GSM Radio Test Measurements
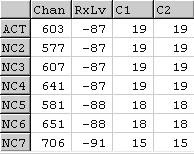
Radio Test Measurements 1

The screen image (Radio Test Measurements 1) represents the output results of radio coverage detected at the receiver (mobile telephone) and represent a single static view of that coverage at one instance. During cell site analysis there will be many screens obtained but for the purposes of this discussion this single screen image will do the job. Firstly, the reader will need to comprehend, at least, an interpretation that can be given to the identifiers in the screen image above.
TOP ROW
1. Chan: this indicator refers to the Broadcast Control Channel number.
2. RxLv: this indicator refers to the received strength of signal at the test handset measured in deciBel milliwatts, (dBm), where dBm is the notion for the measurement of power of the received radio signal e.g -75dBm.
3. C1: this is a quality indicator (path loss criterion) and is used for cell selection and cell reselection. The parameters are determined from the signal strength, the minimum received power levels for initiation of signals between the mobile and network, the maximum transmit power for accessing the network and the power of the mobile phone itself.
4. C2: this is an indicator used only for cell reselection optimisation and identifies parameters to aid the mobile phone in its cell reselection process.
LEFT COLUMN
5. 'ACT' denotes the strongest, thus dominant, serving cell coverage at that location providing the best quality associated with the BCCH number (Chan). Meaning the mobile telephone has completed the cell selection/reselection processes for normal service and has chosen a cell from which it plans to receive all available services (known as "camping on a cell").
6. 'NC2-NC6' denotes other cells available in an area that may equally offer service, but that the mobile phone has not camped upon them. However, the mobile network is aware that the mobile phone has choices available to it. Displayed beside the NCs are the cells, identified by their respective Broadcast Control Channel (BCCH) numbers.
OBSERVATIONS
If it is accepted that Chan (Channel) identifies the BCCH frequencies of the radio coverage that the receiver (mobile telephone) has detected in the ether (or as Professor Clerk-Maxwell (1886) so put it "ethereal wind" when describing electro-magnetic energy in the air ) then the consideration of the RxLv (signal strength) and C1 and C2 can then be considered.
Signal Strength
The maximum received signal strength at the receiver is understood to be -40dBm for GSM (see e.g GSM 11.10 etc) and commonly -40dBm is said to be at or very close to the transmitter. However, when looking at Radio Test Measurement 1 for ACT and NC1 we see Chan 81 and 87 detected at the receiver with signal strength -27dBm and -37dBm respectively. This raises the suggestion of saturation by the transmitter's coverage determined at the receiver, where the receiver is located on the ground. So what could be the reason for this?
One suggestion might be the sensitivity at the receiver is out of spec. For this instance it would be wrong. When I conduct cell site analysis I have five (5) mobile telephones with me set in network engineering mode in order to account for a faulty handset and other anomolies and for the purposes to determine when several mobile telephones are switched ON and side by side whether they would detect and camp on the same cell (GSM terminology for radio coverage from a particular Mast) or other cells. For the radio test measurements in this case all five (5) were switched ON and all detected Chan 81 with signal strength ranging from -27dBm / -30dBm.
So if it is accepted that the mobile telephones collectively are not revealing false-positives, what other occurrence might cause this to occur. To determine this matter readers may wish to investigate by way of the GSM Standards to comprehend the standard for upper and lower limits of signal strength and review the requirements for BTS (Base Transceiver Station) transmission power etc.
It may equally be helpful to mention at this point that the signal strengths for NC2 (- 44dBm), NC3 (-67dBm), NC4 (-68dBm), NC5 (-69dBm) and NC6 (-70dBm) are very respectable levels of signal strength being that they are of high quality. When I refer to high quality I am of course referring to the term as used by the objective GSM Standard GSM03.22. It contains a useful reference when considering the quality of signal strength (RxLv) recorded in radio test measurements that a mobile network "shall be understood to be received with high quality signal if the signal level is above ‑85 dBm".
Moreover, GSM05.08 identfies the threshold RXLEV (same as RxLv) on the downlink for handover process to commence. Typical range -103 to -73 dBm. Thus NC2 to NC6 received signal strength at the receiver, being above -73dBm, could one conclude from that were the mobile telephone to have camped on either one of NC2 to NC6 the network is unlikely to handover the mobile to another cell in the list? My observation to any reader would be investigate the GSM Standards in order to consider all the elements in order to produce a more rounded opinion on this matter.
C1/C2
Cell selection and cell reselection are rather complex and convoluted matters to discuss in this short discussion thread. My observation to the reader would be to look at C1/C2 and see whether at first instance the threshold results are identical or different? What does it mean if they are not identical? Also look closely to see if cells are indicated as not available for selection or reselection - denoted in Radio Test Measurement 1 as -99. Why would a cell not be selected and/or reselected? Is it due to poor signal strength; the mobile telephone has calculated its own power capability as low; or is it detecting interference etc?
The above is just a fraction of the information that needs to be considered during and following cell site analysis and from the little I have extrapolated above means that a casual approach to radio test measurements and cell site analysis can result in erroneous conclusions being drawn.
[Update: For more on Cell Site Analysis, see: