched telephone network (PSTN)
(These are just a few of authored material over the years and some of the documents above are still available today)
Project Work
USIM Detective (available from Quantaq Solutions http://www.quantaq.com/). The work involved assisting the manufacturer to include forensic features and evidential standards.
I also run the only approved Accredited training for USIM Detective http://www.quantaq.com/ud_training.htm. This is a 3G training course.
Mobile Phone Forensics & Evidence training courses includes: introduction to mobile telephone examination, undersatnding the GSM/3G Standards, SIM/USIM examination, mobile phone examination, cell site analysis, interpretation of data.
Moderate the Mobile Forensics Forums at Forensic Focus:
http://www.forensicfocus.com/mobile-forensics-forum
Also run Mobile Telephone Case law:
http://www.forensicfocus.com/index.php?name=Forums&file=viewforum&f=18
Preparing and writing the Mobile Telephone Forensic and Evidence BSc/MSc/PhD Degrees to be made available through Universities.
I have been involved with forensics and technology evidence for 22 years (1986-2007), of which 20 years with wireless evidence, and of which 14 years dealing with Global System for Mobile (GSM) communications evidence. The extent to which I have dealt with cellular/wireless evidence relates originally to the analogue mobile telephone system in the UK called TACS (Total Access Communications System) trial runs 1983 and launched 1985. This wireless system was phased out of use in the 1990s, although the last TACS wireless licence expired in 2005.
The predominant evidence for TACS related to investigating stolen and cloning mobile telephones. It required examination of the handset and transmitted identity to the network; the examination of the printed circuit boards for modification components or circuitry used to hijack the use of a genuine user's identity; to reprogram stolen identity into a stolen mobile and jettison original identity. To examine usage of stolen TACS mobile'phones in relation to Phonebook and mobile calls. To conduct cell site analysis based on the use of Masts by the stolen mobile 'phones and Masts radio coverage area. The last bulk of TACS mobile 'phone cases ended between 1997/98. This was largely due to the introduction of GSM in 1992 and the four fully operational GSM networks by 1994.
My work with GSM assisted in the introduction into evidence of the early GSM radio maps, called digital cell footprint maps but categorised as Best Server Plots/Density Maps and Single Cell Prediction Plots/Density Maps. This work with GSM began in 1993 with mobile telephone and SIM card examination, and GSM cell site analysis. In 1999 I created the first GSM accredited mobile telephone courses in the UK delivered in 2001 and in 2003 set about creating the first 3G USIM courses in the UK, which began in November 2005. My main skillsets are conducting research and development, data acquisition and harvesting, examining evidence but also presenting evidence in criminal courts of law, thus combining specialist R&D & evidential experience skillsets necessary when dealing with criminal proceedings.
Recently gave evidence to the House of Commons Home Affairs Select Committee - Terrorism Detention Powers relevant to mobile telephone evidence.
Appeared on Panorama to discuss Cell Site Analysis with respect to the Omagh Bombing 1988.
Gave evidence to the Omagh Inquiry held by the Intelligence Services Commissioner.
More info on Trew MTE courses: trewmte@googlemail.com
Currently Publications I produce:
Mobile Telephone Evidence (MTE) Newsletter
Mobile Telephone Surveillance (MTS) Newsletter
MTE Reports
Forensic Expert News (FEN)
Professional Communications Security Management (PCSM)
Past Publications
Professional Telephone Engineer and Installer
Telephone Times
Telephone News
Author
Admissibility of Computer Evidence in Criminal Proceedings
Understanding the European Community Phase II Directive
Implications of a regulatory framework for telecoms terminal equipment
European Telecommunications Approvals Process
The EMC Implications for type approval for telecommunications terminal equipment
Basic Overview of the Mobile Phone Network
Cloning SIM Cards
Cloning Mobile Phones
Access Control of Networks
PSTN Interface Requirements for Terminal Equipment
Telephone Installation: Keep it simply and legal
Profiting from Private Payphone
Meeting NETs Needs
Computer Evidence in Criminal Proceedings
Security Management - the evolution of standards
The path to Data Encryption and Cryptography
Network Management - Virus and other potential threats to the integrity of the network
Putting Britain First - A blueprint for the future control of public switched telephone network (PSTN)
(These are just a few of authored material over the years and some of the documents above are still available today)
Project Work
USIM Detective (available from Quantaq Solutions http://www.quantaq.com/). The work involved assisting the manufacturer to include forensic features and evidential standards.
I also run the only approved Accredited training for USIM Detective http://www.quantaq.com/ud_training.htm. This is a 3G training course.
Mobile Phone Forensics & Evidence training courses includes: introduction to mobile telephone examination, undersatnding the GSM/3G Standards, SIM/USIM examination, mobile phone examination, cell site analysis, interpretation of data.
Moderate the Mobile Forensics Forums at Forensic Focus:
http://www.forensicfocus.com/mobile-forensics-forum
Also run Mobile Telephone Case law:
http://www.forensicfocus.com/index.php?name=Forums&file=viewforum&f=18
Preparing and writing the Mobile Telephone Forensic and Evidence BSc/MSc/PhD Degrees to be made available through Universities.
Saturday, November 04, 2006
Mobile Telephone Evidence - Handset examination
Handset examination
For those who have not as yet considered the examination procedure for video-phones or mobiles that have no forensic data acquisition programs, perhaps the following observations may be of use.
1. Video the examination
2. Ensure video has date/timestamp and other traceable signatures
3. Keep the Master copy safe
4. Make Working copies from Master copy (see 7,8)
5. During examination, make sure examiner seen make contemporary notes
6. Ensure examiner seen referring to 3 handset user manual
7. Working copy: take Stills needed for evidence (inc date/timestamp etc)
8. Working copy: for defence
More info on Trew MTE mobile 'phone forensic training courses: trewmte@googlemail.com
For those who have not as yet considered the examination procedure for video-phones or mobiles that have no forensic data acquisition programs, perhaps the following observations may be of use.
1. Video the examination
2. Ensure video has date/timestamp and other traceable signatures
3. Keep the Master copy safe
4. Make Working copies from Master copy (see 7,8)
5. During examination, make sure examiner seen make contemporary notes
6. Ensure examiner seen referring to 3 handset user manual
7. Working copy: take Stills needed for evidence (inc date/timestamp etc)
8. Working copy: for defence
More info on Trew MTE mobile 'phone forensic training courses: trewmte@googlemail.com
Mobile Telephone Evidence - Video Evidence
VIDEO SURVEILLANCE
In response to numerous queries raised in 2003 about examining handsets with video or 'Still' images capability, where no effective tools are available to download images safely, it was suggested that examiners may well find it useful to video an examination. This was with respect to handsets designed for 3G-hybrid/GPRS/WAP/GSM technology enabled.
demonstrate images that were recovered were representative of the handset stored data and the output was a reliable representation.
The old adage of an independent examiner being able to reproduce the same results, whilst a useful tenet, was not the concern but how reasonably one could show, at first instance:
A) The procedures undertaken during the examination process
B) The recorded data that was recovered
C) To display the images accordingly.
This process is considered best practice in that it would enable an examiner, if challenged, to identify the procedures in handling evidence; the extraction processes; and which could support any contemporaneous notes made. It was foreseen that law enforcement might wish to serve images in 'Still' format, thus the time/date stamp, case reference, and authentication may also be recorded in a 'Still' image.
However, there might still be some additional policies that may not have been considered? In May 2003 the European Committee on Co-operation (CDCJ) adopted guiding principles for the protection of individuals with regard to the collection and processing of data by means of video surveillance (2003). The guidelines are applicable to data protection.
There are 12 guiding principles that have been adopted, which are recorded on Page 2 below, and which law enforcement might wish to clarify whether these adopted guidelines are applicable to evidence recorded on video during examination of particular handset data that may amount to video surveillance, for instance:
- where moving pictures stored in a handset record an individual or individuals, which are subsequently recorded to an evidential video. Or, where 'Still' images of the same are reproduced from an evidential video.
GUIDING PRINCIPLES
Any video surveillance activity should be undertaken by taking such measures as are necessary in order to ensure that this activity complies with personal data protection principles, in particular:
1) by ensuring that it is carried out in a fair and lawful manner for legitimate, specific, and explicit purposes. Personal data collected by means of video surveillance should not be further processed in a way incompatible with the purposes for which they were collected;
2) by only using video surveillance if, depending on the circumstances, the purpose cannot be attained by measures which interfere less with privacy, provided that the alternative measures would not involve disproportionate cost.
3) by making use of video surveillance in an adequate, relevant and non-excessive way with regard to the determined and specific purposes sought in the individual cases where there is a demonstrable need, in order to avoid any unintentional and unjustified infringement of the data subject's rights and fundamental freedoms, for example, the freedom of movement, and to ensure in particular respect of his privacy, even in public places;1
4) Video surveillance should be carried out in a way that does not make the persons recorded recognisable if the purpose of the processing does not require their possible identification;
5) by preventing the data collected from being indexed, matched or kept unnecessarily. When it proves necessary to keep data, these data must be deleted as soon as they are no longer necessary for the determined and specific purpose sought;
6) by refraining from video surveillance activities where the processing of the data would result in discrimination against certain data subjects or groups of data subjects exclusively on account of their political opinions, religious beliefs, health or sexual life, racial or ethnic origin;
7) by making clearly discernible in an appropriate manner that video surveillance is taking place, its purpose and the identity of the controller2 or by informing the data subject beforehand of the above. Other information,3 having regard to the specific circumstances, should be provided to the data subject, where this is necessary to guarantee fair processing of personal data and does not jeopardise the purpose of the surveillance;
8) by ensuring that during the storage period, the right of access to the data, and, where appropriate, the right of rectification, blocking and/or erasure, is granted to the data subject unless this would entail disproportionate effort;
9) by taking all technical or organisational measures necessary to safeguard the integrity of the collected information4;
10) In case of storage by the police of personal data by automatic means resulting from video surveillance, the principles of Recommendation No. R (87) 15 on the use of personal data in the police sector should furthermore be taken into account;
11) by limiting the use of video surveillance systems in the workplace to organisational and production requirements or to occupational safety purposes. This system should not be aimed at the systematic surveillance of the quality and quantity of individual performance in the workplace.
Employees or their representatives should be informed or consulted before the introduction or adaptation of a video surveillance system. Where the consultation procedure reveals a possibility of infringement of employees' right to respect for privacy and human dignity their agreement5 should be sought. In the event of a lawsuit or counterclaim, employees should be able to ground them on the recording made.
12) If personal data are recorded and kept, this should be done as far as possible in a way that allows data subjects to exercise their right of access, in accordance with data protection legislation, without obtaining information about other people.
Details about the 12 Guiding Principles can be found at the follow web URL:
http://www.coe.int/T/E/Legal_affairs/Legal_cooperation/Data_protection/Documents/Reports/10report%20guiding%20principles.asp#TopOfPage
In response to numerous queries raised in 2003 about examining handsets with video or 'Still' images capability, where no effective tools are available to download images safely, it was suggested that examiners may well find it useful to video an examination. This was with respect to handsets designed for 3G-hybrid/GPRS/WAP/GSM technology enabled.
demonstrate images that were recovered were representative of the handset stored data and the output was a reliable representation.
The old adage of an independent examiner being able to reproduce the same results, whilst a useful tenet, was not the concern but how reasonably one could show, at first instance:
A) The procedures undertaken during the examination process
B) The recorded data that was recovered
C) To display the images accordingly.
This process is considered best practice in that it would enable an examiner, if challenged, to identify the procedures in handling evidence; the extraction processes; and which could support any contemporaneous notes made. It was foreseen that law enforcement might wish to serve images in 'Still' format, thus the time/date stamp, case reference, and authentication may also be recorded in a 'Still' image.
However, there might still be some additional policies that may not have been considered? In May 2003 the European Committee on Co-operation (CDCJ) adopted guiding principles for the protection of individuals with regard to the collection and processing of data by means of video surveillance (2003). The guidelines are applicable to data protection.
There are 12 guiding principles that have been adopted, which are recorded on Page 2 below, and which law enforcement might wish to clarify whether these adopted guidelines are applicable to evidence recorded on video during examination of particular handset data that may amount to video surveillance, for instance:
- where moving pictures stored in a handset record an individual or individuals, which are subsequently recorded to an evidential video. Or, where 'Still' images of the same are reproduced from an evidential video.
GUIDING PRINCIPLES
Any video surveillance activity should be undertaken by taking such measures as are necessary in order to ensure that this activity complies with personal data protection principles, in particular:
1) by ensuring that it is carried out in a fair and lawful manner for legitimate, specific, and explicit purposes. Personal data collected by means of video surveillance should not be further processed in a way incompatible with the purposes for which they were collected;
2) by only using video surveillance if, depending on the circumstances, the purpose cannot be attained by measures which interfere less with privacy, provided that the alternative measures would not involve disproportionate cost.
3) by making use of video surveillance in an adequate, relevant and non-excessive way with regard to the determined and specific purposes sought in the individual cases where there is a demonstrable need, in order to avoid any unintentional and unjustified infringement of the data subject's rights and fundamental freedoms, for example, the freedom of movement, and to ensure in particular respect of his privacy, even in public places;1
4) Video surveillance should be carried out in a way that does not make the persons recorded recognisable if the purpose of the processing does not require their possible identification;
5) by preventing the data collected from being indexed, matched or kept unnecessarily. When it proves necessary to keep data, these data must be deleted as soon as they are no longer necessary for the determined and specific purpose sought;
6) by refraining from video surveillance activities where the processing of the data would result in discrimination against certain data subjects or groups of data subjects exclusively on account of their political opinions, religious beliefs, health or sexual life, racial or ethnic origin;
7) by making clearly discernible in an appropriate manner that video surveillance is taking place, its purpose and the identity of the controller2 or by informing the data subject beforehand of the above. Other information,3 having regard to the specific circumstances, should be provided to the data subject, where this is necessary to guarantee fair processing of personal data and does not jeopardise the purpose of the surveillance;
8) by ensuring that during the storage period, the right of access to the data, and, where appropriate, the right of rectification, blocking and/or erasure, is granted to the data subject unless this would entail disproportionate effort;
9) by taking all technical or organisational measures necessary to safeguard the integrity of the collected information4;
10) In case of storage by the police of personal data by automatic means resulting from video surveillance, the principles of Recommendation No. R (87) 15 on the use of personal data in the police sector should furthermore be taken into account;
11) by limiting the use of video surveillance systems in the workplace to organisational and production requirements or to occupational safety purposes. This system should not be aimed at the systematic surveillance of the quality and quantity of individual performance in the workplace.
Employees or their representatives should be informed or consulted before the introduction or adaptation of a video surveillance system. Where the consultation procedure reveals a possibility of infringement of employees' right to respect for privacy and human dignity their agreement5 should be sought. In the event of a lawsuit or counterclaim, employees should be able to ground them on the recording made.
12) If personal data are recorded and kept, this should be done as far as possible in a way that allows data subjects to exercise their right of access, in accordance with data protection legislation, without obtaining information about other people.
Details about the 12 Guiding Principles can be found at the follow web URL:
http://www.coe.int/T/E/Legal_affairs/Legal_cooperation/Data_protection/Documents/Reports/10report%20guiding%20principles.asp#TopOfPage
Article on SIM Card Readers
Article on SIM Card readers
http://www.ilexjournal.com/special_features/article.asp?theid=284&themode=2C
http://www.ilexjournal.com/special_features/article.asp?theid=284&themode=2C
Article on SIM Card Readers
Article on SIM Card readers
http://www.ilexjournal.com/special_features/article.asp?theid=284&themode=2C
http://www.ilexjournal.com/special_features/article.asp?theid=284&themode=2C
Cell phones do not disrupt navigation systems
Cell phones do not disrupt navigation systems
Tests by Airbus and American Airlines /Qualcomm indicate that, contrary to popular lore, cellular signals do not disrupt airplanes' navigational systems. The two results were similar for both the CDMA and GSM cellular technologies, but the Federal Aviation Administration and the Federal Communications Commission say the tests can't officially be considered in their review of the rules because they were conducted without government oversight. The agencies say they are moving ahead with their own tests (Wall Street Journal 23 Sep 2004)
Tests by Airbus and American Airlines /Qualcomm indicate that, contrary to popular lore, cellular signals do not disrupt airplanes' navigational systems. The two results were similar for both the CDMA and GSM cellular technologies, but the Federal Aviation Administration and the Federal Communications Commission say the tests can't officially be considered in their review of the rules because they were conducted without government oversight. The agencies say they are moving ahead with their own tests (Wall Street Journal 23 Sep 2004)
WHERE INTERCEPTION STOPS AND DATA PROTECTION STARTS?
WHERE INTERCEPTION STOPS AND DATA PROTECTION STARTS?
Professional examiners have been grappling for some months now with the task of trying to define what constitutes interception, when examining mobile 'phones. Most noticeably, the issues associated with received SMS text messages arriving after seizure or during examination, and downloading voicemail messages. There has been no shortage of takers defining what exactly an examiner can and cannot obtain and/or should or shouldn't do. It is not surprising
that currently various forces around the country implement a disparate range of ad hoc policies and procedures, which are subject to regular change. Fundamentally, the question of whether an examiner has any responsibility in this area at all appears to be largely overlooked. Significantly, it may well come down to professional examiners making a rod for their own backs by assuming responsibility and lawful duties that may actually be the burden of someone else.
Two cases that fairly recently emerged shed some very interesting light as to what the law may require in this area. Any discussion of them, here, is only by way of observation and clarification should really be sought from regional CPS departments. The first case that was kindly forwarded to me heard in April 2004 was R v X (CA 2004) concerning whether a listening device in a vehicle that recorded only one part of the mobile 'phone conversation amounted to unlawful interception. The second case United States Court of Appeals for the First Circuit No 03-1383. The latter case concerned whether emails copied, prior to receipt by the intended receiving party, by an ISP amounted to unlawful interception. Both cases may provide some assistance in those matters that currently vex professional examiners.
As an observation amalgamated from the findings in both cases, combined, they suggest it is less likely that a professional examiner would be conducting unlawful interception where text messages and voicemail are retrieved during examination. Moreover, if there is any legal issue that is more pressing, and in need of realisation, it is relevant to Data Protection. The rationale behind the observation is not made in isolation and simply based on the findings in these cases, but extends to applying the case rationale to technical realisations and implementations for mobile telephony.
Professional examiners have been grappling for some months now with the task of trying to define what constitutes interception, when examining mobile 'phones. Most noticeably, the issues associated with received SMS text messages arriving after seizure or during examination, and downloading voicemail messages. There has been no shortage of takers defining what exactly an examiner can and cannot obtain and/or should or shouldn't do. It is not surprising
that currently various forces around the country implement a disparate range of ad hoc policies and procedures, which are subject to regular change. Fundamentally, the question of whether an examiner has any responsibility in this area at all appears to be largely overlooked. Significantly, it may well come down to professional examiners making a rod for their own backs by assuming responsibility and lawful duties that may actually be the burden of someone else.
Two cases that fairly recently emerged shed some very interesting light as to what the law may require in this area. Any discussion of them, here, is only by way of observation and clarification should really be sought from regional CPS departments. The first case that was kindly forwarded to me heard in April 2004 was R v X (CA 2004) concerning whether a listening device in a vehicle that recorded only one part of the mobile 'phone conversation amounted to unlawful interception. The second case United States Court of Appeals for the First Circuit No 03-1383. The latter case concerned whether emails copied, prior to receipt by the intended receiving party, by an ISP amounted to unlawful interception. Both cases may provide some assistance in those matters that currently vex professional examiners.
As an observation amalgamated from the findings in both cases, combined, they suggest it is less likely that a professional examiner would be conducting unlawful interception where text messages and voicemail are retrieved during examination. Moreover, if there is any legal issue that is more pressing, and in need of realisation, it is relevant to Data Protection. The rationale behind the observation is not made in isolation and simply based on the findings in these cases, but extends to applying the case rationale to technical realisations and implementations for mobile telephony.
Deleted SMS text messages
Deleted SMS text messages
GSM 11.11 (ETSI TS 100 977) is a Standard containing mandatory and optional requirements relevant to Subscriber Identity Module (SIM) cards. An optional service that an Operator may provide to a subscriber of its services is Short Message Service (SMS) text messaging. The requirements relating to storing sent and received SMS text messages, in the user memory area of the SIM card, are identified at GSM 11.11 cl10.5.3. When a message that is received and is subsequently deleted by the user of the SIM, the user can no longer gain access to that data. The details about a particular SMS message that has been deleted are removed from the SIM's memory table thus the mobile telephone will no longer display the SIM details of that message to the user.
Although the details of the SMS text message are no longer accessible by the user, GSM 11.11 makes it clear the physical data relating to the entire text message may still be recorded on the card. GSM 11.11 procedure for "Erasure" of text messages states:
GSM 11.11 cl 11.5.2
"Erasure: The ME will select in the SIM the message area to be erased. Depending on the MMI, the message may be read before the area is marked as "free". After performing the updating procedure with EFSMS, the memory allocated to this short message in the SIM is made available for a new incoming message. The memory of the SIM may still contain the old message until a new message is stored in this area."
Using specialist examination tools it is therefore possible to recover erased (deleted) SMS text messages from a SIM card. Where a previously deleted message has been over-written by either new data allocated to the memory area previously occupied by the deleted data or the handset automatically over-writes as a function of its operating procedure (usually over-writes with 000000's) the erased (deleted) data in the SIM are no longer recoverable. Hopefully this
information will assist if you are asked is it possible can deleted text messages be recovered, and, if not recoverable, why not?
http://www.filebucket.net/files/1596_ooy39/SMS%20Text%20Messages.pdf
GSM 11.11 (ETSI TS 100 977) is a Standard containing mandatory and optional requirements relevant to Subscriber Identity Module (SIM) cards. An optional service that an Operator may provide to a subscriber of its services is Short Message Service (SMS) text messaging. The requirements relating to storing sent and received SMS text messages, in the user memory area of the SIM card, are identified at GSM 11.11 cl10.5.3. When a message that is received and is subsequently deleted by the user of the SIM, the user can no longer gain access to that data. The details about a particular SMS message that has been deleted are removed from the SIM's memory table thus the mobile telephone will no longer display the SIM details of that message to the user.
Although the details of the SMS text message are no longer accessible by the user, GSM 11.11 makes it clear the physical data relating to the entire text message may still be recorded on the card. GSM 11.11 procedure for "Erasure" of text messages states:
GSM 11.11 cl 11.5.2
"Erasure: The ME will select in the SIM the message area to be erased. Depending on the MMI, the message may be read before the area is marked as "free". After performing the updating procedure with EFSMS, the memory allocated to this short message in the SIM is made available for a new incoming message. The memory of the SIM may still contain the old message until a new message is stored in this area."
Using specialist examination tools it is therefore possible to recover erased (deleted) SMS text messages from a SIM card. Where a previously deleted message has been over-written by either new data allocated to the memory area previously occupied by the deleted data or the handset automatically over-writes as a function of its operating procedure (usually over-writes with 000000's) the erased (deleted) data in the SIM are no longer recoverable. Hopefully this
information will assist if you are asked is it possible can deleted text messages be recovered, and, if not recoverable, why not?
http://www.filebucket.net/files/1596_ooy39/SMS%20Text%20Messages.pdf
Deleted SMS text messages
Deleted SMS text messages
GSM 11.11 (ETSI TS 100 977) is a Standard containing mandatory and optional requirements relevant to Subscriber Identity Module (SIM) cards. An optional service that an Operator may provide to a subscriber of its services is Short Message Service (SMS) text messaging. The requirements relating to storing sent and received SMS text messages, in the user memory area of the SIM card, are identified at GSM 11.11 cl10.5.3. When a message that is received and is subsequently deleted by the user of the SIM, the user can no longer gain access to that data. The details about a particular SMS message that has been deleted are removed from the SIM's memory table thus the mobile telephone will no longer display the SIM details of that message to the user.
Although the details of the SMS text message are no longer accessible by the user, GSM 11.11 makes it clear the physical data relating to the entire text message may still be recorded on the card. GSM 11.11 procedure for "Erasure" of text messages states:
GSM 11.11 cl 11.5.2
"Erasure: The ME will select in the SIM the message area to be erased. Depending on the MMI, the message may be read before the area is marked as "free". After performing the updating procedure with EFSMS, the memory allocated to this short message in the SIM is made available for a new incoming message. The memory of the SIM may still contain the old message until a new message is stored in this area."
Using specialist examination tools it is therefore possible to recover erased (deleted) SMS text messages from a SIM card. Where a previously deleted message has been over-written by either new data allocated to the memory area previously occupied by the deleted data or the handset automatically over-writes as a function of its operating procedure (usually over-writes with 000000's) the erased (deleted) data in the SIM are no longer recoverable. Hopefully this
information will assist if you are asked is it possible can deleted text messages be recovered, and, if not recoverable, why not?
http://www.filebucket.net/files/1596_ooy39/SMS%20Text%20Messages.pdf
GSM 11.11 (ETSI TS 100 977) is a Standard containing mandatory and optional requirements relevant to Subscriber Identity Module (SIM) cards. An optional service that an Operator may provide to a subscriber of its services is Short Message Service (SMS) text messaging. The requirements relating to storing sent and received SMS text messages, in the user memory area of the SIM card, are identified at GSM 11.11 cl10.5.3. When a message that is received and is subsequently deleted by the user of the SIM, the user can no longer gain access to that data. The details about a particular SMS message that has been deleted are removed from the SIM's memory table thus the mobile telephone will no longer display the SIM details of that message to the user.
Although the details of the SMS text message are no longer accessible by the user, GSM 11.11 makes it clear the physical data relating to the entire text message may still be recorded on the card. GSM 11.11 procedure for "Erasure" of text messages states:
GSM 11.11 cl 11.5.2
"Erasure: The ME will select in the SIM the message area to be erased. Depending on the MMI, the message may be read before the area is marked as "free". After performing the updating procedure with EFSMS, the memory allocated to this short message in the SIM is made available for a new incoming message. The memory of the SIM may still contain the old message until a new message is stored in this area."
Using specialist examination tools it is therefore possible to recover erased (deleted) SMS text messages from a SIM card. Where a previously deleted message has been over-written by either new data allocated to the memory area previously occupied by the deleted data or the handset automatically over-writes as a function of its operating procedure (usually over-writes with 000000's) the erased (deleted) data in the SIM are no longer recoverable. Hopefully this
information will assist if you are asked is it possible can deleted text messages be recovered, and, if not recoverable, why not?
http://www.filebucket.net/files/1596_ooy39/SMS%20Text%20Messages.pdf
Ten more years of life in GSM, at least
Ten more years of life in GSM, at least
It is a personal view held, but I believe there is still 10 years of life left for GSM, and that is at the very least. That view is not arrived at by wishful thinking. World trends tend to indicate this transmission technology will run and run. Recently, reviewing the Annual report and analysis of competitive market conditions with respect to commercial mobile services, and the hearing into International settlements policy reform and international settlement rates, roaming termination charges alone are estimated at $50 billion worldwide. Putting aside financial revenue issues, there are still countries developing GSM networks (China's market, possibly the largest in the world). Equally, new GSM networks are being installed globally. All in all, to view the development of 3G in the UK as an immediate successor to GSM might be premature, and from a global perspective rather parochial viewpoint. In talking to some TSUs about examinations, approx. 12% of mobiles and SIMs are from overseas. Therefore mobile telephone evidence does not appear to be diminishing.
It is a personal view held, but I believe there is still 10 years of life left for GSM, and that is at the very least. That view is not arrived at by wishful thinking. World trends tend to indicate this transmission technology will run and run. Recently, reviewing the Annual report and analysis of competitive market conditions with respect to commercial mobile services, and the hearing into International settlements policy reform and international settlement rates, roaming termination charges alone are estimated at $50 billion worldwide. Putting aside financial revenue issues, there are still countries developing GSM networks (China's market, possibly the largest in the world). Equally, new GSM networks are being installed globally. All in all, to view the development of 3G in the UK as an immediate successor to GSM might be premature, and from a global perspective rather parochial viewpoint. In talking to some TSUs about examinations, approx. 12% of mobiles and SIMs are from overseas. Therefore mobile telephone evidence does not appear to be diminishing.
Mobile Telephone Evidence
MCC AND MNC CODES
As examination of SIM Cards and Handsets is on the increase internationally, thus roaming is relevant, the list below identifies Mobile Country Codes (e.g. 234) and Mobile Network Codes (e.g. 44) for global Mobile Operators. Please note the data are subject to change.
20201 Cosmote Greece
20205 Vodafone Greece
20209 Q-Telecom Greece
20210 Telestet Greece
20404 Vodafone Netherlands
20408 KPN Netherlands
20412 O2 Netherlands
20416 T-Mobile Netherlands
20420 Orange Netherlands
20601 Proximus Belgium
20610 Mobistar Belgium
20620 Base Belgium
20801 Orange France
20810 SFR France
20820 Bouygtel Telecom France
21303 S.T.A. MobilAnd Andorra
21401 Vodafone Spain
21402 Movistar Spain
21403 Amena Spain
21404 Xfera Spain
21407 Telefonica Movistar Spain
21601 Pannon GSM Hungary
21630 Westel 900 GSM Mobile Hungary
21670 Vodafone Hungary
21803 Eronet Bosnia Herzegovina
21805 Mobi's Bosnia Herzegovina
21890 GSM BIH Bosnia Herzegovina
21901 Croatian Telecoms Cronet Croatia
21910 VIP Croatia
22001 MOBTEL Yugoslavia
22002 ProMonte GSM Yugoslavia
22003 03 Yugoslavia
22004 Monet Yugoslavia
22201 Telecom Italia Mobile TIM Italy
22210 Vodafone Italy
22288 Wind Telecomunicazioni Italy
22298 BLU Italy
22299 3 Italy
22601 MobiFon CONNEX GSM Romania
22603 Cosmorom Romania
22610 Mobil Rom DIALOG Romania
22801 Swisscom NATEL Switzerland
22802 Sunrise Switzerland
22803 Orange Switzerland
23001 T-mobile Czech Republic
23002 EuroTel Praha Czech Republic
23003 Oskar Czech Republic
23101 Orange GSM Slovak Republic
23102 EuroTel GSM Slovak Republic
23201 MobilKom Austria A1 Austria
23203 T-Mobile Austria
23205 Connect Austria One Austria
23207 Tele.ring Austria
23210 3AT Austria
23400001 Virgin United Kingdom
23410 02 United Kingdom
23415 Vodafone United Kingdom
23420 3 United Kingdom
23430 Virgin United Kigndom (others)
23430 T-Mobile United Kingdom
23433 Orange United Kingdom
23450 Jersey Telecom GSM United Kingdom
23455 Guernsey Telecoms GSM UK
23458 Manx Telecom Pronto GSM UK
23800001 Debitel Denmark
23801 Tele-Danmark Mobil Denmark
23802 Sonofon Denmark
23820 Telia Denmark Denmark
23830 Orange Denmark
24001 Telia Mobitel Sweden
24002 3 Sweden
24003 Orange Sweden
24007 Comviq GSM Sweden
24008 Vodafone Sweden
24201 Telenor Mobil Norway
24202 NetCom GSM Norway
24403 Telia Finland Finland
24405 Radiolinja Finland
24407 AT&T U.S.A.
24409 Finnet Group Finland
24412 2G Finland
24414 AMT Finland
24491 Sonera Corporation Finland
24601 Omnitel Lithuania
24602 UAB Bite GSM Lithuania
24603 Tele 2 Lithuania
24701 Latvian Mobile Tel. Latvia
24702 Tele 2 Latvia
24801 Estonian Mobile Telephone Estonia
24802 RadioLinja Eesti Estonia
24803 Tele 2 Estonia
25001 MTS Moscow Russia
25002 Megafon Russia
25005 Siberian Cellular Russia
25007 Zao Smarts Russia
25010 Don Telecom Russia
25012 New Telephone Company Russia
25013 Kuban GSM Russia
25039 Uratel Russia
25044 North Caucasian GSM Russia
25099 BeeLine Russia
25501 Ukrainian Mobile Comms Ukraine
25502 Ukrainian Radio Systems Ukraine
25503 Kyivstar GSM Ukraine
25505 Golden Telecom Ukraine
25701 Velcom
25702 MTS
25901 Voxtel Moldova
25902 Moldcell Moldova
26001 Polkomtel PLUS GSM Poland
26002 ERA GSM Poland
26003 IDEA Centertel Poland
26201 T-Mobile Germany
26202 Vodafone Germany
26203 E-Plus Mobilfunk Germany
26207 O2 Germany
26213 MobilCom Germany
26214 Quam Germany
26601 Gibraltar Telecoms Gibtel Gibraltar
26801 Vodafone Portugal
26803 Optimus Telecom. Portugal
26806 Telecom Moveis Nac. TMN Portugal
27001 P+T LUXGSM Luxembourg
27077 Millicom Tango GSM Luxembourg
27201 Vodafone Ireland
27202 O2 Ireland
27203 Meteor Ireland
27401 Iceland Telecom Siminn Iceland
27402 TAL hf Iceland
27403 Islandss Iceland
27404 Viking Iceland
27601 Albanian Mobile Comms Albania
27602 Vodafone Albania
27801 Vodafone Malta
27821 Go Mobile Malta
28001 Cyprus Telecoms Authority Cyprus
28201 Geocell Limited Georgia
28202 Magti GSM Georgia
28203 Geo 03 Georgia
28301 ArmenTel Armenia
28401 MobilTel AD Bulgaria
28405 Globul Bulgaria
28601 Turkcell Turkey
28602 TELSIM Turkey
28603 Aria Turkey
28604 Aycell Turkey
28801 FT-GSM
28802 KALL
29001 Tele Greenland Greenland
29340 Si.mobil Slovenia
29341 Si-GSM Slovenia
29370 Si VEGA 070 Slovenia
29401 MobiMak Macedonia
29402 MTS AD Macedonia
29501 Telecom
29502 Montel
29505 FL1
29577 Tango
30200001 Fido Canada
30237 Microcell Connexions Inc Canada
30272 Rogers AT&T Canada
31001 Pacific Mobile Comms Pap New Guinea
31002 APC Sprint Spectrum U.S.A.
31011 Wireless 2000 Telephone U.S.A.
31015 BellSouth Mobility DCS U.S.A.
31017 Cingular (Pacific Bell Wireless) U.S.A.
31020 T-Mobile U.S.A.
31026 Western Wireless Voicestream U.S.A.
31027 Powertel U.S.A.
31031 Aerial Communications U.S.A.
31038 AT&T U.S.A.
31077 Iowa Wireless Services U.S.A.
33805 Digicel JM
34001 Orange French West Indies
34020 BouygTel French West Indies
36801 C-Com CU
37412 TSTT
40001 Acell Telekom B.M. Azerbaijan
40002 BKcell GSM 2000 Azerbaijan
40101 K-Mobile Kazaksthan
40102 KCELL Kazaksthan
40217 B-Mobile BT
40401 Aircel Digilink Essar Cellph. India
40402 Bharti Cellular Telecom Airtel India
40403 Bharti Cellular Telecom Airtel India
40405 Hutch India
40407 TATA Cellular India
40408 Ushafon India
40410 Bharti Cellular Telecom Airtel India
40411 Hutch India
40412 Escotel Mobile Comms India
40413 Hutch India
40414 Ina Spice India
40415 Aircel Digilink Essar Cellph. India
40419 Escotel India
40420 Orange India
40421 BPL USWest Cellular India
40422 Idea India
40423 Usha Martin Tel. Command India
40424 Idea India
40426 Usha Martin Tel. Command India
40427 BPL USWest Cellular India
40430 Usha Martin Tel. Command India
40431 Bharti Cellular Telecom Airtel India
40432 Ushafone India
40434 BPL USWest Cellular India
40438 BPL USWest Cellular India
40440 INA AIRTel India
40441 RPG MAA India
40442 Srinivas Cellcom India
40443 BPL USWest Cellular India
40444 Spice India
40445 Bharti Cellular Telecom Airtel India
40446 BPL USWest Cellular India
40449 Bharti Cellular Telecom Airtel India
40451,53,54,55 BSNL Mobile India
40456 Escotel India
40457,58,59 BSNL Mobile India
40460 Aircel Digilink Essar Cellph. India
40462,64,66 BSNL Mobile India
40468 Dolphin India
40469 Dolphin India
40470 Oasis India
40471,72,73,74,75,76,77 BSNL Mobile India
40478 IDEA India
40479,80,81 BSNL Mobile India
40486 Hutch India
40490,92,93,94,95,96,97,98 Bharti Cellular
Telecom Airtel India
41001 Ufone Pakistan
41201 AWCC AF
41302 MTN Networks Dialog GSM Sri Lanka
41303 CellTel Sri Lanka
41401 MPTGSM
41501 FTML Cellis Lebanon
41503 LibanCell Lebanon
41601 J.M.T.S Fastlink Jordan
41677 MobCom Jordan
41701 SyriaTel Syria
41702 94 Syria
41709 MOBILE Syrian Telecom Est. Syria
41793 SyriaTel Syria
41801 Iraq Telecom Iraq
41902 Mobile Telecoms MTCNet Kuwait
41903 Wataniya Kuwait
42001 Ministry of PTT Al Jawal Saudi Arabia
42007 Electronics App' Est. EAE Saudi Arabia
42202 General Telecoms Oman
42401 UAE ETISALAT-G1 United Arab Emirates
42402 UAE ETISALAT-G2 United Arab Emirates
42501 Orange Israel
42502 Cellcom Israel
42505 JAWWAL Israel
42601 Batelco Bahrain
42701 QATARNET Qatar
42899 MobiCom MN
43211 TCI Iran
43214 Kish Iran
43400 Uzmacom Uzbekistan
43401 Buztel Uzbekistan
43402 Uzmacom Uzbekistan
43404 Daewoo Unitel Uzbekistan
43405 Coscom Uzbekistan
43407 UZD Uzbekistan
43603 MLT TJK
43605 TajikTel
43701 Bitel Kyrgyz Republic
44010 DoCoMo Japan
45201 Mobifone Vietnam
45202 Vinaphone Vietnam
45400 Hong Kong Telecom CSL Hong Kong
45404 Hutchison Telecom Hong Kong
45406 SmarTone Mobile Comms Hong Kong
45410 New World PCS Hong Kong
45412 Peoples Telephone Hong Kong
45416 Mandarin Com. Sunday Hong Kong
45418 Pacific Link Hong Kong
45422 P Plus Comm Hong Kong
45501 C.T.M. TELEMOVEL+ Macau
45601 Mobitel Cambodia
45602 SM Cambodia
45618 Camshin Cambodia
45701 Lao Shinawatra Telecom Lao
45702 ETLMNW Lao
45703 LatMil Lao
45708 Tango Lao
46000 China Telecom GSM China
46001 China Unicom GSM China
46002 Liaoning PPTA China
46601 Far EasTone Telecoms Taiwan
46606 TUNTEX Telecom Taiwan
46688 KG Telecom Taiwan
46692 Chunghwa Telecom Taiwan
46693 Mobitai Communications Taiwan
46697 Pacific Cellular TWNGSM Taiwan
46699 TransAsia Telecoms Taiwan
46701 Sun KP PRK
47001 Grameen Phone Bangladesh
47002 Aktel Bangladesh
47003 Sheba Telecom Bangladesh
47201 DHI Mobile MV
50202 Binariang Malaysia
50212 Maxis Malaysia
50213 Telekom Cellular TM Touch Malaysia
50216 DiGi Telecommunications Malaysia
50217 TimeCel Wireless Adam Malaysia
50219 Celcom Malaysia
50501 Telstra Mobile Comms Australia
50502 Optus Australia
50503 Vodafone Australia
50503 3 Australia
50508 OneTel Australia
51001 PT. SATelindo C Indonesia
51008 Lippo Telkomsel Indonesia
51010 TelKomSel Indonesia
51011 Pro XL Indonesia
51021 IM3 Indonesia
51501 Isla Comms Philippines
51502 Globe Telecom Philippines
51503 Smart Communications Philippines
51505 DigiTel Philippines
52001 Advanced Info Service AIS Thailand
52010 Orange Thailand
52018 DTotal Access Worldphone Thailand
52023 GSM 1800 Thailand
52099 Orange Thailand
52501 Sing. Tel. GSM 900 Singapore
52502 Sing. Tel. GSM 1800 Singapore
52503 MobileOne Asia Singapore
52504 M1-3GSM Singapore
52505 StarHub Singapore
52811 DST Communications Brunei Darussalam
53001 Vodafone New Zealand
53901 O-Call ton
54101 Smile VUT
54201 Vodafone Fiji Fiji
54601 Mobilis New Caledonia
54720 Vini French Polynesia
55001 FSM Telecom FSM
60201 MobiNil Egypt
60202 Vodafone Egypt
60301 Algerian Mobile Network Algeria
60302 Djezzy Algeria
60400 Meditel Marocco
60401 Itissalat Al-Maghrib IAM Marocco
60502 Tunisie Telecom Tunicell Tunisia
60503 Tunisiana Tunisia
60701 GamCel GMB
60702 AfriCELL GMB
60801 Sonatel ALIZE Senegal
60802 Sentel Senegal
60901 Mattel MR
61001 Matitel ML
61002 Ikatel ML
61201 Comstar Cellular Network Cote d'Ivoire
61203 Orange Cote d'Ivoire
61205 Telecel Cote d'Ivoire
61302 CelTel BF
61402 CelTel NE
61501 Togo Telecom TOGO CELL Togo
61602 TLCL-Ben BJ
61603 Benincell BJ
61604 BBcom BJ
61701 Cellplus Mobile Comms Mauritius
61710 Emtel Mauritius
61801 Lonestar Liberia
62001 ScanCom Ghana
62002 OneToch Ghana
62003 Mobitel Ghana
62120 Econet NG
62130 MTN NG
62140 Nitel NG
62201 CelTel TC
62202 Libertis TD
62401 MTN Cameroon
62402 Orange Cameroon
62501 Cabo Verde Movel Cape Verde
62601 CSTMovel STP
62701 GNQ01 GNQ
62801 Libertis GA
62802 GAB TeleCel
62803 CelTel GA
62901 CelTel CD
62910 Libertis CD
63002 CelTel RC
63004 CellCo GSM RC
63089 OASIS
63102 Unitel AGO
63301 Seychelles Cellular Services Seychelles
63310 AIRTEL Seychelles
63401 Mobile Telephone Company Sudan
63510 Rwandacell Rwanda
63601 Ethiopian Telecoms Auth. Ethiopia
63701 Barakaat SOM
63782 Telsom SOM
63902 Safaricom KE
63903 KenCell KE
64001 Tritel Tanzania
64002 Mobitel Tanzania
64003 Zantel Tanzania
64005 CelTel Tanzania
64101 Celtel Cellular Uganda
64110 MTN Uganda Uganda
64111 UTL Telecel Uganda
64201 Spacetel BI
64202 Busafa BI
64301 mCel MOZ
64501 Celtel Zambia
64601 Madacom Madagascar
64602 SMM Antaris Madagascar
64603 Sacel Madagascar
64700 Orange
64702 OMT
64710 Societe Reunionnaise SRR Reunion
64801 NET*ONE Zimbabwe
64803 Telecel Zimbabwe
64804 Econet Zimbabwe
64901 MTC Namibia
65001 Telekom Network Callpoint Malawi
65010 CelTel Malawi
65101 VCL Comms Lesotho
65102 Ezi Cel Lesothp
65201 Mascom Wireless Botswana
65202 Vista Botswana
65310 Swazi MTN SZ
65501 Vodacom South Africa
65507 Cell C South Africa
65510 MTN South Africa
71201 ICE CRI
72235 Port Hable ARG
72402,03,04 TIM Brazil
72431 Oi Brazil
732101 Comcel Columbia
73401 Infonet Venezuela
73402 Digitel Venezuela
74601 ICMS SR
74602 TeleG SR
As examination of SIM Cards and Handsets is on the increase internationally, thus roaming is relevant, the list below identifies Mobile Country Codes (e.g. 234) and Mobile Network Codes (e.g. 44) for global Mobile Operators. Please note the data are subject to change.
20201 Cosmote Greece
20205 Vodafone Greece
20209 Q-Telecom Greece
20210 Telestet Greece
20404 Vodafone Netherlands
20408 KPN Netherlands
20412 O2 Netherlands
20416 T-Mobile Netherlands
20420 Orange Netherlands
20601 Proximus Belgium
20610 Mobistar Belgium
20620 Base Belgium
20801 Orange France
20810 SFR France
20820 Bouygtel Telecom France
21303 S.T.A. MobilAnd Andorra
21401 Vodafone Spain
21402 Movistar Spain
21403 Amena Spain
21404 Xfera Spain
21407 Telefonica Movistar Spain
21601 Pannon GSM Hungary
21630 Westel 900 GSM Mobile Hungary
21670 Vodafone Hungary
21803 Eronet Bosnia Herzegovina
21805 Mobi's Bosnia Herzegovina
21890 GSM BIH Bosnia Herzegovina
21901 Croatian Telecoms Cronet Croatia
21910 VIP Croatia
22001 MOBTEL Yugoslavia
22002 ProMonte GSM Yugoslavia
22003 03 Yugoslavia
22004 Monet Yugoslavia
22201 Telecom Italia Mobile TIM Italy
22210 Vodafone Italy
22288 Wind Telecomunicazioni Italy
22298 BLU Italy
22299 3 Italy
22601 MobiFon CONNEX GSM Romania
22603 Cosmorom Romania
22610 Mobil Rom DIALOG Romania
22801 Swisscom NATEL Switzerland
22802 Sunrise Switzerland
22803 Orange Switzerland
23001 T-mobile Czech Republic
23002 EuroTel Praha Czech Republic
23003 Oskar Czech Republic
23101 Orange GSM Slovak Republic
23102 EuroTel GSM Slovak Republic
23201 MobilKom Austria A1 Austria
23203 T-Mobile Austria
23205 Connect Austria One Austria
23207 Tele.ring Austria
23210 3AT Austria
23400001 Virgin United Kingdom
23410 02 United Kingdom
23415 Vodafone United Kingdom
23420 3 United Kingdom
23430 Virgin United Kigndom (others)
23430 T-Mobile United Kingdom
23433 Orange United Kingdom
23450 Jersey Telecom GSM United Kingdom
23455 Guernsey Telecoms GSM UK
23458 Manx Telecom Pronto GSM UK
23800001 Debitel Denmark
23801 Tele-Danmark Mobil Denmark
23802 Sonofon Denmark
23820 Telia Denmark Denmark
23830 Orange Denmark
24001 Telia Mobitel Sweden
24002 3 Sweden
24003 Orange Sweden
24007 Comviq GSM Sweden
24008 Vodafone Sweden
24201 Telenor Mobil Norway
24202 NetCom GSM Norway
24403 Telia Finland Finland
24405 Radiolinja Finland
24407 AT&T U.S.A.
24409 Finnet Group Finland
24412 2G Finland
24414 AMT Finland
24491 Sonera Corporation Finland
24601 Omnitel Lithuania
24602 UAB Bite GSM Lithuania
24603 Tele 2 Lithuania
24701 Latvian Mobile Tel. Latvia
24702 Tele 2 Latvia
24801 Estonian Mobile Telephone Estonia
24802 RadioLinja Eesti Estonia
24803 Tele 2 Estonia
25001 MTS Moscow Russia
25002 Megafon Russia
25005 Siberian Cellular Russia
25007 Zao Smarts Russia
25010 Don Telecom Russia
25012 New Telephone Company Russia
25013 Kuban GSM Russia
25039 Uratel Russia
25044 North Caucasian GSM Russia
25099 BeeLine Russia
25501 Ukrainian Mobile Comms Ukraine
25502 Ukrainian Radio Systems Ukraine
25503 Kyivstar GSM Ukraine
25505 Golden Telecom Ukraine
25701 Velcom
25702 MTS
25901 Voxtel Moldova
25902 Moldcell Moldova
26001 Polkomtel PLUS GSM Poland
26002 ERA GSM Poland
26003 IDEA Centertel Poland
26201 T-Mobile Germany
26202 Vodafone Germany
26203 E-Plus Mobilfunk Germany
26207 O2 Germany
26213 MobilCom Germany
26214 Quam Germany
26601 Gibraltar Telecoms Gibtel Gibraltar
26801 Vodafone Portugal
26803 Optimus Telecom. Portugal
26806 Telecom Moveis Nac. TMN Portugal
27001 P+T LUXGSM Luxembourg
27077 Millicom Tango GSM Luxembourg
27201 Vodafone Ireland
27202 O2 Ireland
27203 Meteor Ireland
27401 Iceland Telecom Siminn Iceland
27402 TAL hf Iceland
27403 Islandss Iceland
27404 Viking Iceland
27601 Albanian Mobile Comms Albania
27602 Vodafone Albania
27801 Vodafone Malta
27821 Go Mobile Malta
28001 Cyprus Telecoms Authority Cyprus
28201 Geocell Limited Georgia
28202 Magti GSM Georgia
28203 Geo 03 Georgia
28301 ArmenTel Armenia
28401 MobilTel AD Bulgaria
28405 Globul Bulgaria
28601 Turkcell Turkey
28602 TELSIM Turkey
28603 Aria Turkey
28604 Aycell Turkey
28801 FT-GSM
28802 KALL
29001 Tele Greenland Greenland
29340 Si.mobil Slovenia
29341 Si-GSM Slovenia
29370 Si VEGA 070 Slovenia
29401 MobiMak Macedonia
29402 MTS AD Macedonia
29501 Telecom
29502 Montel
29505 FL1
29577 Tango
30200001 Fido Canada
30237 Microcell Connexions Inc Canada
30272 Rogers AT&T Canada
31001 Pacific Mobile Comms Pap New Guinea
31002 APC Sprint Spectrum U.S.A.
31011 Wireless 2000 Telephone U.S.A.
31015 BellSouth Mobility DCS U.S.A.
31017 Cingular (Pacific Bell Wireless) U.S.A.
31020 T-Mobile U.S.A.
31026 Western Wireless Voicestream U.S.A.
31027 Powertel U.S.A.
31031 Aerial Communications U.S.A.
31038 AT&T U.S.A.
31077 Iowa Wireless Services U.S.A.
33805 Digicel JM
34001 Orange French West Indies
34020 BouygTel French West Indies
36801 C-Com CU
37412 TSTT
40001 Acell Telekom B.M. Azerbaijan
40002 BKcell GSM 2000 Azerbaijan
40101 K-Mobile Kazaksthan
40102 KCELL Kazaksthan
40217 B-Mobile BT
40401 Aircel Digilink Essar Cellph. India
40402 Bharti Cellular Telecom Airtel India
40403 Bharti Cellular Telecom Airtel India
40405 Hutch India
40407 TATA Cellular India
40408 Ushafon India
40410 Bharti Cellular Telecom Airtel India
40411 Hutch India
40412 Escotel Mobile Comms India
40413 Hutch India
40414 Ina Spice India
40415 Aircel Digilink Essar Cellph. India
40419 Escotel India
40420 Orange India
40421 BPL USWest Cellular India
40422 Idea India
40423 Usha Martin Tel. Command India
40424 Idea India
40426 Usha Martin Tel. Command India
40427 BPL USWest Cellular India
40430 Usha Martin Tel. Command India
40431 Bharti Cellular Telecom Airtel India
40432 Ushafone India
40434 BPL USWest Cellular India
40438 BPL USWest Cellular India
40440 INA AIRTel India
40441 RPG MAA India
40442 Srinivas Cellcom India
40443 BPL USWest Cellular India
40444 Spice India
40445 Bharti Cellular Telecom Airtel India
40446 BPL USWest Cellular India
40449 Bharti Cellular Telecom Airtel India
40451,53,54,55 BSNL Mobile India
40456 Escotel India
40457,58,59 BSNL Mobile India
40460 Aircel Digilink Essar Cellph. India
40462,64,66 BSNL Mobile India
40468 Dolphin India
40469 Dolphin India
40470 Oasis India
40471,72,73,74,75,76,77 BSNL Mobile India
40478 IDEA India
40479,80,81 BSNL Mobile India
40486 Hutch India
40490,92,93,94,95,96,97,98 Bharti Cellular
Telecom Airtel India
41001 Ufone Pakistan
41201 AWCC AF
41302 MTN Networks Dialog GSM Sri Lanka
41303 CellTel Sri Lanka
41401 MPTGSM
41501 FTML Cellis Lebanon
41503 LibanCell Lebanon
41601 J.M.T.S Fastlink Jordan
41677 MobCom Jordan
41701 SyriaTel Syria
41702 94 Syria
41709 MOBILE Syrian Telecom Est. Syria
41793 SyriaTel Syria
41801 Iraq Telecom Iraq
41902 Mobile Telecoms MTCNet Kuwait
41903 Wataniya Kuwait
42001 Ministry of PTT Al Jawal Saudi Arabia
42007 Electronics App' Est. EAE Saudi Arabia
42202 General Telecoms Oman
42401 UAE ETISALAT-G1 United Arab Emirates
42402 UAE ETISALAT-G2 United Arab Emirates
42501 Orange Israel
42502 Cellcom Israel
42505 JAWWAL Israel
42601 Batelco Bahrain
42701 QATARNET Qatar
42899 MobiCom MN
43211 TCI Iran
43214 Kish Iran
43400 Uzmacom Uzbekistan
43401 Buztel Uzbekistan
43402 Uzmacom Uzbekistan
43404 Daewoo Unitel Uzbekistan
43405 Coscom Uzbekistan
43407 UZD Uzbekistan
43603 MLT TJK
43605 TajikTel
43701 Bitel Kyrgyz Republic
44010 DoCoMo Japan
45201 Mobifone Vietnam
45202 Vinaphone Vietnam
45400 Hong Kong Telecom CSL Hong Kong
45404 Hutchison Telecom Hong Kong
45406 SmarTone Mobile Comms Hong Kong
45410 New World PCS Hong Kong
45412 Peoples Telephone Hong Kong
45416 Mandarin Com. Sunday Hong Kong
45418 Pacific Link Hong Kong
45422 P Plus Comm Hong Kong
45501 C.T.M. TELEMOVEL+ Macau
45601 Mobitel Cambodia
45602 SM Cambodia
45618 Camshin Cambodia
45701 Lao Shinawatra Telecom Lao
45702 ETLMNW Lao
45703 LatMil Lao
45708 Tango Lao
46000 China Telecom GSM China
46001 China Unicom GSM China
46002 Liaoning PPTA China
46601 Far EasTone Telecoms Taiwan
46606 TUNTEX Telecom Taiwan
46688 KG Telecom Taiwan
46692 Chunghwa Telecom Taiwan
46693 Mobitai Communications Taiwan
46697 Pacific Cellular TWNGSM Taiwan
46699 TransAsia Telecoms Taiwan
46701 Sun KP PRK
47001 Grameen Phone Bangladesh
47002 Aktel Bangladesh
47003 Sheba Telecom Bangladesh
47201 DHI Mobile MV
50202 Binariang Malaysia
50212 Maxis Malaysia
50213 Telekom Cellular TM Touch Malaysia
50216 DiGi Telecommunications Malaysia
50217 TimeCel Wireless Adam Malaysia
50219 Celcom Malaysia
50501 Telstra Mobile Comms Australia
50502 Optus Australia
50503 Vodafone Australia
50503 3 Australia
50508 OneTel Australia
51001 PT. SATelindo C Indonesia
51008 Lippo Telkomsel Indonesia
51010 TelKomSel Indonesia
51011 Pro XL Indonesia
51021 IM3 Indonesia
51501 Isla Comms Philippines
51502 Globe Telecom Philippines
51503 Smart Communications Philippines
51505 DigiTel Philippines
52001 Advanced Info Service AIS Thailand
52010 Orange Thailand
52018 DTotal Access Worldphone Thailand
52023 GSM 1800 Thailand
52099 Orange Thailand
52501 Sing. Tel. GSM 900 Singapore
52502 Sing. Tel. GSM 1800 Singapore
52503 MobileOne Asia Singapore
52504 M1-3GSM Singapore
52505 StarHub Singapore
52811 DST Communications Brunei Darussalam
53001 Vodafone New Zealand
53901 O-Call ton
54101 Smile VUT
54201 Vodafone Fiji Fiji
54601 Mobilis New Caledonia
54720 Vini French Polynesia
55001 FSM Telecom FSM
60201 MobiNil Egypt
60202 Vodafone Egypt
60301 Algerian Mobile Network Algeria
60302 Djezzy Algeria
60400 Meditel Marocco
60401 Itissalat Al-Maghrib IAM Marocco
60502 Tunisie Telecom Tunicell Tunisia
60503 Tunisiana Tunisia
60701 GamCel GMB
60702 AfriCELL GMB
60801 Sonatel ALIZE Senegal
60802 Sentel Senegal
60901 Mattel MR
61001 Matitel ML
61002 Ikatel ML
61201 Comstar Cellular Network Cote d'Ivoire
61203 Orange Cote d'Ivoire
61205 Telecel Cote d'Ivoire
61302 CelTel BF
61402 CelTel NE
61501 Togo Telecom TOGO CELL Togo
61602 TLCL-Ben BJ
61603 Benincell BJ
61604 BBcom BJ
61701 Cellplus Mobile Comms Mauritius
61710 Emtel Mauritius
61801 Lonestar Liberia
62001 ScanCom Ghana
62002 OneToch Ghana
62003 Mobitel Ghana
62120 Econet NG
62130 MTN NG
62140 Nitel NG
62201 CelTel TC
62202 Libertis TD
62401 MTN Cameroon
62402 Orange Cameroon
62501 Cabo Verde Movel Cape Verde
62601 CSTMovel STP
62701 GNQ01 GNQ
62801 Libertis GA
62802 GAB TeleCel
62803 CelTel GA
62901 CelTel CD
62910 Libertis CD
63002 CelTel RC
63004 CellCo GSM RC
63089 OASIS
63102 Unitel AGO
63301 Seychelles Cellular Services Seychelles
63310 AIRTEL Seychelles
63401 Mobile Telephone Company Sudan
63510 Rwandacell Rwanda
63601 Ethiopian Telecoms Auth. Ethiopia
63701 Barakaat SOM
63782 Telsom SOM
63902 Safaricom KE
63903 KenCell KE
64001 Tritel Tanzania
64002 Mobitel Tanzania
64003 Zantel Tanzania
64005 CelTel Tanzania
64101 Celtel Cellular Uganda
64110 MTN Uganda Uganda
64111 UTL Telecel Uganda
64201 Spacetel BI
64202 Busafa BI
64301 mCel MOZ
64501 Celtel Zambia
64601 Madacom Madagascar
64602 SMM Antaris Madagascar
64603 Sacel Madagascar
64700 Orange
64702 OMT
64710 Societe Reunionnaise SRR Reunion
64801 NET*ONE Zimbabwe
64803 Telecel Zimbabwe
64804 Econet Zimbabwe
64901 MTC Namibia
65001 Telekom Network Callpoint Malawi
65010 CelTel Malawi
65101 VCL Comms Lesotho
65102 Ezi Cel Lesothp
65201 Mascom Wireless Botswana
65202 Vista Botswana
65310 Swazi MTN SZ
65501 Vodacom South Africa
65507 Cell C South Africa
65510 MTN South Africa
71201 ICE CRI
72235 Port Hable ARG
72402,03,04 TIM Brazil
72431 Oi Brazil
732101 Comcel Columbia
73401 Infonet Venezuela
73402 Digitel Venezuela
74601 ICMS SR
74602 TeleG SR
Mobile Telephone Evidence
MCC AND MNC CODES
As examination of SIM Cards and Handsets is on the increase internationally, thus roaming is relevant, the list below identifies Mobile Country Codes (e.g. 234) and Mobile Network Codes (e.g. 44) for global Mobile Operators. Please note the data are subject to change.
20201 Cosmote Greece
20205 Vodafone Greece
20209 Q-Telecom Greece
20210 Telestet Greece
20404 Vodafone Netherlands
20408 KPN Netherlands
20412 O2 Netherlands
20416 T-Mobile Netherlands
20420 Orange Netherlands
20601 Proximus Belgium
20610 Mobistar Belgium
20620 Base Belgium
20801 Orange France
20810 SFR France
20820 Bouygtel Telecom France
21303 S.T.A. MobilAnd Andorra
21401 Vodafone Spain
21402 Movistar Spain
21403 Amena Spain
21404 Xfera Spain
21407 Telefonica Movistar Spain
21601 Pannon GSM Hungary
21630 Westel 900 GSM Mobile Hungary
21670 Vodafone Hungary
21803 Eronet Bosnia Herzegovina
21805 Mobi's Bosnia Herzegovina
21890 GSM BIH Bosnia Herzegovina
21901 Croatian Telecoms Cronet Croatia
21910 VIP Croatia
22001 MOBTEL Yugoslavia
22002 ProMonte GSM Yugoslavia
22003 03 Yugoslavia
22004 Monet Yugoslavia
22201 Telecom Italia Mobile TIM Italy
22210 Vodafone Italy
22288 Wind Telecomunicazioni Italy
22298 BLU Italy
22299 3 Italy
22601 MobiFon CONNEX GSM Romania
22603 Cosmorom Romania
22610 Mobil Rom DIALOG Romania
22801 Swisscom NATEL Switzerland
22802 Sunrise Switzerland
22803 Orange Switzerland
23001 T-mobile Czech Republic
23002 EuroTel Praha Czech Republic
23003 Oskar Czech Republic
23101 Orange GSM Slovak Republic
23102 EuroTel GSM Slovak Republic
23201 MobilKom Austria A1 Austria
23203 T-Mobile Austria
23205 Connect Austria One Austria
23207 Tele.ring Austria
23210 3AT Austria
23400001 Virgin United Kingdom
23410 02 United Kingdom
23415 Vodafone United Kingdom
23420 3 United Kingdom
23430 Virgin United Kigndom (others)
23430 T-Mobile United Kingdom
23433 Orange United Kingdom
23450 Jersey Telecom GSM United Kingdom
23455 Guernsey Telecoms GSM UK
23458 Manx Telecom Pronto GSM UK
23800001 Debitel Denmark
23801 Tele-Danmark Mobil Denmark
23802 Sonofon Denmark
23820 Telia Denmark Denmark
23830 Orange Denmark
24001 Telia Mobitel Sweden
24002 3 Sweden
24003 Orange Sweden
24007 Comviq GSM Sweden
24008 Vodafone Sweden
24201 Telenor Mobil Norway
24202 NetCom GSM Norway
24403 Telia Finland Finland
24405 Radiolinja Finland
24407 AT&T U.S.A.
24409 Finnet Group Finland
24412 2G Finland
24414 AMT Finland
24491 Sonera Corporation Finland
24601 Omnitel Lithuania
24602 UAB Bite GSM Lithuania
24603 Tele 2 Lithuania
24701 Latvian Mobile Tel. Latvia
24702 Tele 2 Latvia
24801 Estonian Mobile Telephone Estonia
24802 RadioLinja Eesti Estonia
24803 Tele 2 Estonia
25001 MTS Moscow Russia
25002 Megafon Russia
25005 Siberian Cellular Russia
25007 Zao Smarts Russia
25010 Don Telecom Russia
25012 New Telephone Company Russia
25013 Kuban GSM Russia
25039 Uratel Russia
25044 North Caucasian GSM Russia
25099 BeeLine Russia
25501 Ukrainian Mobile Comms Ukraine
25502 Ukrainian Radio Systems Ukraine
25503 Kyivstar GSM Ukraine
25505 Golden Telecom Ukraine
25701 Velcom
25702 MTS
25901 Voxtel Moldova
25902 Moldcell Moldova
26001 Polkomtel PLUS GSM Poland
26002 ERA GSM Poland
26003 IDEA Centertel Poland
26201 T-Mobile Germany
26202 Vodafone Germany
26203 E-Plus Mobilfunk Germany
26207 O2 Germany
26213 MobilCom Germany
26214 Quam Germany
26601 Gibraltar Telecoms Gibtel Gibraltar
26801 Vodafone Portugal
26803 Optimus Telecom. Portugal
26806 Telecom Moveis Nac. TMN Portugal
27001 P+T LUXGSM Luxembourg
27077 Millicom Tango GSM Luxembourg
27201 Vodafone Ireland
27202 O2 Ireland
27203 Meteor Ireland
27401 Iceland Telecom Siminn Iceland
27402 TAL hf Iceland
27403 Islandss Iceland
27404 Viking Iceland
27601 Albanian Mobile Comms Albania
27602 Vodafone Albania
27801 Vodafone Malta
27821 Go Mobile Malta
28001 Cyprus Telecoms Authority Cyprus
28201 Geocell Limited Georgia
28202 Magti GSM Georgia
28203 Geo 03 Georgia
28301 ArmenTel Armenia
28401 MobilTel AD Bulgaria
28405 Globul Bulgaria
28601 Turkcell Turkey
28602 TELSIM Turkey
28603 Aria Turkey
28604 Aycell Turkey
28801 FT-GSM
28802 KALL
29001 Tele Greenland Greenland
29340 Si.mobil Slovenia
29341 Si-GSM Slovenia
29370 Si VEGA 070 Slovenia
29401 MobiMak Macedonia
29402 MTS AD Macedonia
29501 Telecom
29502 Montel
29505 FL1
29577 Tango
30200001 Fido Canada
30237 Microcell Connexions Inc Canada
30272 Rogers AT&T Canada
31001 Pacific Mobile Comms Pap New Guinea
31002 APC Sprint Spectrum U.S.A.
31011 Wireless 2000 Telephone U.S.A.
31015 BellSouth Mobility DCS U.S.A.
31017 Cingular (Pacific Bell Wireless) U.S.A.
31020 T-Mobile U.S.A.
31026 Western Wireless Voicestream U.S.A.
31027 Powertel U.S.A.
31031 Aerial Communications U.S.A.
31038 AT&T U.S.A.
31077 Iowa Wireless Services U.S.A.
33805 Digicel JM
34001 Orange French West Indies
34020 BouygTel French West Indies
36801 C-Com CU
37412 TSTT
40001 Acell Telekom B.M. Azerbaijan
40002 BKcell GSM 2000 Azerbaijan
40101 K-Mobile Kazaksthan
40102 KCELL Kazaksthan
40217 B-Mobile BT
40401 Aircel Digilink Essar Cellph. India
40402 Bharti Cellular Telecom Airtel India
40403 Bharti Cellular Telecom Airtel India
40405 Hutch India
40407 TATA Cellular India
40408 Ushafon India
40410 Bharti Cellular Telecom Airtel India
40411 Hutch India
40412 Escotel Mobile Comms India
40413 Hutch India
40414 Ina Spice India
40415 Aircel Digilink Essar Cellph. India
40419 Escotel India
40420 Orange India
40421 BPL USWest Cellular India
40422 Idea India
40423 Usha Martin Tel. Command India
40424 Idea India
40426 Usha Martin Tel. Command India
40427 BPL USWest Cellular India
40430 Usha Martin Tel. Command India
40431 Bharti Cellular Telecom Airtel India
40432 Ushafone India
40434 BPL USWest Cellular India
40438 BPL USWest Cellular India
40440 INA AIRTel India
40441 RPG MAA India
40442 Srinivas Cellcom India
40443 BPL USWest Cellular India
40444 Spice India
40445 Bharti Cellular Telecom Airtel India
40446 BPL USWest Cellular India
40449 Bharti Cellular Telecom Airtel India
40451,53,54,55 BSNL Mobile India
40456 Escotel India
40457,58,59 BSNL Mobile India
40460 Aircel Digilink Essar Cellph. India
40462,64,66 BSNL Mobile India
40468 Dolphin India
40469 Dolphin India
40470 Oasis India
40471,72,73,74,75,76,77 BSNL Mobile India
40478 IDEA India
40479,80,81 BSNL Mobile India
40486 Hutch India
40490,92,93,94,95,96,97,98 Bharti Cellular
Telecom Airtel India
41001 Ufone Pakistan
41201 AWCC AF
41302 MTN Networks Dialog GSM Sri Lanka
41303 CellTel Sri Lanka
41401 MPTGSM
41501 FTML Cellis Lebanon
41503 LibanCell Lebanon
41601 J.M.T.S Fastlink Jordan
41677 MobCom Jordan
41701 SyriaTel Syria
41702 94 Syria
41709 MOBILE Syrian Telecom Est. Syria
41793 SyriaTel Syria
41801 Iraq Telecom Iraq
41902 Mobile Telecoms MTCNet Kuwait
41903 Wataniya Kuwait
42001 Ministry of PTT Al Jawal Saudi Arabia
42007 Electronics App' Est. EAE Saudi Arabia
42202 General Telecoms Oman
42401 UAE ETISALAT-G1 United Arab Emirates
42402 UAE ETISALAT-G2 United Arab Emirates
42501 Orange Israel
42502 Cellcom Israel
42505 JAWWAL Israel
42601 Batelco Bahrain
42701 QATARNET Qatar
42899 MobiCom MN
43211 TCI Iran
43214 Kish Iran
43400 Uzmacom Uzbekistan
43401 Buztel Uzbekistan
43402 Uzmacom Uzbekistan
43404 Daewoo Unitel Uzbekistan
43405 Coscom Uzbekistan
43407 UZD Uzbekistan
43603 MLT TJK
43605 TajikTel
43701 Bitel Kyrgyz Republic
44010 DoCoMo Japan
45201 Mobifone Vietnam
45202 Vinaphone Vietnam
45400 Hong Kong Telecom CSL Hong Kong
45404 Hutchison Telecom Hong Kong
45406 SmarTone Mobile Comms Hong Kong
45410 New World PCS Hong Kong
45412 Peoples Telephone Hong Kong
45416 Mandarin Com. Sunday Hong Kong
45418 Pacific Link Hong Kong
45422 P Plus Comm Hong Kong
45501 C.T.M. TELEMOVEL+ Macau
45601 Mobitel Cambodia
45602 SM Cambodia
45618 Camshin Cambodia
45701 Lao Shinawatra Telecom Lao
45702 ETLMNW Lao
45703 LatMil Lao
45708 Tango Lao
46000 China Telecom GSM China
46001 China Unicom GSM China
46002 Liaoning PPTA China
46601 Far EasTone Telecoms Taiwan
46606 TUNTEX Telecom Taiwan
46688 KG Telecom Taiwan
46692 Chunghwa Telecom Taiwan
46693 Mobitai Communications Taiwan
46697 Pacific Cellular TWNGSM Taiwan
46699 TransAsia Telecoms Taiwan
46701 Sun KP PRK
47001 Grameen Phone Bangladesh
47002 Aktel Bangladesh
47003 Sheba Telecom Bangladesh
47201 DHI Mobile MV
50202 Binariang Malaysia
50212 Maxis Malaysia
50213 Telekom Cellular TM Touch Malaysia
50216 DiGi Telecommunications Malaysia
50217 TimeCel Wireless Adam Malaysia
50219 Celcom Malaysia
50501 Telstra Mobile Comms Australia
50502 Optus Australia
50503 Vodafone Australia
50503 3 Australia
50508 OneTel Australia
51001 PT. SATelindo C Indonesia
51008 Lippo Telkomsel Indonesia
51010 TelKomSel Indonesia
51011 Pro XL Indonesia
51021 IM3 Indonesia
51501 Isla Comms Philippines
51502 Globe Telecom Philippines
51503 Smart Communications Philippines
51505 DigiTel Philippines
52001 Advanced Info Service AIS Thailand
52010 Orange Thailand
52018 DTotal Access Worldphone Thailand
52023 GSM 1800 Thailand
52099 Orange Thailand
52501 Sing. Tel. GSM 900 Singapore
52502 Sing. Tel. GSM 1800 Singapore
52503 MobileOne Asia Singapore
52504 M1-3GSM Singapore
52505 StarHub Singapore
52811 DST Communications Brunei Darussalam
53001 Vodafone New Zealand
53901 O-Call ton
54101 Smile VUT
54201 Vodafone Fiji Fiji
54601 Mobilis New Caledonia
54720 Vini French Polynesia
55001 FSM Telecom FSM
60201 MobiNil Egypt
60202 Vodafone Egypt
60301 Algerian Mobile Network Algeria
60302 Djezzy Algeria
60400 Meditel Marocco
60401 Itissalat Al-Maghrib IAM Marocco
60502 Tunisie Telecom Tunicell Tunisia
60503 Tunisiana Tunisia
60701 GamCel GMB
60702 AfriCELL GMB
60801 Sonatel ALIZE Senegal
60802 Sentel Senegal
60901 Mattel MR
61001 Matitel ML
61002 Ikatel ML
61201 Comstar Cellular Network Cote d'Ivoire
61203 Orange Cote d'Ivoire
61205 Telecel Cote d'Ivoire
61302 CelTel BF
61402 CelTel NE
61501 Togo Telecom TOGO CELL Togo
61602 TLCL-Ben BJ
61603 Benincell BJ
61604 BBcom BJ
61701 Cellplus Mobile Comms Mauritius
61710 Emtel Mauritius
61801 Lonestar Liberia
62001 ScanCom Ghana
62002 OneToch Ghana
62003 Mobitel Ghana
62120 Econet NG
62130 MTN NG
62140 Nitel NG
62201 CelTel TC
62202 Libertis TD
62401 MTN Cameroon
62402 Orange Cameroon
62501 Cabo Verde Movel Cape Verde
62601 CSTMovel STP
62701 GNQ01 GNQ
62801 Libertis GA
62802 GAB TeleCel
62803 CelTel GA
62901 CelTel CD
62910 Libertis CD
63002 CelTel RC
63004 CellCo GSM RC
63089 OASIS
63102 Unitel AGO
63301 Seychelles Cellular Services Seychelles
63310 AIRTEL Seychelles
63401 Mobile Telephone Company Sudan
63510 Rwandacell Rwanda
63601 Ethiopian Telecoms Auth. Ethiopia
63701 Barakaat SOM
63782 Telsom SOM
63902 Safaricom KE
63903 KenCell KE
64001 Tritel Tanzania
64002 Mobitel Tanzania
64003 Zantel Tanzania
64005 CelTel Tanzania
64101 Celtel Cellular Uganda
64110 MTN Uganda Uganda
64111 UTL Telecel Uganda
64201 Spacetel BI
64202 Busafa BI
64301 mCel MOZ
64501 Celtel Zambia
64601 Madacom Madagascar
64602 SMM Antaris Madagascar
64603 Sacel Madagascar
64700 Orange
64702 OMT
64710 Societe Reunionnaise SRR Reunion
64801 NET*ONE Zimbabwe
64803 Telecel Zimbabwe
64804 Econet Zimbabwe
64901 MTC Namibia
65001 Telekom Network Callpoint Malawi
65010 CelTel Malawi
65101 VCL Comms Lesotho
65102 Ezi Cel Lesothp
65201 Mascom Wireless Botswana
65202 Vista Botswana
65310 Swazi MTN SZ
65501 Vodacom South Africa
65507 Cell C South Africa
65510 MTN South Africa
71201 ICE CRI
72235 Port Hable ARG
72402,03,04 TIM Brazil
72431 Oi Brazil
732101 Comcel Columbia
73401 Infonet Venezuela
73402 Digitel Venezuela
74601 ICMS SR
74602 TeleG SR
As examination of SIM Cards and Handsets is on the increase internationally, thus roaming is relevant, the list below identifies Mobile Country Codes (e.g. 234) and Mobile Network Codes (e.g. 44) for global Mobile Operators. Please note the data are subject to change.
20201 Cosmote Greece
20205 Vodafone Greece
20209 Q-Telecom Greece
20210 Telestet Greece
20404 Vodafone Netherlands
20408 KPN Netherlands
20412 O2 Netherlands
20416 T-Mobile Netherlands
20420 Orange Netherlands
20601 Proximus Belgium
20610 Mobistar Belgium
20620 Base Belgium
20801 Orange France
20810 SFR France
20820 Bouygtel Telecom France
21303 S.T.A. MobilAnd Andorra
21401 Vodafone Spain
21402 Movistar Spain
21403 Amena Spain
21404 Xfera Spain
21407 Telefonica Movistar Spain
21601 Pannon GSM Hungary
21630 Westel 900 GSM Mobile Hungary
21670 Vodafone Hungary
21803 Eronet Bosnia Herzegovina
21805 Mobi's Bosnia Herzegovina
21890 GSM BIH Bosnia Herzegovina
21901 Croatian Telecoms Cronet Croatia
21910 VIP Croatia
22001 MOBTEL Yugoslavia
22002 ProMonte GSM Yugoslavia
22003 03 Yugoslavia
22004 Monet Yugoslavia
22201 Telecom Italia Mobile TIM Italy
22210 Vodafone Italy
22288 Wind Telecomunicazioni Italy
22298 BLU Italy
22299 3 Italy
22601 MobiFon CONNEX GSM Romania
22603 Cosmorom Romania
22610 Mobil Rom DIALOG Romania
22801 Swisscom NATEL Switzerland
22802 Sunrise Switzerland
22803 Orange Switzerland
23001 T-mobile Czech Republic
23002 EuroTel Praha Czech Republic
23003 Oskar Czech Republic
23101 Orange GSM Slovak Republic
23102 EuroTel GSM Slovak Republic
23201 MobilKom Austria A1 Austria
23203 T-Mobile Austria
23205 Connect Austria One Austria
23207 Tele.ring Austria
23210 3AT Austria
23400001 Virgin United Kingdom
23410 02 United Kingdom
23415 Vodafone United Kingdom
23420 3 United Kingdom
23430 Virgin United Kigndom (others)
23430 T-Mobile United Kingdom
23433 Orange United Kingdom
23450 Jersey Telecom GSM United Kingdom
23455 Guernsey Telecoms GSM UK
23458 Manx Telecom Pronto GSM UK
23800001 Debitel Denmark
23801 Tele-Danmark Mobil Denmark
23802 Sonofon Denmark
23820 Telia Denmark Denmark
23830 Orange Denmark
24001 Telia Mobitel Sweden
24002 3 Sweden
24003 Orange Sweden
24007 Comviq GSM Sweden
24008 Vodafone Sweden
24201 Telenor Mobil Norway
24202 NetCom GSM Norway
24403 Telia Finland Finland
24405 Radiolinja Finland
24407 AT&T U.S.A.
24409 Finnet Group Finland
24412 2G Finland
24414 AMT Finland
24491 Sonera Corporation Finland
24601 Omnitel Lithuania
24602 UAB Bite GSM Lithuania
24603 Tele 2 Lithuania
24701 Latvian Mobile Tel. Latvia
24702 Tele 2 Latvia
24801 Estonian Mobile Telephone Estonia
24802 RadioLinja Eesti Estonia
24803 Tele 2 Estonia
25001 MTS Moscow Russia
25002 Megafon Russia
25005 Siberian Cellular Russia
25007 Zao Smarts Russia
25010 Don Telecom Russia
25012 New Telephone Company Russia
25013 Kuban GSM Russia
25039 Uratel Russia
25044 North Caucasian GSM Russia
25099 BeeLine Russia
25501 Ukrainian Mobile Comms Ukraine
25502 Ukrainian Radio Systems Ukraine
25503 Kyivstar GSM Ukraine
25505 Golden Telecom Ukraine
25701 Velcom
25702 MTS
25901 Voxtel Moldova
25902 Moldcell Moldova
26001 Polkomtel PLUS GSM Poland
26002 ERA GSM Poland
26003 IDEA Centertel Poland
26201 T-Mobile Germany
26202 Vodafone Germany
26203 E-Plus Mobilfunk Germany
26207 O2 Germany
26213 MobilCom Germany
26214 Quam Germany
26601 Gibraltar Telecoms Gibtel Gibraltar
26801 Vodafone Portugal
26803 Optimus Telecom. Portugal
26806 Telecom Moveis Nac. TMN Portugal
27001 P+T LUXGSM Luxembourg
27077 Millicom Tango GSM Luxembourg
27201 Vodafone Ireland
27202 O2 Ireland
27203 Meteor Ireland
27401 Iceland Telecom Siminn Iceland
27402 TAL hf Iceland
27403 Islandss Iceland
27404 Viking Iceland
27601 Albanian Mobile Comms Albania
27602 Vodafone Albania
27801 Vodafone Malta
27821 Go Mobile Malta
28001 Cyprus Telecoms Authority Cyprus
28201 Geocell Limited Georgia
28202 Magti GSM Georgia
28203 Geo 03 Georgia
28301 ArmenTel Armenia
28401 MobilTel AD Bulgaria
28405 Globul Bulgaria
28601 Turkcell Turkey
28602 TELSIM Turkey
28603 Aria Turkey
28604 Aycell Turkey
28801 FT-GSM
28802 KALL
29001 Tele Greenland Greenland
29340 Si.mobil Slovenia
29341 Si-GSM Slovenia
29370 Si VEGA 070 Slovenia
29401 MobiMak Macedonia
29402 MTS AD Macedonia
29501 Telecom
29502 Montel
29505 FL1
29577 Tango
30200001 Fido Canada
30237 Microcell Connexions Inc Canada
30272 Rogers AT&T Canada
31001 Pacific Mobile Comms Pap New Guinea
31002 APC Sprint Spectrum U.S.A.
31011 Wireless 2000 Telephone U.S.A.
31015 BellSouth Mobility DCS U.S.A.
31017 Cingular (Pacific Bell Wireless) U.S.A.
31020 T-Mobile U.S.A.
31026 Western Wireless Voicestream U.S.A.
31027 Powertel U.S.A.
31031 Aerial Communications U.S.A.
31038 AT&T U.S.A.
31077 Iowa Wireless Services U.S.A.
33805 Digicel JM
34001 Orange French West Indies
34020 BouygTel French West Indies
36801 C-Com CU
37412 TSTT
40001 Acell Telekom B.M. Azerbaijan
40002 BKcell GSM 2000 Azerbaijan
40101 K-Mobile Kazaksthan
40102 KCELL Kazaksthan
40217 B-Mobile BT
40401 Aircel Digilink Essar Cellph. India
40402 Bharti Cellular Telecom Airtel India
40403 Bharti Cellular Telecom Airtel India
40405 Hutch India
40407 TATA Cellular India
40408 Ushafon India
40410 Bharti Cellular Telecom Airtel India
40411 Hutch India
40412 Escotel Mobile Comms India
40413 Hutch India
40414 Ina Spice India
40415 Aircel Digilink Essar Cellph. India
40419 Escotel India
40420 Orange India
40421 BPL USWest Cellular India
40422 Idea India
40423 Usha Martin Tel. Command India
40424 Idea India
40426 Usha Martin Tel. Command India
40427 BPL USWest Cellular India
40430 Usha Martin Tel. Command India
40431 Bharti Cellular Telecom Airtel India
40432 Ushafone India
40434 BPL USWest Cellular India
40438 BPL USWest Cellular India
40440 INA AIRTel India
40441 RPG MAA India
40442 Srinivas Cellcom India
40443 BPL USWest Cellular India
40444 Spice India
40445 Bharti Cellular Telecom Airtel India
40446 BPL USWest Cellular India
40449 Bharti Cellular Telecom Airtel India
40451,53,54,55 BSNL Mobile India
40456 Escotel India
40457,58,59 BSNL Mobile India
40460 Aircel Digilink Essar Cellph. India
40462,64,66 BSNL Mobile India
40468 Dolphin India
40469 Dolphin India
40470 Oasis India
40471,72,73,74,75,76,77 BSNL Mobile India
40478 IDEA India
40479,80,81 BSNL Mobile India
40486 Hutch India
40490,92,93,94,95,96,97,98 Bharti Cellular
Telecom Airtel India
41001 Ufone Pakistan
41201 AWCC AF
41302 MTN Networks Dialog GSM Sri Lanka
41303 CellTel Sri Lanka
41401 MPTGSM
41501 FTML Cellis Lebanon
41503 LibanCell Lebanon
41601 J.M.T.S Fastlink Jordan
41677 MobCom Jordan
41701 SyriaTel Syria
41702 94 Syria
41709 MOBILE Syrian Telecom Est. Syria
41793 SyriaTel Syria
41801 Iraq Telecom Iraq
41902 Mobile Telecoms MTCNet Kuwait
41903 Wataniya Kuwait
42001 Ministry of PTT Al Jawal Saudi Arabia
42007 Electronics App' Est. EAE Saudi Arabia
42202 General Telecoms Oman
42401 UAE ETISALAT-G1 United Arab Emirates
42402 UAE ETISALAT-G2 United Arab Emirates
42501 Orange Israel
42502 Cellcom Israel
42505 JAWWAL Israel
42601 Batelco Bahrain
42701 QATARNET Qatar
42899 MobiCom MN
43211 TCI Iran
43214 Kish Iran
43400 Uzmacom Uzbekistan
43401 Buztel Uzbekistan
43402 Uzmacom Uzbekistan
43404 Daewoo Unitel Uzbekistan
43405 Coscom Uzbekistan
43407 UZD Uzbekistan
43603 MLT TJK
43605 TajikTel
43701 Bitel Kyrgyz Republic
44010 DoCoMo Japan
45201 Mobifone Vietnam
45202 Vinaphone Vietnam
45400 Hong Kong Telecom CSL Hong Kong
45404 Hutchison Telecom Hong Kong
45406 SmarTone Mobile Comms Hong Kong
45410 New World PCS Hong Kong
45412 Peoples Telephone Hong Kong
45416 Mandarin Com. Sunday Hong Kong
45418 Pacific Link Hong Kong
45422 P Plus Comm Hong Kong
45501 C.T.M. TELEMOVEL+ Macau
45601 Mobitel Cambodia
45602 SM Cambodia
45618 Camshin Cambodia
45701 Lao Shinawatra Telecom Lao
45702 ETLMNW Lao
45703 LatMil Lao
45708 Tango Lao
46000 China Telecom GSM China
46001 China Unicom GSM China
46002 Liaoning PPTA China
46601 Far EasTone Telecoms Taiwan
46606 TUNTEX Telecom Taiwan
46688 KG Telecom Taiwan
46692 Chunghwa Telecom Taiwan
46693 Mobitai Communications Taiwan
46697 Pacific Cellular TWNGSM Taiwan
46699 TransAsia Telecoms Taiwan
46701 Sun KP PRK
47001 Grameen Phone Bangladesh
47002 Aktel Bangladesh
47003 Sheba Telecom Bangladesh
47201 DHI Mobile MV
50202 Binariang Malaysia
50212 Maxis Malaysia
50213 Telekom Cellular TM Touch Malaysia
50216 DiGi Telecommunications Malaysia
50217 TimeCel Wireless Adam Malaysia
50219 Celcom Malaysia
50501 Telstra Mobile Comms Australia
50502 Optus Australia
50503 Vodafone Australia
50503 3 Australia
50508 OneTel Australia
51001 PT. SATelindo C Indonesia
51008 Lippo Telkomsel Indonesia
51010 TelKomSel Indonesia
51011 Pro XL Indonesia
51021 IM3 Indonesia
51501 Isla Comms Philippines
51502 Globe Telecom Philippines
51503 Smart Communications Philippines
51505 DigiTel Philippines
52001 Advanced Info Service AIS Thailand
52010 Orange Thailand
52018 DTotal Access Worldphone Thailand
52023 GSM 1800 Thailand
52099 Orange Thailand
52501 Sing. Tel. GSM 900 Singapore
52502 Sing. Tel. GSM 1800 Singapore
52503 MobileOne Asia Singapore
52504 M1-3GSM Singapore
52505 StarHub Singapore
52811 DST Communications Brunei Darussalam
53001 Vodafone New Zealand
53901 O-Call ton
54101 Smile VUT
54201 Vodafone Fiji Fiji
54601 Mobilis New Caledonia
54720 Vini French Polynesia
55001 FSM Telecom FSM
60201 MobiNil Egypt
60202 Vodafone Egypt
60301 Algerian Mobile Network Algeria
60302 Djezzy Algeria
60400 Meditel Marocco
60401 Itissalat Al-Maghrib IAM Marocco
60502 Tunisie Telecom Tunicell Tunisia
60503 Tunisiana Tunisia
60701 GamCel GMB
60702 AfriCELL GMB
60801 Sonatel ALIZE Senegal
60802 Sentel Senegal
60901 Mattel MR
61001 Matitel ML
61002 Ikatel ML
61201 Comstar Cellular Network Cote d'Ivoire
61203 Orange Cote d'Ivoire
61205 Telecel Cote d'Ivoire
61302 CelTel BF
61402 CelTel NE
61501 Togo Telecom TOGO CELL Togo
61602 TLCL-Ben BJ
61603 Benincell BJ
61604 BBcom BJ
61701 Cellplus Mobile Comms Mauritius
61710 Emtel Mauritius
61801 Lonestar Liberia
62001 ScanCom Ghana
62002 OneToch Ghana
62003 Mobitel Ghana
62120 Econet NG
62130 MTN NG
62140 Nitel NG
62201 CelTel TC
62202 Libertis TD
62401 MTN Cameroon
62402 Orange Cameroon
62501 Cabo Verde Movel Cape Verde
62601 CSTMovel STP
62701 GNQ01 GNQ
62801 Libertis GA
62802 GAB TeleCel
62803 CelTel GA
62901 CelTel CD
62910 Libertis CD
63002 CelTel RC
63004 CellCo GSM RC
63089 OASIS
63102 Unitel AGO
63301 Seychelles Cellular Services Seychelles
63310 AIRTEL Seychelles
63401 Mobile Telephone Company Sudan
63510 Rwandacell Rwanda
63601 Ethiopian Telecoms Auth. Ethiopia
63701 Barakaat SOM
63782 Telsom SOM
63902 Safaricom KE
63903 KenCell KE
64001 Tritel Tanzania
64002 Mobitel Tanzania
64003 Zantel Tanzania
64005 CelTel Tanzania
64101 Celtel Cellular Uganda
64110 MTN Uganda Uganda
64111 UTL Telecel Uganda
64201 Spacetel BI
64202 Busafa BI
64301 mCel MOZ
64501 Celtel Zambia
64601 Madacom Madagascar
64602 SMM Antaris Madagascar
64603 Sacel Madagascar
64700 Orange
64702 OMT
64710 Societe Reunionnaise SRR Reunion
64801 NET*ONE Zimbabwe
64803 Telecel Zimbabwe
64804 Econet Zimbabwe
64901 MTC Namibia
65001 Telekom Network Callpoint Malawi
65010 CelTel Malawi
65101 VCL Comms Lesotho
65102 Ezi Cel Lesothp
65201 Mascom Wireless Botswana
65202 Vista Botswana
65310 Swazi MTN SZ
65501 Vodacom South Africa
65507 Cell C South Africa
65510 MTN South Africa
71201 ICE CRI
72235 Port Hable ARG
72402,03,04 TIM Brazil
72431 Oi Brazil
732101 Comcel Columbia
73401 Infonet Venezuela
73402 Digitel Venezuela
74601 ICMS SR
74602 TeleG SR
Subscribe to:
Posts (Atom)