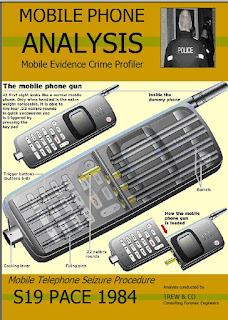
Originals and Copies. Britain and Smartphone Manufacturing
A recent post at
Global Sources discussed the Chinese smartphone manufacturing competition and the design, technical and feature competitiveness of home-grown brands in comparison to Apple's iPhone and Samsung.
Chart image courtesy of Global Sources
It is possible to read the data in chart as signalling a dynamic chinese marketplace presenting its wares to the World that can compete not only locally but at the international level. It is equally possible to read the data that Andoid has driven that evolution or that Western skillsets brought to China to exploit low costs has actually turned the 'student' into a 'master', such that the original 'master' is being forced to step aside and be replaced. To draw a different analogy, but with similar outcomes, was noted by Dr Carroll Quigley in his book Tradegy and Hope
a history of the world in our time (1965). Quigley identifies the Age of Expansion by defining four common expansion factors that re-occur throughout history: (i) of population, (ii) of geographic area, (iii) of production, and (iv) of knowledge.
Furthermore, Quigley equally notes that expansion ebbs and flows by noting that expansion occurs through trade-offs between centres (cores) of expansion and peripheries. The use of circles within circles provides the mental image the author wants the mind to imagine to understand where the core is located and where the periphery can be found. His use of analogy helps the reader to understand that development (production/knowledge) occuring at the core eventually reaches the periphery. At the periphery the incoming development is received and subjected to localised influences.
Fast fowarding from that 1965 commentary to today's manufacturing and placed in context with the above data in the chart, it can be seen that the Chinese have taken western developments and are enjoying expansion from the harvest (production/knowledge) brought to their door whilst the Western core is shrinking. Problematical with expansion ebbs and flows is the change that occurs and the ability to keep up with changes. Those changes have created problems regarding visual identity (mirroring), hardware functionality (imitation) and software (reproduction). Whilst Android OS may not have a problem with reproduction, given the widescale use of it in single country block manufacturing, eventually it would be cheaper for Chinese manufacturers to agree their own smartphone OS and use that to rival Apple, Google, Microsoft, Nokia, etc etc.
Subtle change can be seen by the shift towards differentiation between local manufactures product. As Global Sources comments "
Most large suppliers combine the Android OS with proprietary UI, widgets and mobile applications for differentiation." Eventually, and it is not far off, that differentiation will impact on Android. As Nokia and other European manufacturing was caught cat-napping when the Americas hit the stage with two big band anthem songs called the 'iPhone' and 'Android', which endeared them to the World, so Chinese manufacturing is heading, at a fast rate, for the pinnacle. Granted we don't know the OS name, but it really isn't about the name but what the OS will do that will create challenges Western manufacturing has not yet fully understood, even less are they ready for it.
However, in a quirk of fate just as China is starting to reach the peak, scientific technological breakthroughs that will impact on hardware means that there is no one dominant force in the World that has yet to or will control solely those breakthroughs. This is where Britiain should demonstrate it is leading with a/the British lionheart approach to industrialisation as opposed to '
I have a hug here with your name on it'. Britain must learn the lessons from throwing away (as it did in the 1970s - 2000s) the national treasure of quality manufacturing: - read up on the loss of British Steel, the confusion of the early Airbus project and the mistakes with British Chrysler.
PM Cameron and the British Government may be learning from these changes. The Government should have by now a blueprint for re-industrialisation for manufacturing in Britain. Rather than being dominated by people 'crying into their soup' about manufacturing pollution, perhaps set out the vision where a manufacturing industrial revolution in the UK can take place and explain where all these "green" policies are leading Britain? Answer the question is 'Britain is being artificially held back in manufacturing after billions of pounds of taxes have been spent on so-called non-pollutants to show our "green" credentials that have been and are paraded around the globe? Also, ask the British people to recall any significant programme for British industrialisation and manufacturing and then note the deafening silence? There is also curiousity why only a handful of entrepreneurs are working to get Britain out of the dulldrums.
Industrialisation, and to use that in context with smartphones as one example of a manufacturing stream that Britain can and should be capable of performing, could be adopted in manufacturing areas to see Britain mass produce smartphones and the components to go with them:
- new ultra fine silicon
- smartphone design and casing
- new electronic production technqiues
- a British labelled operating system (OS) -
- etc
In this day and age it does seem inconceivable as to why Britain is not noted for being a mobile phone manufacturing base to a level that is noted for other countries that come to mind when the spoken brand names are heard: Nokia, Ericsson, Alcatel, Apple and Samsung etc.