MOBILE FORENSICS AND EVIDENCE DEGREES BSc, MSc and PhD
.
The introduction of academic qualifications (at the levels of BSc, MSc and PhD) in the forensic analysis of mobile devices is, in my opinion, long overdue. The issues presented by wireless technologies are sufficiently different from those related to "traditional" computer forensics that I strongly feel the time has come to address them in greater depth than the forensics community has done to date.
.
A Bit of BackgroundMobile telephone forensics and evidence has not developed overnight but has been developing from the earliest building blocks of scientific discovery back in the nineteenth century. Below are some of the historical developments from which mobile communications has roots in scientific history:
.
1868: James Clerk Maxwell postulates EM wave phenomenon ethereal wind theory
1886: Heinrich Rudolf Hertz establishes proof of EM wave (Hertz cycle)
1893 - Gugliemo Marconi first use of wireless and first patent of wireless communications
1905: Reginald Fessenden first transmission of speech and music via a wireless link
1908: Nathan B. Stubblefield invented and patented the first mobile telephone a 100-years ago
etc
etc
.
Of course, for those who see the above as relevant to devices that took advantage of a waveform that is analogue by nature, should not over look mobile telephones use of digital waveform that has roots, too, in scientific history going back to the early nineteenth century to the work of French physicist Jean Baptiste Joseph Fourier and the method known as Fourier Synthesis and Measurement that was named after him. His method showed mathematically that “
any periodic waveform could be represented as the sum of sine waves with the appropriate maximum amplitudes, frequencies, and phases” (Noll(4)284-ch04). This gave birth to the notion of sine wave being squared off and introduced the notion of Square Wave.
.
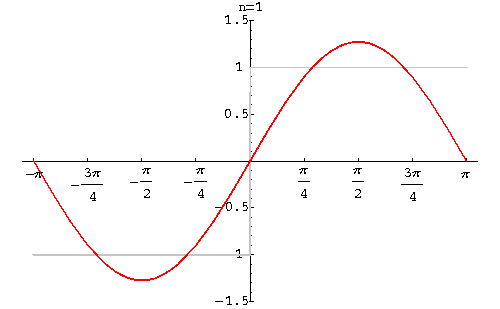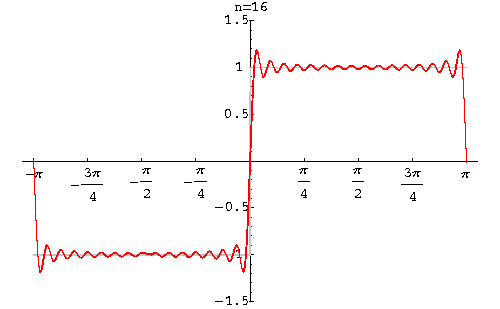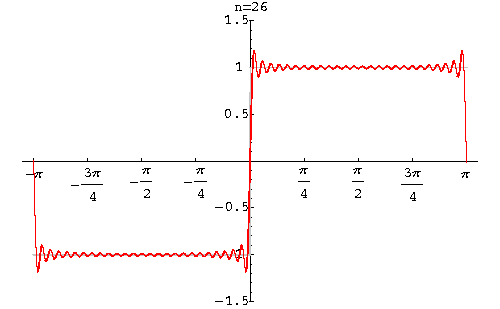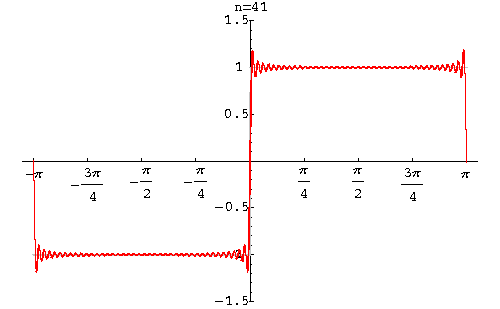
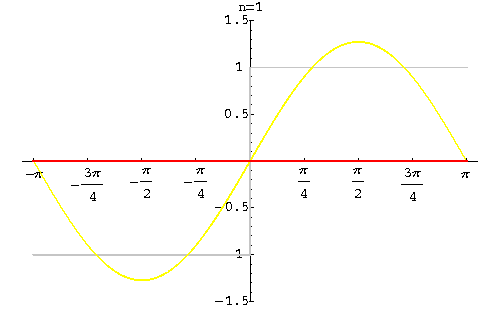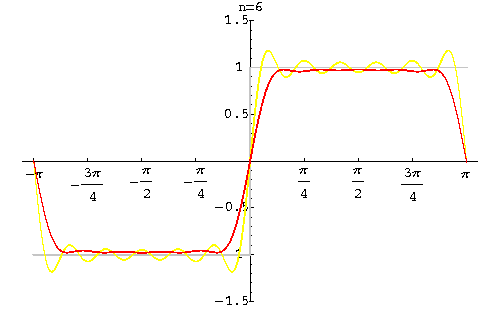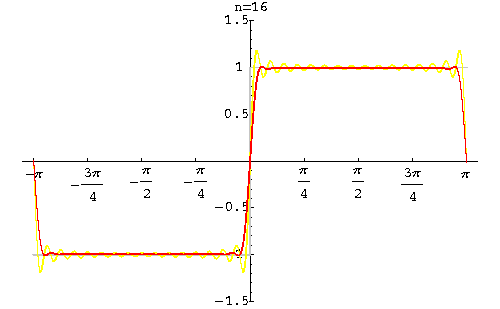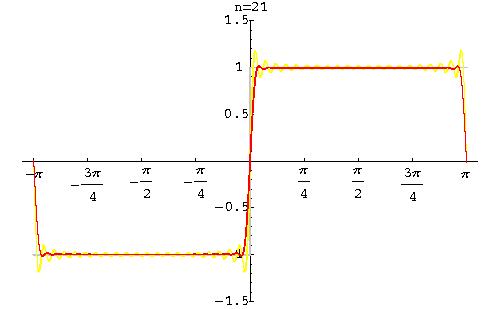
Fourier Theorem - Image 1
.
Fourier’s foundation theorem, set out in Fourier series, was a masterpiece of mathematical calculation but contained a small flaw and that was the square was not perfect at the edges - as first observed by Wilbraham in 1848 as “bumps” at the edges creating a square shape with non-uniformity. Albert Michelson (in 1898) built a machine that calculated Fourier’s coefficients and from his re-synthesized results noted “….wiggles around the discontinuities appeared, and even as the number of Fourier coefficients approached infinity, the wiggles never disappeared” (Radaelli-Sanchez; Baraniuk).
.
In 1899, the phenomenon was first explained by J Willard Gibbs who went on to demonstrate in his mathematical calculations that, in effect, the square wasn’t square at the edges, so to speak, and subsequently his extrapolation of the problem came to be known as Gibbs Phenomenon. The phenomenon can be removed with the Lanczos sigma factor.
.
Lanczos sigma factor applied Image 2
.
There is more to the intriguing discovery above, but for now, if you haven’t guessed, the purpose of discussing square wave is that it is the waveform that can be used to represent positive polarity and negative polarity which can be presented in another format called binary: ones (1) and zeros (0). Binary is a basic building block which is used in digital signalling and communications. The GSM mobile telephone system is a fully digital mobile communication system. Digital signalling and communications are used in GSM handsets and SIM cards.
.
So we can see the link between mobile devices having roots in scientific history, but how does that correlate to digital mobile telephone forensics and evidence today? Well, forensically we need to understand digital communications sent by and received at the handset by understanding the ‘radio DNA bracelet’ and any discovery that can be made from it leading to evidence? Of equal importance is how an examiner gets to this information that provides the building blocks of mobile telephone forensic evidence? Furthermore, we need to know how digital communications occur in the handset and SIM card, as well as how to examine the devices to understand the various formats and coding schemes used for data that are stored, in order to appreciate, once decoded or decrypted, what the content yields as evidence?
.
Policies, practices and procedures combined with examination tools are needed to obtain the evidence above. Some are being developed and some have been developed. I had raised spirits recently when Paul Sanderson of Sanderson Forensics launched his RevEnge and PMExplorer tools, designed to decode and extrapolate the data imaged from particular mobile phones. These tools make the examiner (in an educational way) explore the raw data, define its format and type, and corroborate the information that the data reveals to determine, if the same data were to be read through a mobile phone, would the data be identical?
.
Those of you who know, I worked with Quantaq Solutions' USIM Detective (my details should still be in the help file in USIM Detective) to include forensic aspects to the software and enable analysis of the raw image from GSM and USIM cards, which has proven itself to good effect.
.
I have been quietly partnering with radio test measurement manufacturer Anite (UK division), who produce Nemo Handy, with the specific aims and objectives to produce a 'de facto' standard for cell site analysis. That is because mobile telephones are predominantly wireless telecommunication devices and covered by primary legislation in the UK (e.g. Wireless Telegraphy Act, Telecommunications Act, Communications Act etc). Indeed wireless devices also come under Regulations such as, Telecommunications Terminal Equipment (TTE) Regulations and Radio and Telecommunications Terminal Equipment (R&TTE) Regulations etc. And, equally, as important are the technical standards containing mandatory requirements.
.
So where is this taking all of us in our branch of forensic science? It is taking us towards what I believe are needed and that is BSc, MSc and PhD in Mobile Forensics and Evidence degrees. We should have had these four years ago but have been held back, but the time is now right for degrees specific to our area of work. Importantly, those who have completed modules in Computer Forensic (BSC and MSc) degrees can use those module passes as credits towards one of the Mobile Forensics and Evidence degrees. The feed back from several Universities I have spoken to so far, in the UK, has been positive. It is appreciated QAA will be required for the degrees, showing that the foundation is right and that the Universities can deliver the training.
.
TEST YOUR SKILLS
Do you think you could have sufficient knowledge and experience? To see whether you think you could undertake a Mobile Forensics and Evidence degree at BSc level have a look at the diagram below. It provides a representation of a model about establishing not only past mobile telephone usage but also looking to determine, as far as possible (in time and space), what evidence can be determined about future usage too.
.
Primer
(C now) = Point in time and Space (which is a constant reference point) in the present tense when the examiner is contacted for an investigation and from which the examiner uses to look back at and into the future regarding mobile telephone evidence.
.
(T) = Time is the timeline, limited by how far the examiner can see into the past and future based upon discovery.
.
(S) = Space is the space line that is used as a constant reference point from which all other events occurring in space can be considered based upon discovery (seizure of device, chain of custody of an exhibit etc)
.
(F) = Future relates to things that have yet to happen (future events). This is based upon things that maybe discovered from the time the examiner is contacted
.
(F d) = F d represents, as far as possible, thus not set to a specific period of time, how far into the future the examiner can identify events beyond which no further discovery is possible.
.
(PU usage) = Past User usage (below Blue line represents past recorded events, and below the red dotted line events unfolding during and after investigation)
.
(PR usage) = Past Record usage (below Blue line represents past recorded events, and below the red dotted line events unfolding during and after investigation)
.

Smith Diag 1
.
The proposition in the diagram above (Smith Diag 1) is intended to represent by use of visualization how mobile telephone usage can be investigated. The diagram tests your powers of observation and, more importantly, your depth of knowledge. So do not be fooled by what you believe to be my poor graphics skills. I deliberately intended that (PU usage) area to be shown larger than the (PR usage) area in order to suggest more data may be found in the mobile telephone than maybe obtained from the network records. That is because not all activity on a mobile telephone leads to activity in the radio and fixed mobile network. Network records are not limited to billing records therefore issues associated with cell site analysis also need to be considered. It does not automatically follow there shall be parity between data obtained from the mobile telephone and the network records and vice versa. The diagram below (Smith Diag 2) represents a number of data elements commonly considered during an investigation.
.

Smith Diag 2
.
The third diagram (Smith Diag 3) uses the classic representation of Time (T) and Space (S). Use of a Time line may be obvious but the Space line may not be so obvious. The point of using Space is as a determinate for e.g. the seized exhibit in the examiner's possession. Let's say the examiner receives the mobile telephone exhibit on the 30th March 2008 at 3.00pm. The exhibit was seized 10th March 2008 at 11.00am. So, the examiner has two facts to work with (a) the exhibit in the laboratory (in time and space) and (b) the exhibit seized at a location from premises or person (in time and space).
.
So at the point the examiner has initial Contact (C now), which is a constant reference point, with the exhibit then past events can now start to be determined. By way of illustration, following examination let’s say the examiner finds that the data recovered from the device reveals activity not connected with Space where the mobile telephone was seized at (b). Space would therefore be highly relevant, because (i) the examiner would need to demonstrate that as a fact and (ii) to demonstrate the separation in Space between each of the locations (a) laboratory, (b) the seizure, and the intervening factor between (a) and (b). This may be supported, for instance, by the last location and frequency details stored on the SIM card or may be the handset has GPS or one of the newer mapping system (Nokia Maps etc) that might be set to automatic logging.
.

Smith Diag 3
.
A visualization of this discussion is represented in the diagram above. To distinguish the two events Space lines have been added representing seizure (dashed Black line) and intervening event (dashed Orange line), to the already existing (C now) constant Space line.
.
So the general discussion above should assist in understanding how the model works with past events. But what may be possible to determine in the future, as far as possible, in Time and Space, has not been discussed at all. That question is for the Test that has been set at the end of this discussion.
.
Some points to remember. Not all activity on a mobile phone leads to activity in the radio and fixed mobile network. Network records are not limited to billing records therefore cell site analysis should not be excluded when you are considering this model. It does not automatically follow there shall be parity between data obtained from the mobile telephone and the network records and vice versa. Do remember a mobile telephone is a common term; Mobile Station (MS) is the correct term, meaning a GSM mobile equipment (ME) and SIM card operating together or 3G* Universal Equipment (UE) and USIM card operating together. *In some countries 3G means that the UE and USIM card, as WCDMA devices, may be profiled also with a chipset/module to work in a GSM radio environment.
.
Finally, do remember to look carefully at the diagram as your powers of observation are also being tested.
.
The Test
This test is open to individuals, companies, forensic firms and University students.
.
Discuss, supported by equations if necessary, to either prove or disprove whether the model is correct at first instance.
.
If you do not believe the Diagram is correct then submit a diagram that you have designed to represents the past and future mobile telephone usage.
.
Identifying, using the above diagram, what events in Time and Space you think an examiner might be able to determine about future usage of a handset and SIM card following examination of them. It may assist if I provide some clues when discussing future events.
.
- Remember that radio signals travel at the speed of light and you may wish to consider whether a 2W mobile telephone or less than 2W could generate radio signals propagated at that speed.
- International time zones vis-à-vis international boundaries
- Proactive SIM
- Calendar/Alarm
- Battery
- Subscription
- Also, think along the lines of kidnap cases and death cases
.
The correct responses that have been emailed to me in acrobat .pdf format will be published here at the blog and at Forensic Focus:
.
.
Please remember to identify who you are in your document so that the author gets the recognition for their work. The Test closes 27th March 2009. From your submitted paper to me, which will be reviewed by a Board of Assessors, you will be able to know from your marked paper whether you have sufficient skillsets to undertake a BSc Mobile Forensics and Evidence degree.
.
Good luck



 Smith Diag 2
Smith Diag 2 Smith Diag 3
Smith Diag 3

