Android DOTS - Locking the Screen
I have received several emails following the earlier post iphones-common-password-usage-risks whether I had seen other studies or reports about security risks with the Locking the Screen (linking DOTS) feature in Android and similar featured mobile phones and what I thought.
It is impossible to read everything and many studies/report sometimes don't become available until some years after authors produce them.
My own analysis of the reports (at this stage) that I have seen thus far is that many of the comments about Locking the Screen privacy techniques generally identify that an author acknowledges the device has this privacy/security capability available and provides one method to reduce risk. Forensically speaking, authors also record the complications when the restricted access mode is activated when the device is presented for examination. These are useful comments, but are not fully supported by any indepth research to define common combination of DOTS used by users for their numerical choice of locking patterns. That is menat to be taken in context with the common choice of PINs as suggested by the post iphones-common-password-usage-risks.
The authors Aviv/Gibson/Mossop/Blaze/Smith in 2010 produced an informed and respected report on Screen Smudges that illustrated risks of pattern smudges on the mobile phone touch-screen being detected which refined earlier concerns in 2009 about smudging illustrated in posts on the Android - An Open Handset Alliance Project.
There are discussive science articles on the web about how secure are Android DOTS unlock_patterns regarding numerical choices for the locking code that, again, could provide useful material for more indepth forensic analysis and study. I could carrry on identifying material I have researched but that would merely produce, largely, similar and repetitous paragraphs of statements listing what I found available. However, risks to user touch-screen mobile phones may occur when considering entering unlock DOTS patterns, passwords and PINs and unauthorised access attacker or hackers gaze could potentially include the less troublesome methods to gain access using:
i) clandestine apps/progs (WORMs etc from download or P2P) that could record user entries on the touch-screens and storing the output [having fowarded to a memory cards etc] in a hidden file (so be aware of apps/progs on the handset - check eg file manager/root and change memory cards on a regular basis)
ii) using fingerprint tape on the touch-screen (so clean the screen regularly)
iii) shoulder-surfing the user's locking DOTS pattern (so the longer the pattern the harder it can be for the shoulder-surfer to memorise)
Investigations, Practices and Procedures: Seizure-Forensic Examination-Evidence. Cellular and Satellite Telephones, Call Records-Billing Data, Cell Site Analysis. Telecomms. Computer and Network Analysis. GPS devices & Jammers, Cyber, IoT forensics.
Thursday, August 18, 2011
Wednesday, August 17, 2011
The Emperor's New Clothes
The Emperor's New Clothes
I was reminded recently of this Hans Christian Andersen tale that brought back memories of hearing it as a child. The hero in the tale is the child for speaking out because those who could have said something found it difficult until it became impossible for them not to say something (but by then it was too late).
The tale could have application to forensics and expert evidence. The focus on distinguishing illusion from reality is an important one and tasks all of us in our field of endeavour to ensure amongst other things:
i) opinion given doesn't simply repeat what others have stated for fear of stepping out of line or the threat of the use psychological intimidation of belittle to one's character
ii) to stand up and challenge, even where an awful lot money has been spent on methods or systems that are systemtically flawed or producing inaccurate statements
iii) not to leave a problem to others to highlight the reality of it ('truth will out') because it feels safe to pretend ignorance or suggesting that it was someone else's problem so not bothering to test the veracity of the method/system in use
I was reminded recently of this Hans Christian Andersen tale that brought back memories of hearing it as a child. The hero in the tale is the child for speaking out because those who could have said something found it difficult until it became impossible for them not to say something (but by then it was too late).
The tale could have application to forensics and expert evidence. The focus on distinguishing illusion from reality is an important one and tasks all of us in our field of endeavour to ensure amongst other things:
i) opinion given doesn't simply repeat what others have stated for fear of stepping out of line or the threat of the use psychological intimidation of belittle to one's character
ii) to stand up and challenge, even where an awful lot money has been spent on methods or systems that are systemtically flawed or producing inaccurate statements
iii) not to leave a problem to others to highlight the reality of it ('truth will out') because it feels safe to pretend ignorance or suggesting that it was someone else's problem so not bothering to test the veracity of the method/system in use
Monday, August 15, 2011
Research: critiques of author recognition
Research: critiques of author recognition
With the high-profile Olympics less than 12-months away, the recent looting and rioting that involved the use of voicemail, instant messenging and web-based media and the approach to using "cybercrime" as the new-labelled tool to describe digital investigation and evidential seizure of alleged culpability, these research papers cover some useful ground that might be helpful in evaluating methodology previously unsuspected as fallible to error or mistake, and may have some useful application when applied in author recognition cases which might be relevant to evidence found on mobile phones and computers.
Authors vs. Speakers: A Tale of Two Subfields
The best part of Monday's post on the Facebook authorship-authentication controversy ("High-stakes forensic linguistics", 7/25/2011) was the contribution in the comments by Ron Butters, Larry Solan, and Carole Chaski. It's interesting to compare the situation they describe — and the frustration that they express about it — with the history of technologies for answering questions about the source of bits of speech rather than bits of text.
Practical Attacks Against Authorship Recognition Techniques
The use of statistical AI techniques in authorship recognition (or stylometry) has contributed to literary and historical breakthroughs. These successes have led to the use of these techniques in criminal investigations and prosecutions. However, few have studied adversarial attacks and their devastating effect on the robustness of existing classification methods. This paper presents a framework for adversarial attacks including obfuscation attacks, where a subject attempts to hide their identity imitation attacks, where a subject attempts to frame another subject by imitating their writing style. The major contribution of this research is that it demonstrates that both attacks work very well. The obfuscation attack reduces the effectiveness of the techniques to the level of random guessing and the imitation attack succeeds with 68-91% probability depending on the stylometric technique used. These results are made more significant by the fact that the experimental subjects were unfamiliar with stylometric techniques, without specialized knowledge in linguistics, and spent little time on the attacks. This paper also provides another significant contribution to the field in using human subjects to empirically validate the claim of high accuracy for current techniques (without attacks) by reproducing results for three representative stylometric methods.
With the high-profile Olympics less than 12-months away, the recent looting and rioting that involved the use of voicemail, instant messenging and web-based media and the approach to using "cybercrime" as the new-labelled tool to describe digital investigation and evidential seizure of alleged culpability, these research papers cover some useful ground that might be helpful in evaluating methodology previously unsuspected as fallible to error or mistake, and may have some useful application when applied in author recognition cases which might be relevant to evidence found on mobile phones and computers.
Authors vs. Speakers: A Tale of Two Subfields
The best part of Monday's post on the Facebook authorship-authentication controversy ("High-stakes forensic linguistics", 7/25/2011) was the contribution in the comments by Ron Butters, Larry Solan, and Carole Chaski. It's interesting to compare the situation they describe — and the frustration that they express about it — with the history of technologies for answering questions about the source of bits of speech rather than bits of text.
Practical Attacks Against Authorship Recognition Techniques
The use of statistical AI techniques in authorship recognition (or stylometry) has contributed to literary and historical breakthroughs. These successes have led to the use of these techniques in criminal investigations and prosecutions. However, few have studied adversarial attacks and their devastating effect on the robustness of existing classification methods. This paper presents a framework for adversarial attacks including obfuscation attacks, where a subject attempts to hide their identity imitation attacks, where a subject attempts to frame another subject by imitating their writing style. The major contribution of this research is that it demonstrates that both attacks work very well. The obfuscation attack reduces the effectiveness of the techniques to the level of random guessing and the imitation attack succeeds with 68-91% probability depending on the stylometric technique used. These results are made more significant by the fact that the experimental subjects were unfamiliar with stylometric techniques, without specialized knowledge in linguistics, and spent little time on the attacks. This paper also provides another significant contribution to the field in using human subjects to empirically validate the claim of high accuracy for current techniques (without attacks) by reproducing results for three representative stylometric methods.
Thursday, July 28, 2011
M2M Crime
M2M Crime
In the last discussion (mobile-markets) a reference was made to M2M (machine-to-machine) market stats. Yesterday's article from 'pcworld' about hackers using mobile communications for war texting to unlock car doors (war_texting) should provide useful material to study about M2M for MTEB Students to identify 'potential' crime activity and where evidence maybe generated. Send your finalised report (pdf), for marking, by email please.
In the last discussion (mobile-markets) a reference was made to M2M (machine-to-machine) market stats. Yesterday's article from 'pcworld' about hackers using mobile communications for war texting to unlock car doors (war_texting) should provide useful material to study about M2M for MTEB Students to identify 'potential' crime activity and where evidence maybe generated. Send your finalised report (pdf), for marking, by email please.
Saturday, July 23, 2011
Mobile Markets: Nokia 'Mobile Man'...it tells of a story
Mobile Markets: Nokia 'Mobile Man'...it tells of a story
This excellent construction, made up entirely of mobile phones, is Nokia's collaborative project with Beijing postal service to encourage recycling of mobile phones that can be handed in at post offices, according to the news article at news.cnet.com.
It's great to see projects like, which tend to draw promotions using creative and talented ideas demonstrating the evolving and transforming world of mobile phones and its market places. Back in 2007 I posted on another creative work cellphone-transformer, which, yet again, shows a design that captures the imagination displaying the versatile uses to which a mobile phone might be put.
The business and ecomonic philosophy that resides behind these creative images equally tells of a story of growth and success. If recycling is happening then, perhaps, that is as a likely consequence of mobile ubiquity taking hold. That is a nice statement, but can I back it up? I don't have my finger on every financial and market research pulse, but, apart from anecdotal references, there are various stats out there from the market research firms. Indeed, back in 2008 I blogged (staggering-figures-for-mobile-phone) on the state of the mobile data market when the economic downturn (which appears to have started in 2007 so we are led to believe) had got a firmer grip on global markets. In 2010 the stats still showed extraordinary figures (text.it), although the exact detail where all this activity occurs to generate such figures may not be obvious. It may be compelling to want to know how many consumers send text and mms messages (see OFCOM website for stats), but that is not the full picture. There are the other data markets in business to consider, such as the M2M market place (winwin) and comments by industry pundits on the mobile payments market (cellular-news).
It is useful to see how industry people collate information and bring amassed facts together in order to express their views and vision on what all the facts mean to them in aggregrate. An example of this can be seen in Tomi Ahonen's enthusiastic commentary found in Insiders Guide To Mobile (lulu) with references to trillion dollar market, over 4 billion users and the segmented factors when drawn together identified to him what is forecast for mobile. A view of one segment of the mobile phone market, apps, is simply a further illustration of information to be sourced to underpin market trends (windows-phone-apps-reach-new-market), another is sales and market penetration, such as Apple's iPhone outrageously outstanding sales growth.
If I removed from the context of the above commentary discussion about modern technology, and simply focussed on what an image might communicate, I could have been talking about social, cultural and economic life that might have been depicted by way of an 18th/19th century painting (irrespective of whether the painting is by an impressionist or not). Whilst the image above may not be an old master piece, the image still has a story to explicitly convey and that, in forensic terms, requires understanding all or part of any implicit subtext the image can also communicate.
My forensic skills, acquired over the years, meant that my reaction to seeing this image (even though photo/art imagery is not my subject), was to look at it as evidence and then set out to see what I could deduce from there. In reality we do this everyday in our work. We see a SIM card. We then want to know what it is and what is inside. In order to know what we are dealing with we need to know how it works and what can be held inside and whether all or part thereof can be revealed. Moreover, we need to know what amounts to 'conformance' and within that framework which conforming element is 'mandatory' and which is 'optional'. Once we have that background we can then begin to understand what is 'non-conforming' and/or 'unusual'. This path can equally be taken when dealing with mobile phones and RF investigations.
In conclusion, the subtext of this discussion can be revealed. However mobile phones maybe presented to the world, it is our job in forensics not to change that messsage, but to break down the presentation into its various building block elements in order that we know how each piece works and then how the pieces fit together and work and cooperate together. This is because a true forensic standard requires of the individual to obtain knowledge by way of commentary, appropriate training, standards, specs and investigation, that includes examination and testing (trial and error), which is one side of the coin. The other side of this coin is knowing what the 'thing' in its final state is intended to do, which requiries understanding of the market place it which the 'thing' is to be adopted. Using skills and techniques like these provide for a rich source of experience, too. Essentially, learning to bring all the pieces that are needed into play and being able to demonstrate that identifies the forensic examiner working with a well hone, self-principled approach of high standard.
For MTEB students, the summer recess is now here. Sure, have a great time and relax and enjoy the break, but don't waste valuable time. Great people strive in life because they want to go beyond what has already been achieved. Take time out from relaxing to bring together the exposure you have had to mobile knowledge and experience you have acquired, thus far. Select a particular line of investigative enquiry and see how far you get with it. I have identified some links above to illustrate a way forward or choose a different subject matter; remember to be able to demonstrate the primary basics of 'bush' methodology.
This excellent construction, made up entirely of mobile phones, is Nokia's collaborative project with Beijing postal service to encourage recycling of mobile phones that can be handed in at post offices, according to the news article at news.cnet.com.
It's great to see projects like, which tend to draw promotions using creative and talented ideas demonstrating the evolving and transforming world of mobile phones and its market places. Back in 2007 I posted on another creative work cellphone-transformer, which, yet again, shows a design that captures the imagination displaying the versatile uses to which a mobile phone might be put.
The business and ecomonic philosophy that resides behind these creative images equally tells of a story of growth and success. If recycling is happening then, perhaps, that is as a likely consequence of mobile ubiquity taking hold. That is a nice statement, but can I back it up? I don't have my finger on every financial and market research pulse, but, apart from anecdotal references, there are various stats out there from the market research firms. Indeed, back in 2008 I blogged (staggering-figures-for-mobile-phone) on the state of the mobile data market when the economic downturn (which appears to have started in 2007 so we are led to believe) had got a firmer grip on global markets. In 2010 the stats still showed extraordinary figures (text.it), although the exact detail where all this activity occurs to generate such figures may not be obvious. It may be compelling to want to know how many consumers send text and mms messages (see OFCOM website for stats), but that is not the full picture. There are the other data markets in business to consider, such as the M2M market place (winwin) and comments by industry pundits on the mobile payments market (cellular-news).
It is useful to see how industry people collate information and bring amassed facts together in order to express their views and vision on what all the facts mean to them in aggregrate. An example of this can be seen in Tomi Ahonen's enthusiastic commentary found in Insiders Guide To Mobile (lulu) with references to trillion dollar market, over 4 billion users and the segmented factors when drawn together identified to him what is forecast for mobile. A view of one segment of the mobile phone market, apps, is simply a further illustration of information to be sourced to underpin market trends (windows-phone-apps-reach-new-market), another is sales and market penetration, such as Apple's iPhone outrageously outstanding sales growth.
If I removed from the context of the above commentary discussion about modern technology, and simply focussed on what an image might communicate, I could have been talking about social, cultural and economic life that might have been depicted by way of an 18th/19th century painting (irrespective of whether the painting is by an impressionist or not). Whilst the image above may not be an old master piece, the image still has a story to explicitly convey and that, in forensic terms, requires understanding all or part of any implicit subtext the image can also communicate.
My forensic skills, acquired over the years, meant that my reaction to seeing this image (even though photo/art imagery is not my subject), was to look at it as evidence and then set out to see what I could deduce from there. In reality we do this everyday in our work. We see a SIM card. We then want to know what it is and what is inside. In order to know what we are dealing with we need to know how it works and what can be held inside and whether all or part thereof can be revealed. Moreover, we need to know what amounts to 'conformance' and within that framework which conforming element is 'mandatory' and which is 'optional'. Once we have that background we can then begin to understand what is 'non-conforming' and/or 'unusual'. This path can equally be taken when dealing with mobile phones and RF investigations.
In conclusion, the subtext of this discussion can be revealed. However mobile phones maybe presented to the world, it is our job in forensics not to change that messsage, but to break down the presentation into its various building block elements in order that we know how each piece works and then how the pieces fit together and work and cooperate together. This is because a true forensic standard requires of the individual to obtain knowledge by way of commentary, appropriate training, standards, specs and investigation, that includes examination and testing (trial and error), which is one side of the coin. The other side of this coin is knowing what the 'thing' in its final state is intended to do, which requiries understanding of the market place it which the 'thing' is to be adopted. Using skills and techniques like these provide for a rich source of experience, too. Essentially, learning to bring all the pieces that are needed into play and being able to demonstrate that identifies the forensic examiner working with a well hone, self-principled approach of high standard.
For MTEB students, the summer recess is now here. Sure, have a great time and relax and enjoy the break, but don't waste valuable time. Great people strive in life because they want to go beyond what has already been achieved. Take time out from relaxing to bring together the exposure you have had to mobile knowledge and experience you have acquired, thus far. Select a particular line of investigative enquiry and see how far you get with it. I have identified some links above to illustrate a way forward or choose a different subject matter; remember to be able to demonstrate the primary basics of 'bush' methodology.
Labels:
'bush' methodology,
18th 19th century,
Apple,
cell site analysis,
evidence,
forensic,
future market,
IPhone,
marketplace,
Mobile Evidence,
Mobile Forensics,
MTEB,
Nokia,
painting,
SIM,
USIM
Tuesday, July 19, 2011
iPhones: Common Password Usage Risks
iPhones: Common Password Usage Risks
In the current climate of news about the use of PINs/Passwords to gain unauthorised access to mobile content and voicemail accounts, an interesting study published by an app developer identifying common iPhone passwords. The article identifies the ten most common pin/passwords determined from the study:
"Formulaic passwords are never a good idea, yet 15% of all passcode sets were represented by only 10 different passcodes (out of a possible 10,000). The implication? A thief (or just a prankster) could safely try 10 different passcodes on your iPhone without initiating the data wipe. With a 15% success rate, about 1 in 7 iPhones would easily unlock--even more if the intruder knows the users’ years of birth, relationship status, etc." most common iphone passcodes
Whilst password predicability may not be ground breaking news, this study just might be a useful insight that highlights that iphone mobile phone users appear to make predictable choices when selecting a pin/password and may persuade users to look more carefully at their choice of handset pin/password in current use.
Sunday, July 03, 2011
HTML5: holds a future for and after other mobile apps
HTML5: holds a future for and after other mobile apps
I have just written about mobile apps and forensics (windows-phone-apps-reach-new-market) because it is here and now and requires attention. An aspect of Forensics though is equally not being blinked to future trends. The question of future trends was asked by the House of Commons Science and Technology Committee in their recent report cmselect 855. It is really worth the time and effort to download and read this report.
HTML5 is a future trend and one that has already started to take hold. As nebusiness's The Journal pointed out (http://www.nebusiness.co.utechnology-leap-set-to-make-apps-redundant) "HTML5 builds on the technology of the existing internet but, as every web user knows, if you lose your connection, you lose your work. With HTML5 you don’t – you can go from connected to disconnected and never notice: files can be saved locally and remotely when needed, just like normal apps. Quietly, we’re starting to see more HTML5 apps, like that of the FT, which work on all devices. The FT app is amazing. Try it out. It’s all in HTML5 and as good as, if not better, than a native iPhone app."
With HTML5 there is a sense that forensics might see improvement in interpreting data that could be properly rendered for viewing; currently this can require other apps to assist that process. Moreover, vast quantities of unintelligible random code and data which could not be rendered by handsets can be found during physical dumps that no one really makes sense to identify what it is. Were unravelling and decoding of random code/data to be explained in itself it still might not explicitly or implicity confirm whether the handset user could see/access rendered versions of that code and data on the handset screen or select content by using the handset UI. HTML5 may yet assist in solving some of these issues, so is it a future trend forensic practitioners should be aware?
Well, I think it is something that cannot be excluded largely due to the fact it is at present being used, mobile browsers are making use of it and widely used mobile handsets support or portions of it in e.g. Apple's iOS 4.2, Android, Samsung, Nokia and so on.
So what can HTML5 do for mobile web browsing?
Well, it helps standardise those issues which had previously been problematical to mobile web browsing and, for mobile web developers, to get testable, cross-platform and standards-based interface for developing content that, prior to HTML5, required _fit_the_need_of_the_technology_ methods or proprietory APIs to achieve the level of rendering needed for rich content and browsing.
HTML5 and Forensics
It opens up the door for new or improved evidence. Do remember, particularly for those readers not involved with forensics, evidence doesn't necessarily mean recovered data that is detrimental or that some massive spying operation is in progress. Mobile HTML5 could have benefits to assist retain data that could help resolve a dispute, track a missing person and so on. Location awareness, localised data caching when mobile connectivity is lost and a range of other features that I shall be discussing later on.
What is possible to say at this stage, omitted data previously breaking the chain of causation needed for forensic evaluation may well be greatly assisted by HMTL5 but without a forensic examiner having to put, metaphorically speaking, all his/her sought artefact-eggs into one evidential-methodology basket. Nice !
I have just written about mobile apps and forensics (windows-phone-apps-reach-new-market) because it is here and now and requires attention. An aspect of Forensics though is equally not being blinked to future trends. The question of future trends was asked by the House of Commons Science and Technology Committee in their recent report cmselect 855. It is really worth the time and effort to download and read this report.
HTML5 is a future trend and one that has already started to take hold. As nebusiness's The Journal pointed out (http://www.nebusiness.co.utechnology-leap-set-to-make-apps-redundant) "HTML5 builds on the technology of the existing internet but, as every web user knows, if you lose your connection, you lose your work. With HTML5 you don’t – you can go from connected to disconnected and never notice: files can be saved locally and remotely when needed, just like normal apps. Quietly, we’re starting to see more HTML5 apps, like that of the FT, which work on all devices. The FT app is amazing. Try it out. It’s all in HTML5 and as good as, if not better, than a native iPhone app."
With HTML5 there is a sense that forensics might see improvement in interpreting data that could be properly rendered for viewing; currently this can require other apps to assist that process. Moreover, vast quantities of unintelligible random code and data which could not be rendered by handsets can be found during physical dumps that no one really makes sense to identify what it is. Were unravelling and decoding of random code/data to be explained in itself it still might not explicitly or implicity confirm whether the handset user could see/access rendered versions of that code and data on the handset screen or select content by using the handset UI. HTML5 may yet assist in solving some of these issues, so is it a future trend forensic practitioners should be aware?
Well, I think it is something that cannot be excluded largely due to the fact it is at present being used, mobile browsers are making use of it and widely used mobile handsets support or portions of it in e.g. Apple's iOS 4.2, Android, Samsung, Nokia and so on.
So what can HTML5 do for mobile web browsing?
Well, it helps standardise those issues which had previously been problematical to mobile web browsing and, for mobile web developers, to get testable, cross-platform and standards-based interface for developing content that, prior to HTML5, required _fit_the_need_of_the_technology_ methods or proprietory APIs to achieve the level of rendering needed for rich content and browsing.
HTML5 and Forensics
It opens up the door for new or improved evidence. Do remember, particularly for those readers not involved with forensics, evidence doesn't necessarily mean recovered data that is detrimental or that some massive spying operation is in progress. Mobile HTML5 could have benefits to assist retain data that could help resolve a dispute, track a missing person and so on. Location awareness, localised data caching when mobile connectivity is lost and a range of other features that I shall be discussing later on.
What is possible to say at this stage, omitted data previously breaking the chain of causation needed for forensic evaluation may well be greatly assisted by HMTL5 but without a forensic examiner having to put, metaphorically speaking, all his/her sought artefact-eggs into one evidential-methodology basket. Nice !
Saturday, July 02, 2011
Windows Phone Apps reach new market levels
Windows Phone Apps reach new market levels
Back in 2006 Vodafone announced news to standardise handsets (here) and I commented then that it might be a good idea if users could profile their own handsets with the apps they actually use. There is much market evidence to suggest the evolving mobile is moving in that direction. Android, Apple, Blackberry, Java and Symbian apps stores are a good example of this. The growth in mobile apps has not been limited to the five previously mentioned, Window Phone apps, too, are storming ahead with over 25,235 apps available.
There is a brief synopsis of the Windows Phone apps growth at winrumors. The chart below is courtesy of windowsphoneapplist.
Knowing these stats can be helpful but unless there is some inter-related commentary about the technology (so to speak) that links those stats to forensics, it can all become pretty meaningless. My take on those stats is they do present challenges that the mobile forensic community will need to adapt, sooner rather than later. There is a wealth of information in apps that cannot be gleaned from using many of the evidence recovery automated handset readers. This has happened because evidence tools may not have been designed for that purpose; recovering app info and the content they store.
Firstly, it is important to understand the distinction between apps accessible through interface/emulator tools, designed for app builders and programmers (so to speak), and those tools said to be designed for collecting evidence.
Secondly, it doesn't automatically follow that just because an examiner obtains an evidential physical dump from flash memory ( a ) the examiner has dumped everything from the correct component ( b ) that the dump's content will be 'visible' and 'legible' (PACE 1984) and 'intelligible' (DPA1984).
Holding such a view doesn't mean, nor is it intented to suggest, that I think there is an impossibility here that cannot be overcome. Do I think the mobile forensic communty, working together, will find the solutions? Yes, absolutely, naturally.
Back in 2006 Vodafone announced news to standardise handsets (here) and I commented then that it might be a good idea if users could profile their own handsets with the apps they actually use. There is much market evidence to suggest the evolving mobile is moving in that direction. Android, Apple, Blackberry, Java and Symbian apps stores are a good example of this. The growth in mobile apps has not been limited to the five previously mentioned, Window Phone apps, too, are storming ahead with over 25,235 apps available.
There is a brief synopsis of the Windows Phone apps growth at winrumors. The chart below is courtesy of windowsphoneapplist.
Knowing these stats can be helpful but unless there is some inter-related commentary about the technology (so to speak) that links those stats to forensics, it can all become pretty meaningless. My take on those stats is they do present challenges that the mobile forensic community will need to adapt, sooner rather than later. There is a wealth of information in apps that cannot be gleaned from using many of the evidence recovery automated handset readers. This has happened because evidence tools may not have been designed for that purpose; recovering app info and the content they store.
Firstly, it is important to understand the distinction between apps accessible through interface/emulator tools, designed for app builders and programmers (so to speak), and those tools said to be designed for collecting evidence.
Secondly, it doesn't automatically follow that just because an examiner obtains an evidential physical dump from flash memory ( a ) the examiner has dumped everything from the correct component ( b ) that the dump's content will be 'visible' and 'legible' (PACE 1984) and 'intelligible' (DPA1984).
Holding such a view doesn't mean, nor is it intented to suggest, that I think there is an impossibility here that cannot be overcome. Do I think the mobile forensic communty, working together, will find the solutions? Yes, absolutely, naturally.
Monday, June 27, 2011
iCloud MobileMe Quota Storage
iCloud MobileMe Quota Storage
As with most things in the digital world and examining evidence, it is essential for an examiner to understand the way in which a product or service works and the options that brings, as opposed to only considering the stored data that is discovered upon initial examination.
There has been alot of discussions in the forensic community about iCloud and its impact on off-device storage access and examination. Interesting to note then that MobileMe storage quotas are in place, as recently observed:
http://www.macrumors.com/2011/06/20/if-you-use-all-your-icloud-storage-apple-sends-you-this-email/
If the user only wants to keep to the 5GB limit and doesn't delete data and the devcie storage is equally full, is newer data automatically deleted or stored elsewhere? I only raise the point because with increased data flowing in and out of mobile phones, this could impact on data connected to one issue being spread across several storage locations.
As with most things in the digital world and examining evidence, it is essential for an examiner to understand the way in which a product or service works and the options that brings, as opposed to only considering the stored data that is discovered upon initial examination.
There has been alot of discussions in the forensic community about iCloud and its impact on off-device storage access and examination. Interesting to note then that MobileMe storage quotas are in place, as recently observed:
http://www.macrumors.com/2011/06/20/if-you-use-all-your-icloud-storage-apple-sends-you-this-email/
If the user only wants to keep to the 5GB limit and doesn't delete data and the devcie storage is equally full, is newer data automatically deleted or stored elsewhere? I only raise the point because with increased data flowing in and out of mobile phones, this could impact on data connected to one issue being spread across several storage locations.
Monday, June 06, 2011
D-Day 6th June
D-Day 6th June
I mentioned today's important date to a number of people. Quite a few had forgotten the date and mainly the younger generation didn't know about events that took place on this date back in 1944.
For anyone who may have missed it or might want to know more, here are some links providing the historical background.
NORMANDY LANDINGS
British Legion Remembrance d-day-65
Wikipedia Normandy Landings
Britannica DDay
Remembrance D-Day.html
Lifeformation D-Day
SCHOOL CHILDREN (CBBC)
BBC/CBBC D-Day
I mentioned today's important date to a number of people. Quite a few had forgotten the date and mainly the younger generation didn't know about events that took place on this date back in 1944.
For anyone who may have missed it or might want to know more, here are some links providing the historical background.
NORMANDY LANDINGS
British Legion Remembrance d-day-65
Wikipedia Normandy Landings
Britannica DDay
Remembrance D-Day.html
Lifeformation D-Day
SCHOOL CHILDREN (CBBC)
BBC/CBBC D-Day
Friday, June 03, 2011
Update on Forensic Webblog Posts
Update on Forensic Webblog Posts
-------------------------------------
Radio Survey Field Notes
CSA Training Explanatory Diagram
iOS 4.3.3 deletion of Location Cache
Requesting Cell Site Data
---------------------------------
Handset Examination in 1995
sn0wbreeze unthethering Windows iPhones
Symbian OS v9.4, Series 60 rel. 5
----------------------------
Answer To Reset (ATR)
Blackberry Forensic Analysis
--------------------------------
Vodafone CDR data
Mobile Evidence CDR/Billing Course
Call Detail Record (CDR) GSM Mobile Telephone Call
ABOUT THE BLOGS
I have endeavoured to be free with sharing knowledge and information over many years through my blogs, but given the changing economy, UK and global events and advancements in forensics, the nature of the technical content, new developments and examination techniques and legal information will only be accessible to approved law enforcement personnel, security specialists and authorised individuals. The following blogs are now approved access only:
Cell Site Analysis
http://cellsiteanalysis.blogspot.com
Forensic examination and evidence from SIM an USIM
http://sim2usim.blogspot.com
Forensic examination and evidence from Mobile and Smart Phones
http://forensicmobex.blogspot.com
Forensic analysis of Billing and CDR Records
http://cdranalysis.blogspot.com/
Mobile Telephone Evidence (http://trewmte.blogspot.com) will of course remain an open.
The criteria for authorised access to blogs:
a) Law Enforcement
b) Security Services (MI5, MI6, CID, SB, FBI....)
b1) Security Specialists - a proveable record in security for
networks, digital forensics, handsets, SIM, CDR etc
c) Authorised individuals
Cell Site Analysis
http://cellsiteanalysis.blogspot.com/-------------------------------------
Radio Survey Field Notes
CSA Training Explanatory Diagram
iOS 4.3.3 deletion of Location Cache
Requesting Cell Site Data
Forensic Mobile Examination
http://forensicmobex.blogspot.com---------------------------------
Handset Examination in 1995
sn0wbreeze unthethering Windows iPhones
Symbian OS v9.4, Series 60 rel. 5
Examination and Evidence from SIM and USIM Cards
http://sim2usim.blogspot.com----------------------------
Answer To Reset (ATR)
Blackberry Forensic Analysis
Billing & Call Detail Record Analysis
http://cdranalysis.blogspot.com/--------------------------------
Vodafone CDR data
Mobile Evidence CDR/Billing Course
Call Detail Record (CDR) GSM Mobile Telephone Call
ABOUT THE BLOGS
Mobile Telephone Blogs Approved Access Only
I have endeavoured to be free with sharing knowledge and information over many years through my blogs, but given the changing economy, UK and global events and advancements in forensics, the nature of the technical content, new developments and examination techniques and legal information will only be accessible to approved law enforcement personnel, security specialists and authorised individuals. The following blogs are now approved access only:
Cell Site Analysis
http://cellsiteanalysis.blogspot.com
Forensic examination and evidence from SIM an USIM
http://sim2usim.blogspot.com
Forensic examination and evidence from Mobile and Smart Phones
http://forensicmobex.blogspot.com
Forensic analysis of Billing and CDR Records
http://cdranalysis.blogspot.com/
Mobile Telephone Evidence (http://trewmte.blogspot.com) will of course remain an open.
The criteria for authorised access to blogs:
a) Law Enforcement
b) Security Services (MI5, MI6, CID, SB, FBI....)
b1) Security Specialists - a proveable record in security for
networks, digital forensics, handsets, SIM, CDR etc
c) Authorised individuals
Thursday, June 02, 2011
Radio Survey Field Notes
Radio Survey Field Notes
The CSA Training Explanatory Diagram illustrated (previous thread) some of the codes identified in the broadcast radio identities. At this stage the examiner/expert might want to get an early indicator of what this information could mean when attributed to other knowledge, previously acquired, about the target location of interest where radio test measurements are scheduled to be conducted.
Of course, if you have a keen eye you will note the document is not acquainted with complete pre-profiled cell site details. These details are excluded for a reason, which I shall come onto later. For now it is useful to analyse the Explanatory Diagram content and cross-reference it with the Radio Survey Field Notes.
Some questions:
- What sort of information do you think can be taken for granted that need not be included into the Field Notes that is in the Explanatory Notes?
- What identities are absence by their omission from the Field Notes that are in the Explanatory Diagram?
- Do you think those identities should be in the field notes?
The purpose of pushing these points is that often evidence is omitted and examiners/experts will certainly need that information to hand when preparing for their opinion, writing a report and giving evidence.
The CSA Training Explanatory Diagram illustrated (previous thread) some of the codes identified in the broadcast radio identities. At this stage the examiner/expert might want to get an early indicator of what this information could mean when attributed to other knowledge, previously acquired, about the target location of interest where radio test measurements are scheduled to be conducted.
Of course, if you have a keen eye you will note the document is not acquainted with complete pre-profiled cell site details. These details are excluded for a reason, which I shall come onto later. For now it is useful to analyse the Explanatory Diagram content and cross-reference it with the Radio Survey Field Notes.
Some questions:
- What sort of information do you think can be taken for granted that need not be included into the Field Notes that is in the Explanatory Notes?
- What identities are absence by their omission from the Field Notes that are in the Explanatory Diagram?
- Do you think those identities should be in the field notes?
The purpose of pushing these points is that often evidence is omitted and examiners/experts will certainly need that information to hand when preparing for their opinion, writing a report and giving evidence.
Wednesday, June 01, 2011
CSA Training Explanatory Diagram
CSA Training Explanatory Diagram
Given the huge range of knowledge and information needed for Cell Site Analysis (CSA) I have spent a considable amount of time creating many training sheets for the courses. The explanatory diagram below represents just some basic information acquired from radio tests and the meaning of the codes shown in the test screens.
This training document forms part of the procedure of a step-by-step guide in a long, long line of steps an trainee examiner will undertake and aids the trainee grasp the basics. Later the trainee will be shown additional information that isn't shown in the above diagram to extend knowledge and understanding.
Soon the examiner will come to realise that when I started out in an early thread in this blog identifying the elements in the GSM Radio DNA Bracelet I had a reason for doing that. The data displayed in the screens (like the ones above) occur as a consequence of being assigned to one or more of the logical channels identified in the GSM Radio DNA Bracelet delivered by the physical channels of the radio system.
Given the huge range of knowledge and information needed for Cell Site Analysis (CSA) I have spent a considable amount of time creating many training sheets for the courses. The explanatory diagram below represents just some basic information acquired from radio tests and the meaning of the codes shown in the test screens.
This training document forms part of the procedure of a step-by-step guide in a long, long line of steps an trainee examiner will undertake and aids the trainee grasp the basics. Later the trainee will be shown additional information that isn't shown in the above diagram to extend knowledge and understanding.
Soon the examiner will come to realise that when I started out in an early thread in this blog identifying the elements in the GSM Radio DNA Bracelet I had a reason for doing that. The data displayed in the screens (like the ones above) occur as a consequence of being assigned to one or more of the logical channels identified in the GSM Radio DNA Bracelet delivered by the physical channels of the radio system.
Monday, May 30, 2011
iOS 4.3.3 deletion of Location Cache
iOS 4.3.3 deletion of Location Cache
Apple responded in April 2011 to concerns in the marketplace about location data that enables a user to be tracked without their knowledge or without knowing such a mechanism existed in the iPhone:
http://www.apple.com/pr/library/2011/04/27location_qa.html
By 3rd May 2011 an early fix was suggested would be available pending the outcome of Beta tests. That the fix would deal with location backups to iTunes when Location Services was switched OFF.
On the 5th May the promised iOS patch to resolve the iPhone location tracking went live and reduced the size of the cache of information that had been backed up. Noticeable the cache file is now considerable smaller, however the size of the update to do that was over 650 megabytes.
Loss of evidence in the cache is one observation and another is with Location Services switched OFF on the handset this may impact on historical and current Cell Site Analysis investigations.
Apple responded in April 2011 to concerns in the marketplace about location data that enables a user to be tracked without their knowledge or without knowing such a mechanism existed in the iPhone:
http://www.apple.com/pr/library/2011/04/27location_qa.html
By 3rd May 2011 an early fix was suggested would be available pending the outcome of Beta tests. That the fix would deal with location backups to iTunes when Location Services was switched OFF.
On the 5th May the promised iOS patch to resolve the iPhone location tracking went live and reduced the size of the cache of information that had been backed up. Noticeable the cache file is now considerable smaller, however the size of the update to do that was over 650 megabytes.
Loss of evidence in the cache is one observation and another is with Location Services switched OFF on the handset this may impact on historical and current Cell Site Analysis investigations.
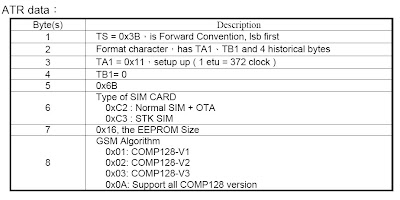
Answer To Reset (ATR)
Answer To Reset (ATR)
It is an endless investigation when dealing with SIM/USIM. The intention of this discussion is to highlight discoveries that you may not be aware. In this instance ATR is the first data read from every SIM/USIM and can provide potentially useful information to an investigation or when making analysis about end-to-end (SIM to Network) mobile telephone evidence.
What might be interpreted from first eight bytes of an ATR recovered? From research, this is an interpretation of the ATR from a particular manufacturer's GSM SIM:
[B1][B2][B3][B4][B5][B6][B7][B8]
3B....34...11...00...6B...C?..16...0?
Byte 6 - options
3B 34 11 00 6B C2 16 0? normal SIM+OTA
3B 34 11 00 6B C3 16 0? SIM-Toolkit (STK) SIM
Byte 7
16 EEPROM size (16K)
Byte 8 - options
3B 34 11 00 6B C? 16 01 GSM security algorithm
3B 34 11 00 6B C? 16 02
3B 34 11 00 6B C? 16 03
3B 34 11 00 6B C? 16 0A
It is an endless investigation when dealing with SIM/USIM. The intention of this discussion is to highlight discoveries that you may not be aware. In this instance ATR is the first data read from every SIM/USIM and can provide potentially useful information to an investigation or when making analysis about end-to-end (SIM to Network) mobile telephone evidence.
What might be interpreted from first eight bytes of an ATR recovered? From research, this is an interpretation of the ATR from a particular manufacturer's GSM SIM:
[B1][B2][B3][B4][B5][B6][B7][B8]
3B....34...11...00...6B...C?..16...0?
Byte 6 - options
3B 34 11 00 6B C2 16 0? normal SIM+OTA
3B 34 11 00 6B C3 16 0? SIM-Toolkit (STK) SIM
Byte 7
16 EEPROM size (16K)
Byte 8 - options
3B 34 11 00 6B C? 16 01 GSM security algorithm
3B 34 11 00 6B C? 16 02
3B 34 11 00 6B C? 16 03
3B 34 11 00 6B C? 16 0A
As interpretation of the ATR can be possible, do all SIM ATRs follow the same identification process or when personalised uniquely characterise the ATR to instruct the handset/network with similar information about the SIM's technical profiling but identified at different byte locations in the ATR string?
Saturday, May 28, 2011
Evolving Cell Site Analysis (CSA)
Evolving Cell Site Analysis (CSA)
In 23 years of dealing with a range of cellular radio systems TACS, GSM and WCDMA and, lately, a little of LTE, in addition to NFC work, generates a measured confidence in dealing with change when it occurs.
The word 'Re-farming' of 900 MHz , largely a play word, the core of which is based upon re-allocation of spectrum from one technology and service to another (eg GSM TDMA to 3G WCDMA), and local inter-operator roaming (Orange and T-Mobile) are two such changes to which CSA is exposed. These changes are, though, nothing more than evolution in a innovation driven and commercially challenging market place. Knowledge doesn't simply disappear overnight because these changes have occurred.
Operator and spectrum imposed changes appear to have generated perhaps understandable concerns, but the premise of these concerns might actually be based upon misconceptions about how those changes impact on cell site analysis. Concerns, such as, a no-can do approach; a patch fix is needed; the notion that is all you are going to get; to a loss of evidence with the introduction of changes, are a variety I have heard. The introduction of Everything Everywhere is another good example in point. Many of the constraints currently being purveyed in the marketplace would require ignoring a considerable body of information.
Photo courtesy of www.dailymail.co.uk article-0-001097AB00000258-251_468x315.jpg
Don't Panic Mr Mainwaring!! Simply running out with a piece of test equipment and having a few shots at a target, chatting with several people or referring to comments on the web really isn't appropriate qualification for the matter under scrutiny when one is not fully certain of (figuratively speaking) the enemy.
Cell site analysis doesn't suffer from evidential menigitis just because changes take place, as there are a huge range of factors and information that need to be considered first when making a diagnosis of the matter in order to determine a prognosis.
Thursday, May 19, 2011
Aggregated SIM
Aggregated SIM
Interesting news story out of Reuters that has been posted by many website that states that Apple has proposed a standardized SIM card smaller than those it currently uses in the iPhone and iPAD in order to be able to produce thinner devices, an Orange executive told Reuters on Tuesday. The news story also mentions Apple having gone along the Standards path and approached ETSI (European Telecommunications Standards Institute) and a hint that something could be seen as early as next year.
http://www.reuters.com/article/2011/05/17/us-summit-orange-apple-idUSTRE74G4WY20110517
This is SIM card developmental news and fascinating to watch as SIM and the microprocessor electronic card (ICC/UICC) that it uses takes further steps on its evolutionary journey. We already know some of the form factors for ICC/UICC:
The integrated and non-integrated examples

A closer look at an integrated example

When SIM (subscriber identity module) cards were introduced for GSM (global systems for mobile) communication devices (handset/terminal devices) ETSI standardised the ID-1 format which was an ISO-size card as defined in the international standard ISO-7816 and commonly referred to as a 'credit card' size. A plug-in size (the size of a 'postage stamp') was also introduced and these designs are commonly seen in the standard GSM11.11. Distinctively, the shape, size and operational performance of the card means that the card, called an ICC- integrated circuit card (or Universal ICC following the introduction of 3G-WCDMA cellular radio) - should be distinguished from the SIM module, which is itself a programmable area on the card. However, a further card size emerged and was defined in the 2004-03 ETSI standard TS 102.221 as "mini-UICC". It should be noted that where I have mentioned GSM11.11 this standard refers to the use of SIM cards with GSM technology and services. The lineage of GSM SIM and its standards are linked to ETSI standards including TS 102.221 and, of course, ISO standards. A similar path can be trod when dealing with U-ICC/U-SIM.
As for Apple's suggested development, what we don't know at this stage is what the aggregated SIM (but I think I might want to read that as form factor and size) will look like or its content for that matter. We can only guess at this stage.
Interesting news story out of Reuters that has been posted by many website that states that Apple has proposed a standardized SIM card smaller than those it currently uses in the iPhone and iPAD in order to be able to produce thinner devices, an Orange executive told Reuters on Tuesday. The news story also mentions Apple having gone along the Standards path and approached ETSI (European Telecommunications Standards Institute) and a hint that something could be seen as early as next year.
http://www.reuters.com/article/2011/05/17/us-summit-orange-apple-idUSTRE74G4WY20110517
This is SIM card developmental news and fascinating to watch as SIM and the microprocessor electronic card (ICC/UICC) that it uses takes further steps on its evolutionary journey. We already know some of the form factors for ICC/UICC:
The integrated and non-integrated examples

A closer look at an integrated example

When SIM (subscriber identity module) cards were introduced for GSM (global systems for mobile) communication devices (handset/terminal devices) ETSI standardised the ID-1 format which was an ISO-size card as defined in the international standard ISO-7816 and commonly referred to as a 'credit card' size. A plug-in size (the size of a 'postage stamp') was also introduced and these designs are commonly seen in the standard GSM11.11. Distinctively, the shape, size and operational performance of the card means that the card, called an ICC- integrated circuit card (or Universal ICC following the introduction of 3G-WCDMA cellular radio) - should be distinguished from the SIM module, which is itself a programmable area on the card. However, a further card size emerged and was defined in the 2004-03 ETSI standard TS 102.221 as "mini-UICC". It should be noted that where I have mentioned GSM11.11 this standard refers to the use of SIM cards with GSM technology and services. The lineage of GSM SIM and its standards are linked to ETSI standards including TS 102.221 and, of course, ISO standards. A similar path can be trod when dealing with U-ICC/U-SIM.
As for Apple's suggested development, what we don't know at this stage is what the aggregated SIM (but I think I might want to read that as form factor and size) will look like or its content for that matter. We can only guess at this stage.
Sunday, May 08, 2011
Forensic Mobile Examination Posts
Forensic Mobile Examination Posts
Latest posts at: http://forensicmobex.blogspot.com/
Nokia s40 Forensic Analysis - Call Release
Deleted Text Messages 3GS iPhones
Blackberry Forensic Analysis
The criteria for authorised access to cell site analysis blog is either:
a) Law Enforcement
b) Security Services (MI5, MI6, CID, SB, FBI....)
b1) Security Specialists - a proveable record in security for
networks, digital forensics, handsets, SIM, CDR etc
c) Authorised individuals (people whom I know)
Cell Site Analysis Posts
Cell Site Analysis Posts
Latest posts at: http://cellsiteanalysis.blogspot.com/
Requesting Cell Site Data
Blackberry Forensic Analysis
GSM Radio DNA Bracelet - RACH
GSM Radio DNA Bracelet
The criteria for authorised access to cell site analysis blog is either:
a) Law Enforcement
b) Security Services (MI5, MI6, CID, SB, FBI....)
b1) Security Specialists - a proveable record in security for
networks, digital forensics, handsets, SIM, CDR etc
c) Authorised individuals (people whom I know)
Requesting Cell Site Data
Requesting Cell Site Data
Engaging with defence solicitors or law enforcement with respect to seeking cell site evidence can be a tricky business. Invariably the request for data is largely governed by the type of case and the instruction of work. Problematical with the latter point is there maybe the notion that the person instructing actually has sufficient technical knowledge and understanding to comprehend the technical details to be analysed and the types of detail the CSA expert will need.
A mistake in common practice that I have noted with examiners and experts is to assume the CDR contains the complete cell site details, and clearly that cannot be the case. The structure and content of CDR vis-a-vis TAP files both are different and have different purposes, but ae not generated for the purposes to include cell site details. I have seen some company websites identifying themselves as experts and suggesting cell site details are found in extended CDRs. I do not agree as cell site details have absolutely nothing to do with a generated per call CDR or indeed TAP file for that matter. There are a minimal references to cell sites by way of cell ID (start/end) and a few other bits and pieces, but nothing more would be generated by the mobile phone, radio network, the switch or data capture machine for inclusion into a CDR/TAP file.
Another matter I have noted, when dealing with expert and examiner cell site reports and those conducting radio test measurements is this vague suggestion allude to an implicit fact that because the examiner took GPS measurements when conducting tests this somehow creates a fact that the cellular radio coverage is corroborated by this or the movements of the handset user is somehow tracked this way. There appears on the face of it at least a confusion between GPS and the mobile network. Neither GSM or WCDMA propagate GPS signals, merely they take data output in the form of a packet of data from a GPS module/unit and forward that packet through the device/network to the terminal that will somehow make use of the data. If I need support for that fact then I find it at first instance in the radio frequencies adopted for GSM and WCDMA and from which all else will follow when dealing with cellular radio propagation and communications.
So what are the data field elements that the examiner/expert might seek at first instance. Clearly there needs to be corroboration of a GSM originated/terminated and start and/or end of a mobile communication. The list below is not data (email/internet/download etc) communication related.
----------------------------------------
Date ?
Time ?
Calling party ?
Called party ?
Type of call ?
Duration ?
Registration (ringing time before answer) ?
Mast location Details for start of call
---------------------------------------
[Start of call] Site ID number?
[Start of call] Site Name?
[Start of call] Site Address?
[Start of call] Site Post code?
[Start of call] Type of transmission 3G WCMDA site or GSM site?
[Start of call] Frequency Range?
[Start of call] Macrocell or Microcell?
[Start of call] Height of Antennas?
[Start of call] Is this a omni-directional site?
[Start of call] How many sectors at site (e.g. 3, 6 etc)?
[Start of call] Easting and Northing?
[Start of call] Longitude and Latitude?
[Start of call] Cell ID (hex)?
[Start of call] Cell ID (dec)?
[Start of call] Cell ID (last digit as sector)?
[Start of call] Broadcast Control Channel (BCCH) number?
[Start of call] Azimuth (bearing of coverage)?
Mast location Details for end of call
-------------------------------------
[End of call] Site ID number?
[End of call] Site Name?
[End of call] Site Address?
[End of call] Site Post code?
[End of call] Type of transmission 3G WCMDA site or GSM site?
[End of call] Frequency Range?
[End of call] Macrocell or Microcell?
[End of call] Height of Antennas?
[End of call] Is this a omni-directional site?
[End of call] How many sectors at site (e.g. 3, 6 etc)?
[End of call] Easting and Northing?
[End of call] Longitude and Latitude?
[End of call] Cell ID (hex)?
[End of call] Cell ID (dec)?
[End of call] Cell ID (last digit as sector)?
[End of call] Broadcast Control Channel (BCCH) number?
[End of call] Azimuth (bearing of coverage)?
The cell site details should relate at minimum to the material time of the mobile communications and at least upto the date the request for information is being made in order to comprehend any changes at the Masts for the Mast that handled the start of the call and the Mast that handled the end of the call.
Request notification of any Mast alterations
-----------------------------------------
[Any change to Mast] Decommissioned?
[Any change to Mast] Height of Antenna altered?
[Any change to Mast] Azimuth Bearing of coverage?
[Any change to Mast] Mechanical or electrical tilt changes and to what degree?
[Any change to Mast] Licenced Power or Transmission power?
[Any change to Mast] Type of transmission from 2G GSM to 3G WCDMA or vice versa?
It is quite possible to seek considerably more about the arrangements at each Mast, but that often means dealing with each operator's specific matters on a case by case basis. These elements are not included here.
Saturday, May 07, 2011
GSM Radio DNA Bracelet - RACH
GSM Radio DNA Bracelet - RACH (Random Access Channel)
The logical channels set out http://cellsiteanalysis.blogspot.com/2011/01/gsm-radio-dna-bracelet.html each provide useful information that is of use to cell site analysis (CSA). A common misunderstanding that arises with CSA is it has been used in evidence in such away that only a minutiae of information is considered. This in turn has led to some believing CSA can be defined by a limited selection of elements. The world of CSA is far, far larger in rich content than those limited elements. An examiner only comes to know about the rich content having first applied him/herself to learning the symbiotic, co-partnership between the science & technology and examination & forensic procedure leading to evidence & opinion.
For instance let us accept that RACH is a GSM uplink common control channel. In that little nugget of information given by the statement there is firstly the science and technology. The technology is Global System for Mobile (communications) a digital cellular radio system. The adopted GSM system manipulates (modulates) the physical radio signals such that physical signals whilst analogue in nature when manipulated hold a secret inside that is revealed when de-modulated revealing the important data (digital). Moreover, the statement uplink is relevant to note, as is common control channel (CCCH). There are four nominated logical control channel assigned connected with CCCH - Paging Channel (PCH), Access Grant Channel (AGCH), Notification Channel (NCH) and, of course, RACH. The term 'common' needs clarification, too, because it identifies that the channels are common to all users (mobile users) in a geographical radio area via their handsets. 'Uplink' defines the direction to which the control channel data are transmitted.
In combination, the examination of transmitted data becomes highly significant for it represent an action by the user's mobile phone creating the 'first' step in radio DNA evidence. A Layer 3 trace (example below), and when we say Layer 3 we are taking about RR (radio resources), identifies the access request RACH message sent to the network and a response from the network to it. The example below has been extrapolited (thus goes beyond) what would normally be seen from the raw data. The network and handset are programmed to understand each other and do not needs man's convoluted and verbose explanations but should the machinery, so to speak, need such explanation, god help us, for access to the GSM radio network would probably take three months just to camp on the network without using further resources.
Equally, for cell site analysis we need to know what information can be gleaned from RACH. The image below identifies a screen from an Ericsson handset with TEMS pocket (a radio diagnostic tool) in active mode. I will deal with the paging details in another discussion thread.
We first see the string '0 1 4 1 0E'. The point to note is that it only contains basic GSM info and not GPRS. Had it included GPRS info the string would consist of seven different separate elements instead of five. So how do we understand the order in which the data appears?
First element '0': refers to Cell Barred (0: No, 1: Yes)
Second element '1': refers to Call Re-establishment (0: Allowed, 1: Not allowed)
Third element '4': refers to Max number of retransmissions (1, 2, 4, 7)
Fourth element '1': refers to Number of RACH bursts sent for the last connection (1–7)
Fifth element '0E': refers to Establishment Cause/Random: Reference used in the latest RACH burst (00–FF)
The fifth element is, as referred to above, the 'first' step in radio DNA evidence. As this is generated by the user's handset it makes it interesting as it shows the examiner has understanding of seeking out evidence from the science and technology under test and that the data should be obtained using forensic methodology to secure unaltered data. Importantly, it illustrates to the examiner how to start to establish a link within the chain of data created by a mobile phone from when it is first switched ON, when using resources, until it it is switched OFF.
The actually RACH access request generated is no more than 8-bits in length. The GSM standard TS04.08 defines the message content format as seen below:
How to interpret the access request message content for establishment cause can be found in TS04.08:
And when the mobile is answering to paging for radio resources connection establishment.
There is so much detail associated with RACH it is possible to write a book solely dealing with this single subject. I do not have the time or luxury to put all that detail here, but to provide a flavour to you that the radio DNA evidence in the bracelet contains a gold mine of evidential information that is largely and randomly ignored and apparently seen by some as not being relevant. I wonder with the little I have mentioned above whether you would think the same?
In the next RACH discussion I shall open up to you more and give insight into RACH and some evidential possibilities.
The logical channels set out http://cellsiteanalysis.blogspot.com/2011/01/gsm-radio-dna-bracelet.html each provide useful information that is of use to cell site analysis (CSA). A common misunderstanding that arises with CSA is it has been used in evidence in such away that only a minutiae of information is considered. This in turn has led to some believing CSA can be defined by a limited selection of elements. The world of CSA is far, far larger in rich content than those limited elements. An examiner only comes to know about the rich content having first applied him/herself to learning the symbiotic, co-partnership between the science & technology and examination & forensic procedure leading to evidence & opinion.
For instance let us accept that RACH is a GSM uplink common control channel. In that little nugget of information given by the statement there is firstly the science and technology. The technology is Global System for Mobile (communications) a digital cellular radio system. The adopted GSM system manipulates (modulates) the physical radio signals such that physical signals whilst analogue in nature when manipulated hold a secret inside that is revealed when de-modulated revealing the important data (digital). Moreover, the statement uplink is relevant to note, as is common control channel (CCCH). There are four nominated logical control channel assigned connected with CCCH - Paging Channel (PCH), Access Grant Channel (AGCH), Notification Channel (NCH) and, of course, RACH. The term 'common' needs clarification, too, because it identifies that the channels are common to all users (mobile users) in a geographical radio area via their handsets. 'Uplink' defines the direction to which the control channel data are transmitted.
In combination, the examination of transmitted data becomes highly significant for it represent an action by the user's mobile phone creating the 'first' step in radio DNA evidence. A Layer 3 trace (example below), and when we say Layer 3 we are taking about RR (radio resources), identifies the access request RACH message sent to the network and a response from the network to it. The example below has been extrapolited (thus goes beyond) what would normally be seen from the raw data. The network and handset are programmed to understand each other and do not needs man's convoluted and verbose explanations but should the machinery, so to speak, need such explanation, god help us, for access to the GSM radio network would probably take three months just to camp on the network without using further resources.
Equally, for cell site analysis we need to know what information can be gleaned from RACH. The image below identifies a screen from an Ericsson handset with TEMS pocket (a radio diagnostic tool) in active mode. I will deal with the paging details in another discussion thread.
We first see the string '0 1 4 1 0E'. The point to note is that it only contains basic GSM info and not GPRS. Had it included GPRS info the string would consist of seven different separate elements instead of five. So how do we understand the order in which the data appears?
First element '0': refers to Cell Barred (0: No, 1: Yes)
Second element '1': refers to Call Re-establishment (0: Allowed, 1: Not allowed)
Third element '4': refers to Max number of retransmissions (1, 2, 4, 7)
Fourth element '1': refers to Number of RACH bursts sent for the last connection (1–7)
Fifth element '0E': refers to Establishment Cause/Random: Reference used in the latest RACH burst (00–FF)
The fifth element is, as referred to above, the 'first' step in radio DNA evidence. As this is generated by the user's handset it makes it interesting as it shows the examiner has understanding of seeking out evidence from the science and technology under test and that the data should be obtained using forensic methodology to secure unaltered data. Importantly, it illustrates to the examiner how to start to establish a link within the chain of data created by a mobile phone from when it is first switched ON, when using resources, until it it is switched OFF.
The actually RACH access request generated is no more than 8-bits in length. The GSM standard TS04.08 defines the message content format as seen below:
How to interpret the access request message content for establishment cause can be found in TS04.08:
And when the mobile is answering to paging for radio resources connection establishment.
There is so much detail associated with RACH it is possible to write a book solely dealing with this single subject. I do not have the time or luxury to put all that detail here, but to provide a flavour to you that the radio DNA evidence in the bracelet contains a gold mine of evidential information that is largely and randomly ignored and apparently seen by some as not being relevant. I wonder with the little I have mentioned above whether you would think the same?
In the next RACH discussion I shall open up to you more and give insight into RACH and some evidential possibilities.
Monday, May 02, 2011
Sir Henry Cooper World Boxing Legend Has Died
Sir Henry Cooper World Boxing Legend Has Died
Sir Henry Cooper, a boxing legend to British boxing fans and boxing fans all over the world, has died. A great advocate and ambassador for boxing, to me Sir Henry was a Gentleman Boxer, an advocate for fair play and clean boxing in the sport. A great man of his time, a World class boxer. Respects and commiserations to his family.
Photo courtesy of::
http://www.solarnavigator.net/sport/sport_images/henry_cooper.jpg
Daily Telegraph report:
http://www.telegraph.co.uk/sport/othersports/boxingandmma/8487084/Sir-Henry-Cooper-the-former-boxer-dies-aged-76.html
Sunday, April 24, 2011
Faraday containers found unsafe
Faraday containers found unsafe
A report that focuses on the results, following conducted practical tests, on the reliability of mobile phone shielding devices (eg 'faraday' containers) found the device shielding failed in a number of instances that the author of the report placed under test and did not prevent RF signalling reaching the test mobile phones inside the containers, the findings in this recently published paper suggests:
https://www.cerias.purdue.edu/assets/pdf/bibtex_archive/2010-27.pdf
The implications might require that an 'impact assessment' on evidence that is seized and placed in shielding devices at the scene of a crime and transported from Police Station to Police Station etc may need to be 'reconducted'. The findings in the report raise the notion whether published Guidelines advocating the use of shielding devices may now need to identify exactly the tests and research considered prior to adopting published policy on the use of shielding devices, although it is unclear at present whether that will happen at all.
Whilst the report dealt primarily with external factors (radio communications) and how the shielding devices coped with them, it also includes some other influences shielding devices can have on touch screen mobile phones, for example.
There have previously been mixed reviews about shielding devices and their impact on seized evidence that is left switched ON within shielding containers:
http://www.forensicfocus.com/index.php?name=Forums&file=viewtopic&t=3914
http://www.forensicfocus.com/index.php?name=Forums&file=viewtopic&t=4277&postdays=0&postorder=asc&start=0
If a mobile phone is already OFF, or is switched OFF at the point of seizure, then such shielding devices shouldn't be necessary at that particular juncture.
A report that focuses on the results, following conducted practical tests, on the reliability of mobile phone shielding devices (eg 'faraday' containers) found the device shielding failed in a number of instances that the author of the report placed under test and did not prevent RF signalling reaching the test mobile phones inside the containers, the findings in this recently published paper suggests:
https://www.cerias.purdue.edu/assets/pdf/bibtex_archive/2010-27.pdf
The implications might require that an 'impact assessment' on evidence that is seized and placed in shielding devices at the scene of a crime and transported from Police Station to Police Station etc may need to be 'reconducted'. The findings in the report raise the notion whether published Guidelines advocating the use of shielding devices may now need to identify exactly the tests and research considered prior to adopting published policy on the use of shielding devices, although it is unclear at present whether that will happen at all.
Whilst the report dealt primarily with external factors (radio communications) and how the shielding devices coped with them, it also includes some other influences shielding devices can have on touch screen mobile phones, for example.
There have previously been mixed reviews about shielding devices and their impact on seized evidence that is left switched ON within shielding containers:
http://www.forensicfocus.com/index.php?name=Forums&file=viewtopic&t=3914
http://www.forensicfocus.com/index.php?name=Forums&file=viewtopic&t=4277&postdays=0&postorder=asc&start=0
If a mobile phone is already OFF, or is switched OFF at the point of seizure, then such shielding devices shouldn't be necessary at that particular juncture.
Easter Remembered
Easter Remembered
I thought I would post this as in the news this Easter period it has been suggested Christian beliefs are declining. This may be so, or it might not be so. Britain has had to absurb some huge changes of the last two decades, cultural and otherwise, with little or no time to stop and pores for thought and to understand what those changes actually meant and mean.
I am not so sure that Christian belief is declining or any other faith-belief for that matter. Merely people are walking away from confrontation where religious beliefs, that are deeply personal to each of us, are used daily as political or scaremongering ends of some sort or other.
This poem was given to me at Easter when I was sixteen. I enjoy the poem as I like the connotation the name 'Abou Ben Adams' brings. For it seems not to matter if the person is black, white, brown, yellow..., christian, muslim or jew...., and so on. All these matters are set aside to express a personal wish, a desire, a belief. As Easter is the time to remember in the Christian calender this poem reflects many of the doctrines set out in the tenets of the Christian faith. It may also be reflected in the tenets of many other faith-beliefs, too.
============================
Abou Ben Adam, may his tribe increase,
Awoke one night from a sweet dream of peace,
And saw within the moonlight in his room,
Painting it rich, like a lilly in bloom
An Angel wirting in a book of gold.
Exceeding peace had made Ben Adam bold,
And to the presence in the room he asked,
"What writeth thou", the vision raid its head,
And with a look made of all sweet accord, replied,
"The names of those who love the Lord".
"And is mine one" said Abou?
"Ney no so replied" the Angel.
Abou spoke more low, but cheerily still and said,
"I pray thee then, write me as one who loves his fellow men".
The Angel wrote and vanished.
The next night it came again with a great wakening light
And showed teh names of those whom love of God had blessed
And lo, Ben Adams name led all the rest.
=============================
http://trewmte.blogspot.com/2009/02/god-is-wireless-scientist-too.html
I trust everyone had a great St George's Day, yesterday, 23rd April 2011
http://trewmte.blogspot.com/2010/04/st-georges-day-23rd-april.html
I thought I would post this as in the news this Easter period it has been suggested Christian beliefs are declining. This may be so, or it might not be so. Britain has had to absurb some huge changes of the last two decades, cultural and otherwise, with little or no time to stop and pores for thought and to understand what those changes actually meant and mean.
I am not so sure that Christian belief is declining or any other faith-belief for that matter. Merely people are walking away from confrontation where religious beliefs, that are deeply personal to each of us, are used daily as political or scaremongering ends of some sort or other.
This poem was given to me at Easter when I was sixteen. I enjoy the poem as I like the connotation the name 'Abou Ben Adams' brings. For it seems not to matter if the person is black, white, brown, yellow..., christian, muslim or jew...., and so on. All these matters are set aside to express a personal wish, a desire, a belief. As Easter is the time to remember in the Christian calender this poem reflects many of the doctrines set out in the tenets of the Christian faith. It may also be reflected in the tenets of many other faith-beliefs, too.
============================
Abou Ben Adam, may his tribe increase,
Awoke one night from a sweet dream of peace,
And saw within the moonlight in his room,
Painting it rich, like a lilly in bloom
An Angel wirting in a book of gold.
Exceeding peace had made Ben Adam bold,
And to the presence in the room he asked,
"What writeth thou", the vision raid its head,
And with a look made of all sweet accord, replied,
"The names of those who love the Lord".
"And is mine one" said Abou?
"Ney no so replied" the Angel.
Abou spoke more low, but cheerily still and said,
"I pray thee then, write me as one who loves his fellow men".
The Angel wrote and vanished.
The next night it came again with a great wakening light
And showed teh names of those whom love of God had blessed
And lo, Ben Adams name led all the rest.
=============================
http://trewmte.blogspot.com/2009/02/god-is-wireless-scientist-too.html
I trust everyone had a great St George's Day, yesterday, 23rd April 2011
http://trewmte.blogspot.com/2010/04/st-georges-day-23rd-april.html
Sunday, March 06, 2011
MTEB - International Mobile Forensics Conference 2011
MTEB - International Mobile Forensics Conference 2011
2011 International Conference presentations and workshops:
- Session 1 The Impact of Mobile Cybercrime
- Session 2 iPhone, Android, Microkia, Blackberry et al
- Session 3 New crimes require new mobile examination methods
- Session 4 Forensic Mobile SSD FTL & Chip Off
- Session 5 Imaging and Data Carving
- Session 6 Indepth with SIM & USIM Examination
- Session 7 Achieving Laboratory Accreditation
- Session 8 Forensic Tools - Performance & Evaluation
- Session 9 Security and deleted data on mobile devices
- Session 10 Hacks, Cracks and Whacks
- Session 11 Cell Site Analysis
- Session 12 Forensic Mobile Computing Laptops to Pads & Tablets
- Session 13 Employment and Market Trends
- Session 14 GSM/WCDMA/GPS Jammers and examination methodology
- Session 15 Call Record Analysis
- Session 16 Student Presentation
- Session 17 Mobile Phone Programming
- Session 18 Wireless technology comparisons
- Session 19 Handset Examination
- Session 20 Wireless technology comparisons
- Session 21 An expert's view of mobile phone evidence
- Session 22 Retained Data: Handover Interface for the request and delivery of retained data
- Session 23 Standards Review
- Session 24 UK perspective - the future of Law Enforcement's involvement in mobile forensics
- Session 25 A Practitioner's view of moble phone examination
- Session 9 Security and deleted data on mobile devices
- Session 10 Hacks, Cracks and Whacks
- Session 11 Cell Site Analysis
- Session 12 Forensic Mobile Computing Laptops to Pads & Tablets
- Session 13 Employment and Market Trends
- Session 14 GSM/WCDMA/GPS Jammers and examination methodology
- Session 15 Call Record Analysis
- Session 16 Student Presentation
- Session 17 Mobile Phone Programming
- Session 18 Wireless technology comparisons
- Session 19 Handset Examination
- Session 20 Wireless technology comparisons
- Session 21 An expert's view of mobile phone evidence
- Session 22 Retained Data: Handover Interface for the request and delivery of retained data
- Session 23 Standards Review
- Session 24 UK perspective - the future of Law Enforcement's involvement in mobile forensics
- Session 25 A Practitioner's view of moble phone examination
There will be a good selection of speakers and presentations. Remember this is a learning conference and due to timings - speakers -v- workshops - the streams occur in some instances at the same time. It would be within your interest to book at least two people to attend the conference. One to listen to the Conference Speakers and the other to attend training workshops. Session presentations or workshops maybe subject to change.
Saturday, March 05, 2011
Passcode locked iPhone may still make calls
Passcode locked iPhone may still make calls
We have known for awhile that many users can answer calls on their bluetooth earpiece even though they have the phone keypad lock set to ON. Moreover, handsets like Samsung GT-S5600 with keypad lock ON that have a synchronised bluetooth earpiece can call the last number received (LNR) or the number of the last received text message by simply pushing the key on the earpiece. Even if the user isn't using bluetooth earpiece, many handsets (eg Nokia 6303) with a locked keypad can still allow the user to answer a ringing phone.
If you have a passcode lock on your iPhone it is possible, where the owner haven't yet changed the voice default security setting from when it was purchased, to still be able to make phone calls or worst still it can allow a thief (if your iPhone is stolen) to make calls with the handset. By switching the default setting to OFF can help prevent this occur.
The image courtesy of The Register
The passcode lock vulnerability has been reaffirmed in a recent article published at the technology website, The Register: http://www.theregister.co.uk/2011/03/04/iphone_voice_dialling/.
Thursday, March 03, 2011
Cell Phone Use May Have Effect On Brain Activity
Cell Phone Use May Have Effect On Brain Activity, But Health Consequences Unknown
February 28, 2011
"The dramatic worldwide increase in use of cellular telephones has prompted concerns regarding potential harmful effects of exposure to radiofrequency-modulated electromagnetic fields (RF-EMFs). Of particular concern has been the potential carcinogenic effects from the RF-EMF emissions of cell phones. However, epidemiologic studies of the association between cell phone use and prevalence of brain tumors have been inconsistent (some, but not all, studies showed increased risk), and the issue remains unresolved," according to background information in the article. The authors add that studies performed in humans to investigate the effects of RF-EMF exposures from cell phones have yielded variable results, highlighting the need for studies to document whether RF-EMFs from cell phone use affects brain function in humans.
Nora D. Volkow, M.D., of the National Institutes of Health, Bethesda, Md., and colleagues conducted a study to assess if cell phone exposure affected regional activity in the human brain. The randomized study, conducted between January 1 and December 31, 2009, included 47 participants. Cell phones were placed on the left and right ears and brain imaging was performed with positron emission tomography (PET) with (18F)fluorodeoxyglucose injection, used to measure brain glucose metabolism twice, once with the right cell phone activated (sound muted) for 50 minutes ("on" condition) and once with both cell phones deactivated ("off" condition). Analysis was conducted to verify the association of metabolism and estimated amplitude of radiofrequency-modulated electromagnetic waves emitted by the cell phone. The PET scans were compared to assess the effect of cell phone use on brain glucose metabolism.
The researchers found that whole-brain metabolism did not differ between the on and off conditions. However, there were significant regional effects. Metabolism in the brain region closest to the antenna (orbitofrontal cortex and temporal pole) was significantly higher (approximately 7 percent) for cell phone on than for cell phone off conditions. "The increases were significantly correlated with the estimated electromagnetic field amplitudes both for absolute metabolism and normalized metabolism," the authors write. "This indicates that the regions expected to have the greater absorption of RF-EMFs from the cell phone exposure were the ones that showed the larger increases in glucose metabolism."
"These results provide evidence that the human brain is sensitive to the effects of RF-EMFs from acute cell phone exposures," the researchers write. They add that the mechanisms by which RF-EMFs could affect brain glucose metabolism are unclear.
"Concern has been raised by the possibility that RF-EMFs emitted by cell phones may induce brain cancer. ... Results of this study provide evidence that acute cell phone exposure affects brain metabolic activity. However, these results provide no information as to their relevance regarding potential carcinogenic effects (or lack of such effects) from chronic cell phone use."
"Further studies are needed to assess if these effects could have potential long-term harmful consequences," the authors conclude. (JAMA 2011;305[8]:808-814. Available pre-embargo to the media at www.jamamedia.org)
Cell Phone Radiofrequency Radiation Exposure and Brain Glucose Metabolism
The results of this study add information about the possible effects of radiofrequency emissions from wireless phones on brain activity, write Henry Lai, Ph.D., of the University of Washington, Seattle, and Lennart Hardell, M.D., Ph.D., of University Hospital, Orebro, Sweden, in an accompanying editorial.
"Although the biological significance, if any, of increased glucose metabolism from acute cell phone exposure is unknown, the results warrant further investigation. An important question is whether glucose metabolism in the brain would be chronically increased from regular use of a wireless phone with higher radiofrequency energy than those used in the current study. Potential acute and chronic health effects need to be clarified. Much has to be done to further investigate and understand these effects."
The editorial authors also question whether the findings of Volkow et al may be a marker of other alterations in brain function from radiofrequency emissions, such as neurotransmitter and neurochemical activities? "If so, this might have effects on other organs, leading to unwanted physiological responses. Further studies on biomarkers of functional brain changes from exposure to radiofrequency radiation are definitely warranted."
SOURCE: American Medical Association
Previous discussions about Mobile Phones and Health:
http://trewmte.blogspot.com/2009/09/cellphones-cause-brain-tumors.html
Sunday, February 27, 2011
What comparisons between Taser and Stun Gun Mobile Phones?
What comparisons between Taser and Stun Gun Mobile Phones?
There is an interesting video released out on BLUtube about the potential understanding of a forensic component occurring within the use of Taser. The component relates to Taser discharge, as opposed to the actual result impacting on the target-human body.
The observations in the video nonetheless are only one dimension of the 'stun' story and, whilst useful, it would be interesting to see whether MSc/PhD students (always looking for dissertation ideas) would conclude similar forensic components exists when it comes to mobile phones that have stun capability?:
http://trewmte.blogspot.com/2007/10/another-mobile-telephone-stun-gun.html
http://trewmte.blogspot.com/2007/07/stun-gun-cellphone.html
Sunday, February 20, 2011
Mobile Phone Chip Off
Mobile Phone Chip Off
If you have produced or know of a mobile phone chip off video showing methods and techniques for removing ICs/memory from various makes/models of mobile handsets then email (trewmte@gmail.com) your youtube link and then it can be added to the thread 'Mobile Phone Chip Off'.
UPDATED:
Thank you Paul for this N70 video
Nathan, thanks for the SonyEricsson W850 video
Another SE W850 video
Nokia UEM removal
Friday, February 04, 2011
Mobile Device Tech-Genetics
Mobile Device Tech-Genetics
I assume mobile phone examinations will start to see the introduction of mobile devices with human thumbs connected to them being brought into the Lab. Testing the thumbs for evidence wont be a problem. DNA and fingerprinting is common for mobile devices and their associated SIM/USIM/Memory Cards. But just how TFK (Trew Forensic Kit), Oxygen Forensics, Cellebrite, XRY, MobilEdit etc will cope with the thumbs, which provides the interface to the device, is another matter. Perhaps this requires developing some type of tech-generic ears that act as couplers/data interface in which to stick those thumbs, no!?
Future possibilities of video streaming data straight to the brain could also be offered, too. A commercial service of 100 megeBytes download at £16.50 a month, may be? I can visualise the advertisement: 'We make worthwhile products, even better. The Trewly best ideas are why Trew are the market innovator and leader.' Well, why not, everyone else says it.....
.....anyone got the number for the Stock Exchange?
The video, by the way, is courtesy of Sony Ericsson Xperia Play commercial available on YouTube.
Labels:
DEEU,
DNA,
Droid,
ears,
fingerprint,
games,
gaming,
iPhones,
mobile phone examination,
Sony Ericsson,
Stock Exchange,
Stocks and Shares,
tech-genetics,
thumbs,
Trew Forensic Kit (TFK),
Xperia
Subscribe to:
Posts (Atom)