US Handset Serial Number Databases
US operators maintain their own stolen and blacklisted cellphone
databases. As of the 31st October 2012 the GSM operators AT&T and
T-Mobile began sharing their databases. CDMA operators Verizon and
Sprint have taken the decision to merge their databases but that will
not be complete until November 2013, so we are told.
The said objective of these initiatives are to improve track and trace.
As an example, GSM uses a 56-bit decimal digit s/n, whereas CDMA uses a
56-bit hexadecimal digitals s/n. However, in the US there are variations
of s/ns to consider.
The engine for these changes is driven by the FCC initiative - http://www.fcc.gov/document/announcement-new-initiatives-combat-smartphone-and-data-theft
To accommodate this and other cellphone/cellular changes I have altered
my CDMA training material and GSM training material. As consequence
these changes will also have an impact on WCDMA and LTE, either on a
national level or international level. These training materials have also changed, too.
_________________
Institute for Digital Forensics (IDF) - LinkedIn
Mobile Telephone Examination Board (MTEB) - LinkedIn
Investigations, Practices and Procedures: Seizure-Forensic Examination-Evidence. Cellular and Satellite Telephones, Call Records-Billing Data, Cell Site Analysis. Telecomms. Computer and Network Analysis. GPS devices & Jammers, Cyber, IoT forensics.
Monday, November 26, 2012
US Handset Serial Number Databases
Labels:
56-bit,
AT and T,
CDMA,
decimal,
digits,
FCC,
GSM,
hexadecimal,
IMEI,
LTE,
MEID,
pESN,
sprint,
t-mobile,
theft of cellphones,
training courses,
United States,
verizon,
wcdma
Thursday, November 22, 2012
EU Cybercrime (aka real name ICT ecrime)
EU Cybercrime (aka real name ICT ecrime)
Setting up the the criminal legal framework:
Judicial cooperation in criminal matters: combating attacks against information systems
Subject
3.30.06 Information and communication technologies
3.30.25 International information networks and society, internet
7.40.04 Judicial cooperation in criminal matters
http://www.europarl.europa.eu/oeil/popups/ficheprocedure.do?id=587653
Having a common European ICT eCrime Judicial protocol must equally rely on a common European Prosecution able to deal with ICT eCrime to assets:
https://www.era.int/cgi-bin/cms?_SID=47326840bea04c616952d8eb19eaceb72b2cb9a400217108097437&_sprache=en&_persistant_variant=/Our%20programme/Browse%20all%20events&_bereich=artikel&_aktion=detail&idartikel=123340
The establishment of the European Public Prosecutor's Office (EPPO) is envisaged in Article 86 TFEU. The EPPO would be responsible for investigating, prosecuting and bringing to justice those who damage assets managed by or on behalf of the EU. The European Council may adopt a decision extending the powers of the EPPO to include serious crime having a cross-border dimension.
Setting up the the criminal legal framework:
Judicial cooperation in criminal matters: combating attacks against information systems
Subject
3.30.06 Information and communication technologies
3.30.25 International information networks and society, internet
7.40.04 Judicial cooperation in criminal matters
http://www.europarl.europa.eu/oeil/popups/ficheprocedure.do?id=587653
Having a common European ICT eCrime Judicial protocol must equally rely on a common European Prosecution able to deal with ICT eCrime to assets:
https://www.era.int/cgi-bin/cms?_SID=47326840bea04c616952d8eb19eaceb72b2cb9a400217108097437&_sprache=en&_persistant_variant=/Our%20programme/Browse%20all%20events&_bereich=artikel&_aktion=detail&idartikel=123340
The establishment of the European Public Prosecutor's Office (EPPO) is envisaged in Article 86 TFEU. The EPPO would be responsible for investigating, prosecuting and bringing to justice those who damage assets managed by or on behalf of the EU. The European Council may adopt a decision extending the powers of the EPPO to include serious crime having a cross-border dimension.
Tuesday, November 20, 2012
Mobile Flash Data Erasure
Mobile Flash Data Erasure

Photo courtesy of Blancco
The growth in smart phones naturally means consumers will see even more utilities and tools similiar to those found on PCs, laptops and notebooks etc. A trend that is growing in relation to cleansing of personal details and company information stored logically and physically is called mobile flash data erasure (MFDE).
Service erasure
A group called www.tabernus.com/ promote "Tabernus also provides erasure solutions for Mobile Phones, USB, SSD (solid state devices) & other types of Flash removable memory and may other data holding devices too!"
Software erasure
Of course, there is a comparison for mobile phone flash erasure available from http://www.blancco.com/us/erase-smartphones/
The above examples are in addition to hardware encryption:
Device specific denied data access
Hardware Encryption: The iPhone 3GS and later, and all iPads, support built-in hardware encryption. All user data can be automatically encrypted in hardware at all times. This is used primarily for wiping the device rather than to stop attacks. Erasing the entire flash storage would be slow, so instead wiping works by destroying the encryption key, which instantly makes all user data inaccessible (Securosis).
And flash memory management:
Flash Memory Management Systems
Wear leveling ( http://en.wikipedia.org/wiki/Wear_leveling ) as well routines used in garbage collection solutions ( http://en.wikipedia.org/wiki/Garbage_collection_%28SSD%29#Garbage_collection and http://en.wikipedia.org/wiki/Garbage_collection_%28computer_science%29 ) can lead to potential loss due to overwriting existing deleted data.
From an examiner's point of view, MFDE is most likely to have a huge impact on deleted data recovery (DDR) from flash chips. The methodology and science behind Chip Off and JTAG is currently used for recovery of deleted data from a range of mobile devices. Overwriting 0101010101 (zeros and ones) or null values over particular areas or the entire area of the flash memory may make Chip Off and JTAG redundant in certain types of investigations and cases in the future.
Sunday, November 11, 2012
iPhone Secret Folder
iPhone Secret Folder
Opening the taps on this one could prove useful:


https://itunes.apple.com/us/app/secrets-folder-pro-lock-your/id566516598?mt=8
Opening the taps on this one could prove useful:


https://itunes.apple.com/us/app/secrets-folder-pro-lock-your/id566516598?mt=8
Thursday, November 08, 2012
Mobile Weapons and Seizure Procedure
Mobile Weapons and Seizure Procedure
The MTEB (Mobile Telephone Examination Board) is preparing the Eighth Edition of Section 4 Mobile Telephone Seizure Procedure (Mobile Weapons) and will update on new items and handling procedures for them.
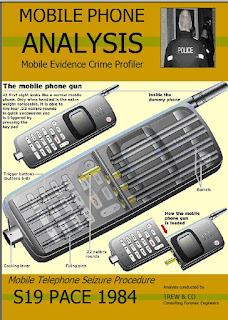
There has been a slow but persistent level in mobile/smart phones being adapted for use as some form of weapon.
Back in 2008 trewmte.blogspot reported about the mobile phone that fires bullets. The story of this wasn't new, by any means, but was highlighted to illustrate the variety and exposure of devcies that those involved in seizure procedure and mobile phone examiners can come into contact.
Report: http://trewmte.blogspot.co.uk/2008/11/mobile-phone-that-fires-bullets.html
Over time the trewmte.blogspot has highlighted other weapons, such as Stun Guns:

http://trewmte.blogspot.co.uk/2007/07/stun-gun-cellphone.html

http://trewmte.blogspot.co.uk/2007/10/another-mobile-telephone-stun-gun.html
But mobile/smart phones that propel objects or inflict severe shock are not the only adaptations out there. Take for instance the age old weapon of a knife adapted for use with a mobile phone ( seized 2005):
And now in 2012 we now have another weapon that uses an adapted iPhone case which the manufacturers purport can be used for personal protection to spray pepper in the eyes:
The above are by no means the end of mobile/smart phones adapted for some form of weapons. We only know too well how mobile phones have been rigged to set off incendiary devices etc, which the MTEB labels IMD (improvised mobile devices):


Yes the photos above all present disburbing images, but not for sensational purposes. Thankfully, it is not common for those involved with seizing items and examiners to come into contact with adapted and improvised devices like these on a regular basis. We still need to be aware and have a proposed handling procedure in place to deal with them though. That is on the basis that mobile/smart phone seizure and examination happens globally. The trewmte.blogspot is not simply local to the UK but deals with international matters and therefore articles like this are not only for UK consumption but for other countries that are involved in and employ seizure and examination procedures.
Lastly, and of specific relavance to seizure and examination procedure, it is priority to deal with mobile/smart phone weapon/s as opposed to figuring out what a person may have intended to do with it/them; figuring out is a thought process that can come later on. Why? One very good reason, the person who is seizing an adapted device (e.g. iPhone case above) and accidently sprays pepper into his/her face because s/he had no prior knowledge about the adapted device is clearly a priority. It is immaterial that the owner of such a device may have had genuine reasons (attacker pepper spray) for having such a device. Apart from mal-intention and recklessness of IMDs etc, for the majority of persons seizing or examining the device they wouldn't be the intended target and are nothing more than innocent bystanders.
The MTEB (Mobile Telephone Examination Board) is preparing the Eighth Edition of Section 4 Mobile Telephone Seizure Procedure (Mobile Weapons) and will update on new items and handling procedures for them.

There has been a slow but persistent level in mobile/smart phones being adapted for use as some form of weapon.
Back in 2008 trewmte.blogspot reported about the mobile phone that fires bullets. The story of this wasn't new, by any means, but was highlighted to illustrate the variety and exposure of devcies that those involved in seizure procedure and mobile phone examiners can come into contact.
Report: http://trewmte.blogspot.co.uk/2008/11/mobile-phone-that-fires-bullets.html
Over time the trewmte.blogspot has highlighted other weapons, such as Stun Guns:

http://trewmte.blogspot.co.uk/2007/07/stun-gun-cellphone.html

http://trewmte.blogspot.co.uk/2007/10/another-mobile-telephone-stun-gun.html
But mobile/smart phones that propel objects or inflict severe shock are not the only adaptations out there. Take for instance the age old weapon of a knife adapted for use with a mobile phone ( seized 2005):
And now in 2012 we now have another weapon that uses an adapted iPhone case which the manufacturers purport can be used for personal protection to spray pepper in the eyes:
The above are by no means the end of mobile/smart phones adapted for some form of weapons. We only know too well how mobile phones have been rigged to set off incendiary devices etc, which the MTEB labels IMD (improvised mobile devices):


Yes the photos above all present disburbing images, but not for sensational purposes. Thankfully, it is not common for those involved with seizing items and examiners to come into contact with adapted and improvised devices like these on a regular basis. We still need to be aware and have a proposed handling procedure in place to deal with them though. That is on the basis that mobile/smart phone seizure and examination happens globally. The trewmte.blogspot is not simply local to the UK but deals with international matters and therefore articles like this are not only for UK consumption but for other countries that are involved in and employ seizure and examination procedures.
Lastly, and of specific relavance to seizure and examination procedure, it is priority to deal with mobile/smart phone weapon/s as opposed to figuring out what a person may have intended to do with it/them; figuring out is a thought process that can come later on. Why? One very good reason, the person who is seizing an adapted device (e.g. iPhone case above) and accidently sprays pepper into his/her face because s/he had no prior knowledge about the adapted device is clearly a priority. It is immaterial that the owner of such a device may have had genuine reasons (attacker pepper spray) for having such a device. Apart from mal-intention and recklessness of IMDs etc, for the majority of persons seizing or examining the device they wouldn't be the intended target and are nothing more than innocent bystanders.
Tuesday, November 06, 2012
Age UK introduces mobile for elderly
Age UK introduces mobile for elderly
Evidential examiners may not expect to find our elderly senior citizens getting into bother and doing things they really ought not. If one or two do decide to go off the rails and grow old disgracefully they might decide they want to use simplified smartphone technology to contact their posse. Age UK and CyCell have got together to produce Age UK My Phone. Reviewed by phonesreview.co.uk the website says it is "a very easy to use mobile phone that is lightweight and credit-card sized weighing only 40 grams, and sports only 8 buttons that can be customised to contact the users loved ones with one press, whilst answering the handset is as simple as pressing a single answer button."
So if you want to see one of these new mobiles then get along to one of the 200 Age UK shops located throughout England. Apparently, the smartphone cost £55, has a range of flexible 30-day rolling price plans, and comes in eleven colours. No need to hunt for the phonebook as all the contact names can be found on the main screen. I could see other uses for this new smartphone, too. Perhaps parents may get one for their child, giving the child limited mobile access to contact home or friends and raise money for Age UK at the same time. A bonus could also be for the younger generation to be introduced to the excellent work of charities for the elderly, such as Age UK, by visiting their shops.
Update:
The Age UK My phone appears to be part of a growing market manufacturing trend internationally creating smartphone user-friendly interfaces for senior citizens, which is highlihted in this later CNET article Design of the times the secret to creating cell phones for seniors
Evidential examiners may not expect to find our elderly senior citizens getting into bother and doing things they really ought not. If one or two do decide to go off the rails and grow old disgracefully they might decide they want to use simplified smartphone technology to contact their posse. Age UK and CyCell have got together to produce Age UK My Phone. Reviewed by phonesreview.co.uk the website says it is "a very easy to use mobile phone that is lightweight and credit-card sized weighing only 40 grams, and sports only 8 buttons that can be customised to contact the users loved ones with one press, whilst answering the handset is as simple as pressing a single answer button."
So if you want to see one of these new mobiles then get along to one of the 200 Age UK shops located throughout England. Apparently, the smartphone cost £55, has a range of flexible 30-day rolling price plans, and comes in eleven colours. No need to hunt for the phonebook as all the contact names can be found on the main screen. I could see other uses for this new smartphone, too. Perhaps parents may get one for their child, giving the child limited mobile access to contact home or friends and raise money for Age UK at the same time. A bonus could also be for the younger generation to be introduced to the excellent work of charities for the elderly, such as Age UK, by visiting their shops.
Update:
The Age UK My phone appears to be part of a growing market manufacturing trend internationally creating smartphone user-friendly interfaces for senior citizens, which is highlihted in this later CNET article Design of the times the secret to creating cell phones for seniors
Subscribe to:
Posts (Atom)



