
Investigations, Practices and Procedures: Seizure-Forensic Examination-Evidence. Cellular and Satellite Telephones, Call Records-Billing Data, Cell Site Analysis. Telecomms. Computer and Network Analysis. GPS devices & Jammers, Cyber, IoT forensics.
Friday, February 23, 2007
Can you help?

Thursday, February 22, 2007
Is your cell phone bugged
Vortex (a US company) has produced an online Video, which they say is "to explain this issue in a more demonstrative and somewhat less technical manner..."
http://video.google.com/videoplay?docid=-3437321657032158285&hl=en
It raises some quizzical issues. This is not my attempt to be dismissive of what they are saying, but I could not help but think it does rely upon the subjectivity of each mobile phone user to perhaps determine if their battery runs down too quickly or the handset gets hot when not in use that information is being extracted from it.
The video authors do stress that any such use of monitoring mobile phones is not targetted at the general public, but those under surveillance. But that in itself may not stop the general public thinking something maybe up if they find the events occurring that have been suggested .
Whilst videos like this can be informative, they can introduce feelings of worry or paranoia to those who maybe vulnerable to such feelings. Perhaps it might assist, if a mobile phone user thinks this is happening to first rule out common events that the mobile phone may be exposed to:
The mobile
A) had been left in direct sunlight
B) left close to a radiator or devices that emit heat generally in areas (kettles, photocopiers, computers/laptops etc)
C) that the user hasn't just taken the mobile phone out of the coat pocket (obvious I know, but worth saying anyway)
D) reduction in battery power occurs because of resource greedy applications running on the mobile phone
E) does update to the network and in areas were poor radio coverage pockets occur or where the mobile is located at the radio boundary of a Mast's coverage, updating to the network does increase energy consumption (drawn from the battery)
F) where a mobile phone is swtiched OFF and battery still runs low, it could be a fault of a bleed from the battery or that the mobile's firmware is faulty regarding e.g. the clock and draws more power from the battery at a higher rate
G) using broadband might require the ISP or application service to 'ping' the mobile to ensure the account is still connected, which might be a separate event from updating to the network regarding the subscriber IMSI-attach status for example
These are just some observations that might help, but if a mobile user is still concerned, the video does demonstrate a detection method using speakers. But even that may produce a false-positive result. There is of course another method that may eliminate this matter which the video suggests is to remove the mobile phone's battery. OK, but that doesn't take account of when the mobile is switched ON and in the idle mode. If the mobile user still feels uncomfortable, then change to a different or new mobile phone.
Monday, February 19, 2007
USB Profiler mobile 'phone examination
 Ever found it annoying, like I have, when trying to examine mobile 'phones and SIMs/USIMs that given the fast range of applications and USB plug-in devices to be used it becomes difficult to know which USB connections are actually running on the computer. That means not just USB devices logged as previously being used but whether there is a live-link currently running. As always it is the simple, straightforward programs that make our lives so much easier. USBDeview profiles all USB connections and provides a global view of activity on your computer. You could of course spend time scrolling through DeviceManager...but that can be long winded. This freeware program speeds up the detection process. Enjoy.
Ever found it annoying, like I have, when trying to examine mobile 'phones and SIMs/USIMs that given the fast range of applications and USB plug-in devices to be used it becomes difficult to know which USB connections are actually running on the computer. That means not just USB devices logged as previously being used but whether there is a live-link currently running. As always it is the simple, straightforward programs that make our lives so much easier. USBDeview profiles all USB connections and provides a global view of activity on your computer. You could of course spend time scrolling through DeviceManager...but that can be long winded. This freeware program speeds up the detection process. Enjoy.USB Profiler mobile 'phone examination
 Ever found it annoying, like I have, when trying to examine mobile 'phones and SIMs/USIMs that given the fast range of applications and USB plug-in devices to be used it becomes difficult to know which USB connections are actually running on the computer. That means not just USB devices logged as previously being used but whether there is a live-link currently running. As always it is the simple, straightforward programs that make our lives so much easier. USBDeview profiles all USB connections and provides a global view of activity on your computer. You could of course spend time scrolling through DeviceManager...but that can be long winded. This freeware program speeds up the detection process. Enjoy.
Ever found it annoying, like I have, when trying to examine mobile 'phones and SIMs/USIMs that given the fast range of applications and USB plug-in devices to be used it becomes difficult to know which USB connections are actually running on the computer. That means not just USB devices logged as previously being used but whether there is a live-link currently running. As always it is the simple, straightforward programs that make our lives so much easier. USBDeview profiles all USB connections and provides a global view of activity on your computer. You could of course spend time scrolling through DeviceManager...but that can be long winded. This freeware program speeds up the detection process. Enjoy.Friday, February 16, 2007
GPS Mobile Phone Computer Training Shoes

To find out more click on the Technologies tab at the bottom of home page - http://www.isaacdaniel.com/fele.htm
Saturday, February 03, 2007
GSM Radio Test Measurements - Non-Dominance
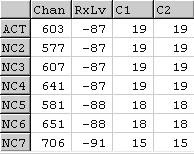 Screen Image 1
Screen Image 1Readers and cell site analysis students will recall the thread at http://trewmte.blogspot.com/2007/01/gsm-radio-test-measurements.html regarding GSM Radio Test Measurements. In that thread the discussion related to possible anomalies and interpretation regarding radio test measurements. In this thread I want to highlight another radio anomaly termed non-dominance that may occur.
Generally speaking, non-dominance occurs when radio coverage from two or more radio sources are equally aligned so that they all become dominant. The rare event in Screen Image 1 displays coverage quality and signal strengths of four radio sources are all equal to each other, in a confined area, where the receiver is in the idle mode and at ground level. Attempting to define that one particular Mast would be used to make or receive a mobile call in these circumstances might be difficult. The problems interpreting outcomes due to non-dominance could be numerous. For instance:
i) Who is to say that the receiver camped on a Mast's coverage shown by ACT would actually use that Mast? The coverage at NC2, NC3 and NC4 are equally as likely to be candidates to carry a mobile call.
ii) What happens in the case that the Mast's coverage upon which the receiver is camped at ACT the Mast is not actually best placed or line of sight with the receiver and in other circumstance would not be considered at first instance to serve the geographical area? The receiver under these conditions could be placed in an entirely different geographical area simply from summarising the Mast details shown in the mobile call records.
iii) When call setup (OACSU) takes place and a connection made it could be possible a mobile ‘phone starts a connection for less than a second on the Mast at ACT but forced into hard handover immediately thereafter thus shifts the call to another Mast (say, NC4)? It could be possible the Mast at ACT is shown as the Mast in the call records, which could be rather misleading when attempting to consider geographical location of the mobile telephone when compared to a particular mobile call.
iv) How can the radio examiner, from looking at historical records, correspond radio test measurements against the outward set of event elements recorded in call records? Non-dominance may mean a series of calls being made at one location handled by numerous Masts – thus may amount to a suggestion from analysis of the Masts usage from the call records that the mobile is on the move when in fact it is rather confined to an area. Non-dominance may result in a high number of short duration mobile calls shown in the call records. The short duration calls may not be due to the user terminating the calls, but rather the network dropping the calls.
I introduced, I believe, GSM non-dominance as an important radio anomaly to be considered regarding evidence of radio test measurements into the first criminal case in the UK back in 2003 at the Central Criminal Court (Old Bailey). GSM non-dominance was identified and shown in my evidence. Three other experts appearing for the prosecution or other defendants received my report. Acceptance of my results and findings were agreed and no challenges were made. However, I should point out that the discovery that non-dominance can occur for radio coverage was not my invention but arose from radio propagation studies by mobile network radio engineers endeavouring to agree anomalies for radio principles. The non-dominance principle had already been adopted for the Tetra standards and is accepted in GSM radio parlances as a noteworthy event. Therefore, I was fairly well armed with other independent findings.
The purpose of this discussion thread is to provide yet another example of radio conditions that can prevail when conducting GSM radio test measurements. That simply analysing call records may only present half a picture – a trompe l’oiel ( a lie to the eye) if you will.
Thursday, February 01, 2007
Master Password Unlock
I have received requests for copies of the 2006 supplement edition of Mobile Telephone Evidence (MTE) Newsletter Vol4-MTE-03-2006 supp: 002 regarding Master Password Unlock for Nokia mobile telephones.
http://www.filebucket.net/files/1597_knksh/Handset%20Password%20Unlock.rar